Microsoft licensing is tough and vague but something we must deal with while implementing our solutions. I’m also aware that some of the features I describe on my blog are only available in the most expensive licensing options Microsoft provides, making some of the features I describe not usable for some of my readers.
Update June 23rd 2020: Microsoft has removed the Intune license requirement for administrators, see this blogpost by Peter van der Woude for more information: Quick tip: Allow access to unlicensed admins
If you administer Microsoft 365 services like Azure Active Directory (AzureAD), Exchange Online (EXO), SharePoint Online (SPO), Intune and many other products the license requirements for your administrative accounts are extra vague. I’ve asked Microsoft in December last year to clarify this, but until now no response was given.
There is some fragmented information available in the Microsoft documentation, that in combination with some other information to be found on the internet, like on twitter concludes that the license requirements are indeed very vague and could really use some official documentation from Microsoft to clear things up.
One thing in known, is that when asked about licensing requirements for the online services provided by Microsoft the statement returned is: “When the user benefits from the service, a license is required”
So let’s see what I found available online and see if it makes sense in some way…
Disclaimer: I don’t consider myself a Microsoft licensing expert and you therefore shouldn’t take anything I write here as being the truth from a licensing perspective. If you are in doubt, consult your licensing partner. This article was written on March 2nd 2020 and reflects the status of that point in time.
Azure Active Directory
Azure Active Directory comes in four editions—Free, Office 365 apps, Premium P1, and Premium P2 as detailed on the Azure Active Directory pricing page. Free has the lesser options while Premium P2 provides all the possible options.
When you buy one license for Azure AD Premium P2, either individually or as part of a suite license like M365 E5 or EMS E5 your whole Azure AD tenant will be put in Premium P2 mode, unlocking all of its capabilities.
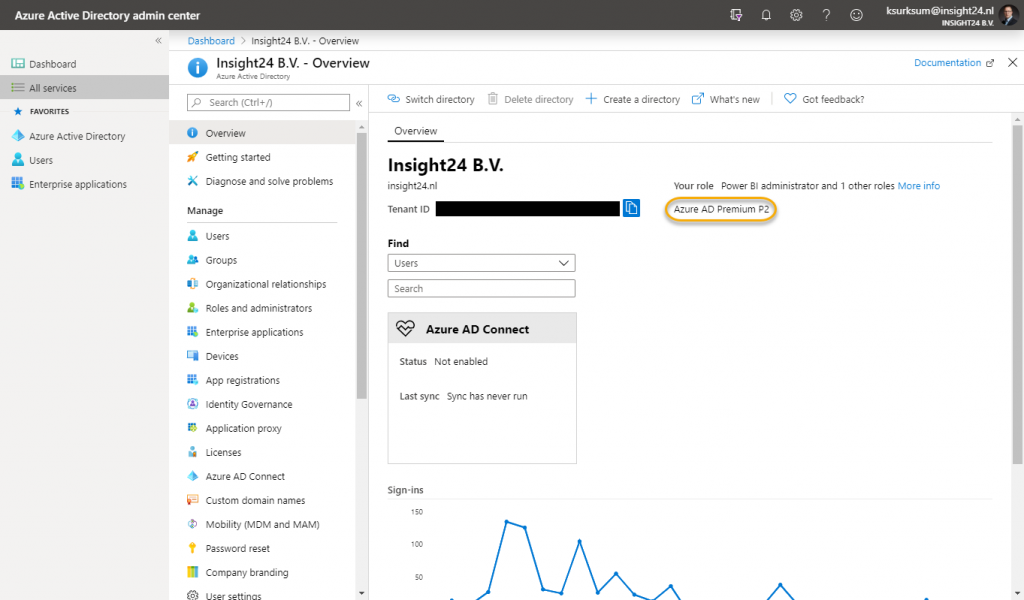
That doesn’t mean though that you are entitled to use the Azure AD Premium P2 functionality for all your users, since the statement is, that if you benefit from the service, you need to buy a license.
Microsoft also makes a remark about this on their Microsoft 365 licensing guidance for security & compliance documentation page, stating “Some tenant services are not currently capable of limiting benefits to specific users. Efforts should be taken to limit the service benefits to licensed users. This will help avoid potential service disruption to your organization once targeting capabilities are available.“

Actually the Microsoft 365 licensing guidance for security & compliance documentation page gives us some more clues about the licenses needed for administrative accounts per feature. Take for example Azure Active Directory Identity Protection.
From the documentation page: How do users benefit from the service?
SecOps analysts and security professionals benefit from having consolidated views of flagged users and risk events based on machine learning algorithms. End users benefit from the automatic protection provided through risk-based Conditional Access and the improved security provided by acting on vulnerabilities.
