In this blogpost I will share my experiences with implementing Azure AD Privileged Identity Management (PIM). PIM is a service that enables you to manage, control, and monitor access to important resources in your Azure environment. These resources include resources in Azure AD, Azure, and other Microsoft Online Services like Exchange Online, SharePoint Online or Microsoft Intune.
PIM provides the following functionality:
- Just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
This article will cover the following topics:
- Securing Privileged Access
- Licensing
- Accessing PIM
- Rights needed
- How to request rights using PIM
- How to configure PIM as a Privileged Role Administrator
- Adding users as Eligible to Azure AD Roles
- Modifying default role settings
- How to approve requests for administrative rights
- Reviewing all given access using Resource Audit
- Azure Resources
- Access Reviews
- Alerts
- Caveats and challenges
- Conclusion
- References
Note: This post reflects the status of Azure AD Privileged Identity Management as of March 24th 2020. Functionality may change, even right after this post has been published.
Securing Privileged Access
Implementing PIM should be part of a wider ranges of actions as described in the following Microsoft Docs article: Securing privileged access for hybrid and cloud deployments in Azure AD, cause besides implementing PIM you should also create emergency accounts, enable MFA, reduce the amount of people holding high privilege roles, implement regular access reviews and much more. Have a look at the documentation, it provides a 4 phased approach and must be part of your implementation.

Licensing
In order to use PIM, the account which benefits from the service (your Admin accounts) must be licensed for Azure AD Premium P2 (or any suite license having P2 on board) which has a list pricing of € 7,59 per user per month, see my other article titled: License requirements for administering Microsoft 365 services for some more context on that subject.

Accessing PIM
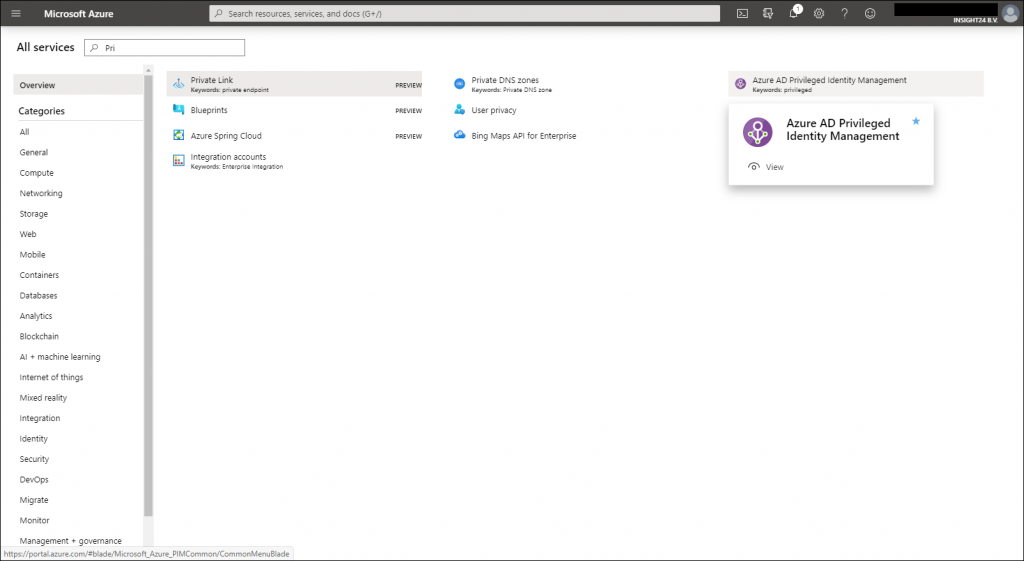
Azure AD PIM is available via the Azure Portal (but also via the Azure AD admin center), you can search for it under All services, type in the first letters in this example “Pri” and Azure AD Privileged Identity Management should already be available in the list. If you hover over it, you can select the “star” which makes PIM available in the hamburger menu of your Azure portal page.
Rights needed
The first user enabling PIM will also receive the “Privileged Role Administrator” role, if you want to configure anything in PIM, being a Global Administrator is not sufficient, you’ll need the Privileged Role Administrator rights. Microsoft also mentions that the first account enabling PIM will receive the Security Administrator role, but I have no idea what the purpose of that would be. I successfully tested and was able to execute all tasks being a “Privileged Role Administrator” only.