Conclusion: So, based on this answer we can safely say that if your SecOps analyst and security professionals use an administrative account when they use consolidated views of flagged users and risk events that they must be licensed for Azure AD Premium P2.
Ok, that makes sense… and when it comes to some other examples as well like for example when using Azure AD Privileged Identity Management (PIM) – when you want to implement PIM for your administrative accounts, those accounts must be licensed.
It already becomes vague when looking at Microsoft Cloud App Security, here the documentation provides the following information:
Which users benefit from the service?
Licensed users of MCAS, Enterprise Mobility + Security E5/A5/G5, Microsoft 365 E5/A5/G5, and Microsoft 365 E5/A5/G5 Security can benefit from MCAS.
Licensed users of Azure AD P1 can benefit from the Discovery capabilities in MCAS.
To benefit from the Conditional Access App Control capabilities in MCAS, users must also be licensed for Azure Active Directory P1, which is included in Enterprise Mobility + Security E3/A3/G3, Enterprise Mobility + Security E5/A5/G5, Microsoft 365 E3/A3/G3, Microsoft 365 E5/A5/G5, and Microsoft 365 E5/A5/G5 Security.
To benefit from automatic labeling, users must be licensed for Azure Information Protection P2, which is included in Enterprise Mobility + Security E5/A5/G5, Microsoft 365 E5/A5/G5, and Microsoft 365 E5/A5/G5 Compliance.
For more information, see the Microsoft Cloud App Security Licensing Datasheet.
How do users benefit from the service?
MCAS discovers and assesses Shadow IT, provides threat protection across first- and third-party cloud apps, and protects information across first- and third-party cloud apps.
Conclusion: So, it’s clear that both users and administrators benefit from MCAS, but what’s not clear if administrative accounts should be licensed for Azure AD Premium P1 or Azure AD Premium P2 in order to administer MCAS. So overall we can conclude that it’s probably best to license your administrative accounts with Azure AD Premium P2 if that account benefits from any of the Premium P2 functionality.
But wait there is more…..
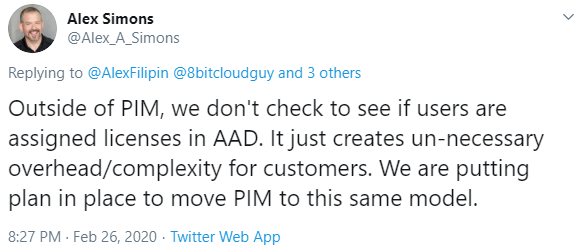
Last week I was triggered by a tweet from Tobias Zuegel (@MrAzureAD), who asked the following question:
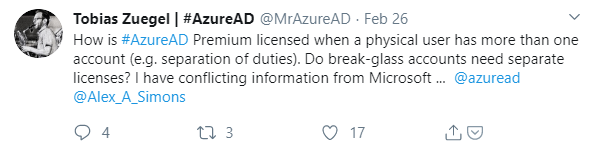
The thread which followed was actually very interesting to read, since it was answered by Alex Simons (@Alex_A_Simons) as well, who is Corporate Vice President PM, Microsoft Identity Division.
Tobias replies with mentioned that he has a written statement, stating that Azure AD Premium P1 and P2 are licensed per user and not per account, which was later confirmed by Alex Simons.
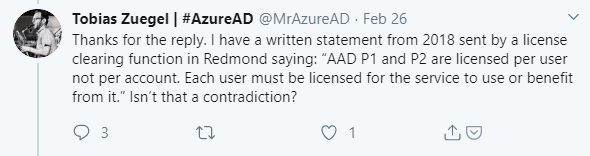
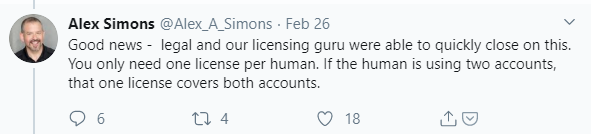
Conclusion: If you have a normal account licensed for Azure AD Premium P2, your administrative account can also use the Azure AD Premium P2 functionality and be compliant with licensing requirements.
So does this mean that you don’t have to add a license to your administrative accounts?
Not really at the moment, for example when you want to make use of Azure AD Privileged Identity Management (PIM), the user which is managed by PIM must have a license or else the functionality won’t work. Alex Simons commented on that that Microsoft is working on removing that requirement though.
How about other products, like Microsoft Intune and Exchange Online?