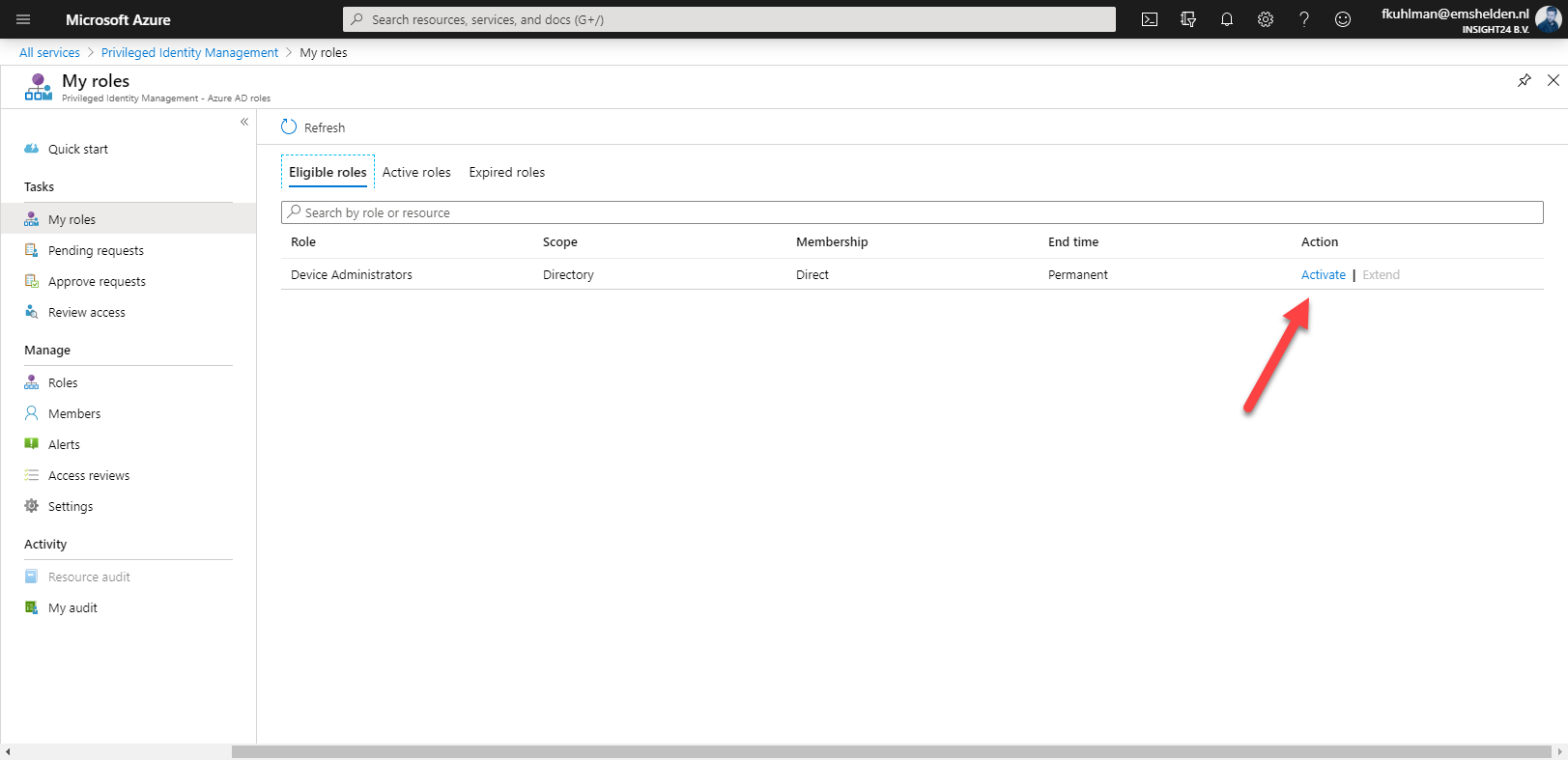
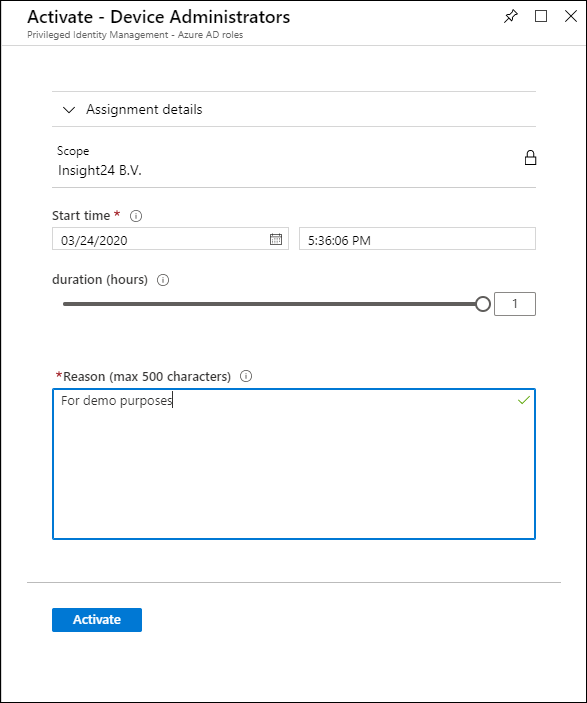
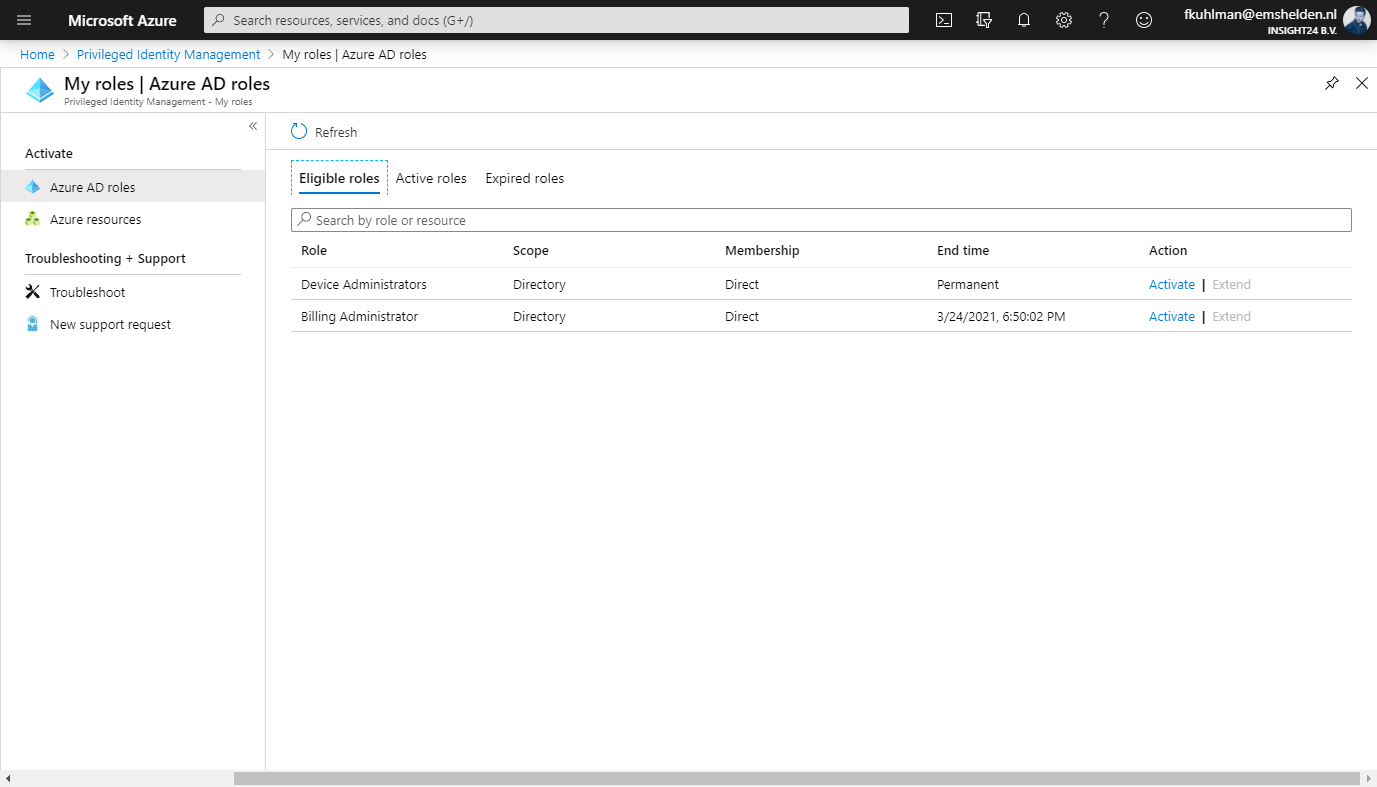
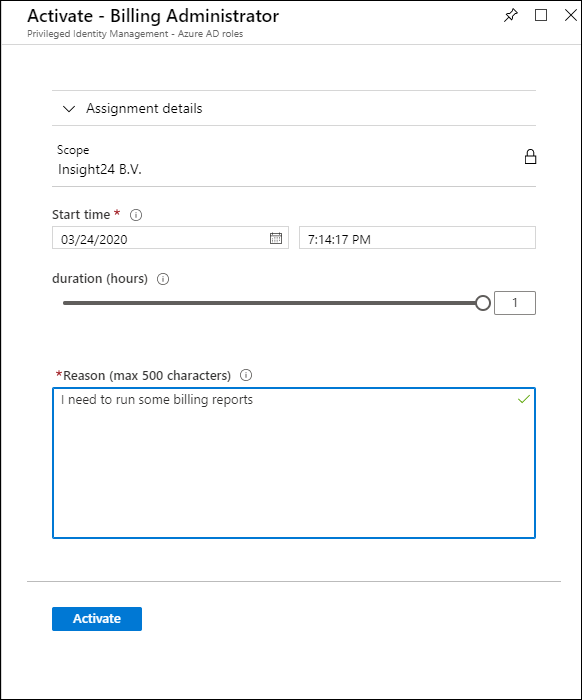
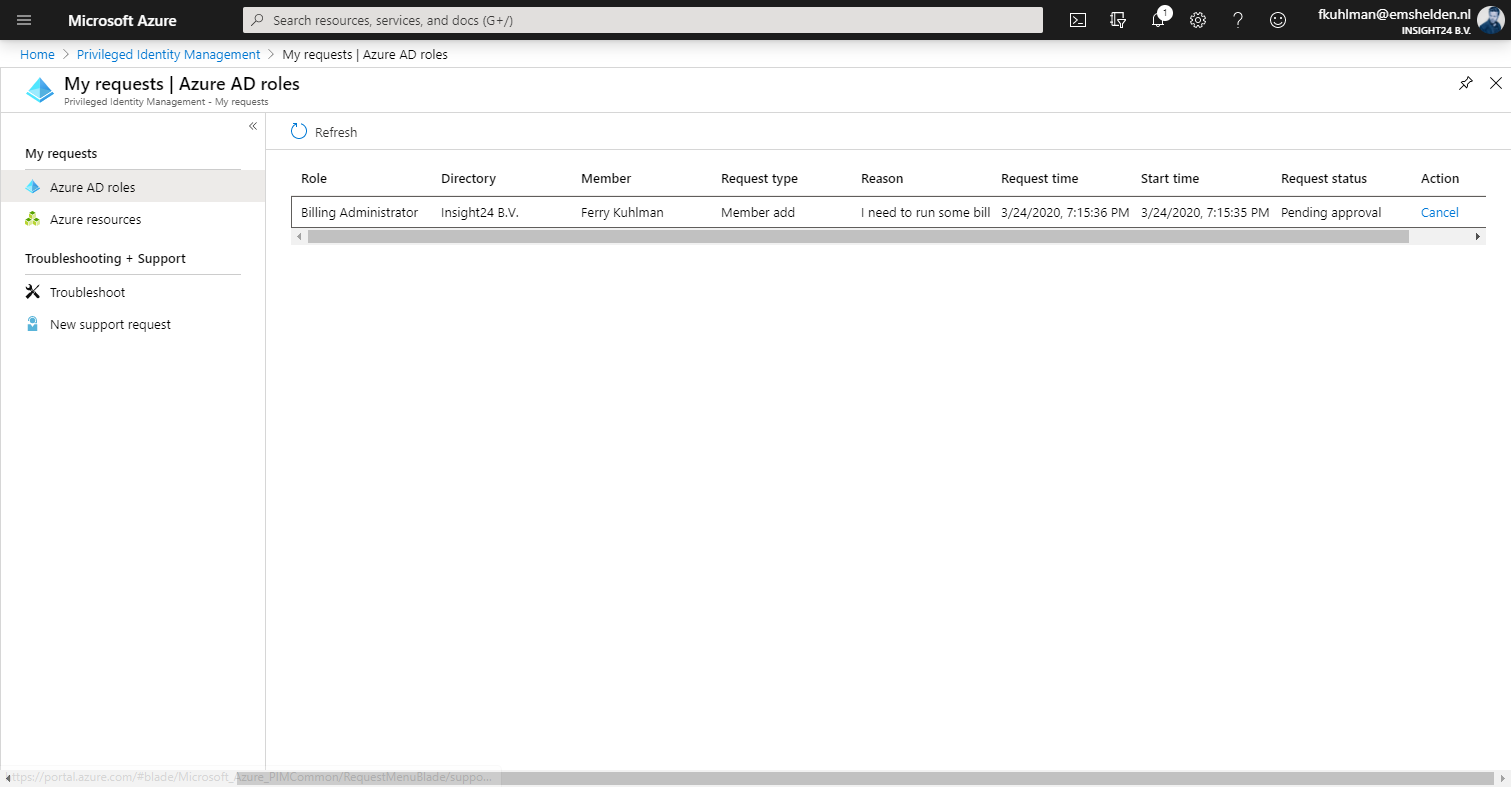
How to request rights using PIM
An user accessing PIM can request to activate roles for which “eligibility” has been defined by a Privileged Role Administrator, how to do this will be described later in this post. In the example below