While for Azure Active Directory we at least now how someone with authority with Microsoft sees it, for other products within the Microsoft 365 suite it’s not that clear, let’s have a look at Microsoft Intune and Exchange Online
Microsoft Intune
For Intune I haven’t found any information on the Microsoft 365 licensing guidance for security & compliance documentation page. There is some licensing information on the Microsoft Intune licensing documentation page though stating:
The appropriate Microsoft Intune license is required if a user or device benefits directly or indirectly from the Microsoft Intune service, including access to the Microsoft Intune service through a Microsoft API.
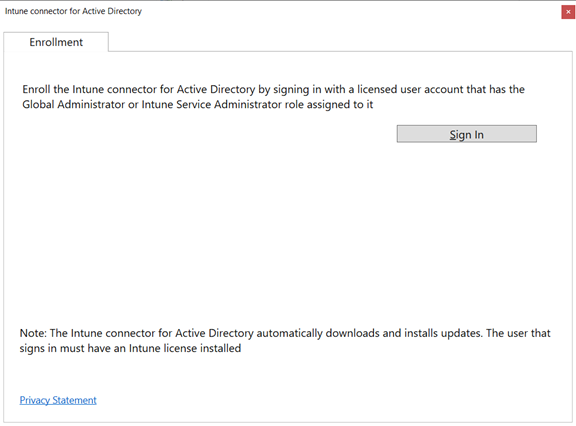
I’ve also found some other License requirements when it comes to Microsoft Intune while working with the product, for example while installing the Intune Connector for Active Directory the installation wizard provides the following text:
Note: The Intune connector for Active Directory automatically downloads and installs updates. The user that signs in must have an Intune license installed.
Conclusion: If you are currently administering Microsoft Intune, you must be licensed, even though in practical terms I haven’t experienced any issues while administering Intune using a non-licensed account in my test enviroment. Also any user accessing the Microsoft Intune service using the Microsoft API must be licensed.
Exchange Online
With Exchange Online I didn’t experience any issues when administering the service in my test tenant using a non-licensed administrative account. The Microsoft 365 licensing guidance for security & compliance documentation page raises some questions though, take for example Office 365 Advanced eDiscovery:
How do users benefit from the service?
A user benefits from Advanced eDiscovery when the user is selected as a data custodian (a person having administrative control of a document or electronic file) for a case.
How is the service provisioned/deployed?
By default, Advanced eDiscovery features are enabled at the tenant level for all users within the tenant when admins assign eDiscovery permissions in the Security & Compliance Center.
Conclusion: If you are a data custodian in a Advanced eDiscovery case, you must be licensed for the Advanced eDiscovery
Conclusion
I hope this article sheds some light on the complexity involved when it comes to licensing your administrative accounts. Personally I really hope Microsoft will make some changes to their products and unifies the statement that a human must be licensed instead of an account. That human, if having administrative rights and a separate administrative account can then have both a normal licensed account and an administrative “non-licensed” account to do his/her work.
This will make our life as Modern Workplace designers and implementers so much easier in my opinion.
Please, do not give your normal user account administrative rights because of this conclusion so that you know for sure that you are properly licensed. Even when using PIM and giving a lifetime to the administrative rights, this opens the account for compromise.. For example, what happens if a user (who is temporary Global Administrator) via PIM opens an email with a malicious link..
Hopefully this article will trigger someone within Microsoft to clear up this confusion, if so I will update this article of course.
Has any progress been made on removing the license check from PIM? I’ve found no further information, and Alex Simons doesn’t seem interested in responding.
Hi Pete,
I haven’t seen any update related to PIM where this check is removed unfortunately. I don’t see anything on the roadmap either: https://www.microsoft.com/en-us/microsoft-365/roadmap?filters=Azure%20Active%20Directory#owRoadmapMainContent
Guess we have to be patient….
/Kenneth
Thanks Kenneth. The answer we finally got back from Microsoft’s licensing group is essentially “we have no idea what you’re talking about. Here’s the licenses you need to buy for your admin accounts”. I rarely use Twitter so maybe I missed it, but it looks like the conversation with Alex Simons you reference no longer exists on his account. I wonder if he’s had to backtrack. I would think it would have been mentioned somewhere else in the last 15 months if it was still going to happen.
Thank you Kenneth for the information, very helpful and informative.
Dear Kenneth,
I liked your article a lot so I wanted to contribute. Maybe something has changed since 2020 because in this link https://learn.microsoft.com/en-us/microsoft-365/enterprise/subscriptions-licenses-accounts-and-tenants-for-microsoft-cloud-offerings?view=o365-worldwide I can find the following note from MS:
“A security best practice is to use separate user accounts that are assigned specific roles for administrative functions. These dedicated administrator accounts do not need to be assigned a license for the cloud services that they administer. For example, a SharePoint administrator account does not need to be assigned a Microsoft 365 license.”
Therefore, it seems straightforward now, at least in theory.