we are going to request the Device Administrator rights. (which is actually a bad example, more on that later)
The Microsoft best practice is only perform administrative duties on a so called “Privileged Access Workstation” also known as PAWs, see also Microsoft Cybersecurity Reference Architecture. For companies which do not have this implemented yet, it becomes tricky – let me explain why:
Most of the time, we use the so called “Manage People” or “Profiles” functionality provided by Modern browsers like Google Chrome or the new Microsoft Edge. Some users like to start their browser session for administrative purposes using InPrivate browsing.
You might have noticed the following behavior: If you work with the profile functionality in your default browser and open a link from an email, that link is opened in the last activated browser instance used. So, hypothetically if an user with administrative credentials logged in under his/her normal credentials receives a malicious email with a link which opens in a browser session having just received administrative rights, then you might have a serious security issue at your hands.
If you therefore cannot make use of PAWs, I advise to at least use a different browser for your administrative tasks. For example, use the new Edge for your normal browsing and set Edge as the default browser, and use Google Chrome for your administrative tasks.
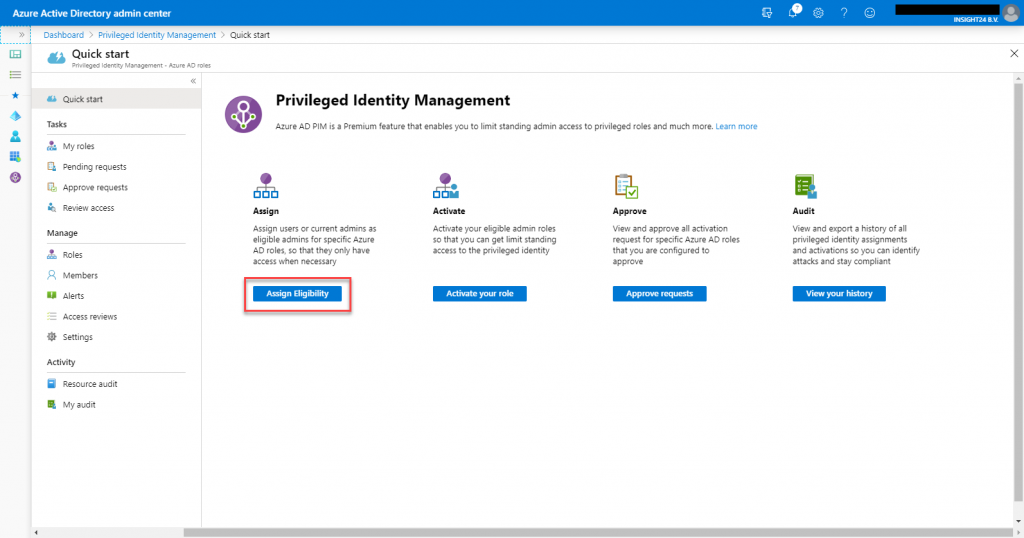
How to configure PIM as a Privileged Role Administrator
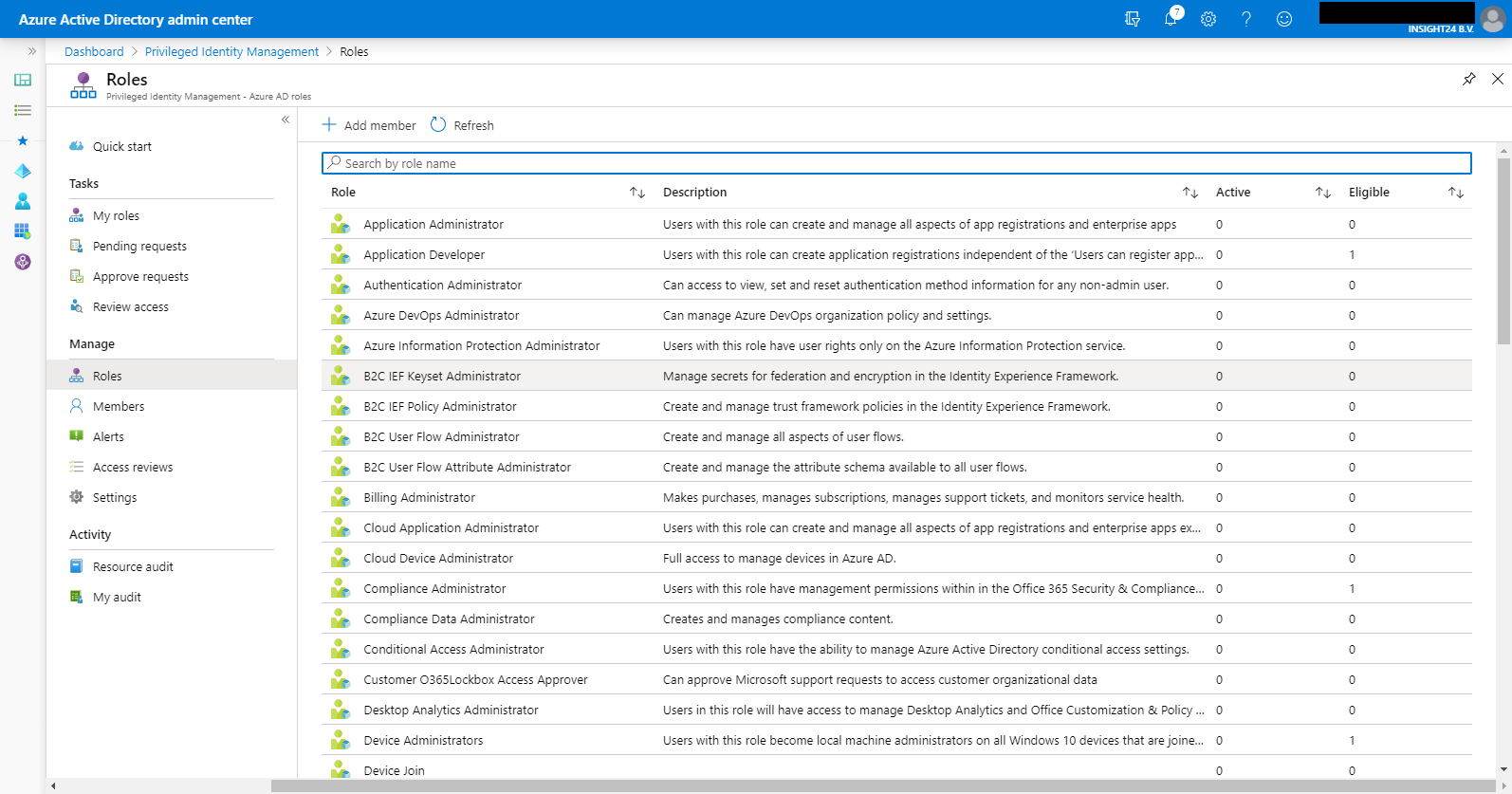
When you have the Privileged Role Administrator role, you’ll notice that the “Assign Eligibility” option is not greyed out – for me personally this is the easiest indication that you can configure the roles within PIM.
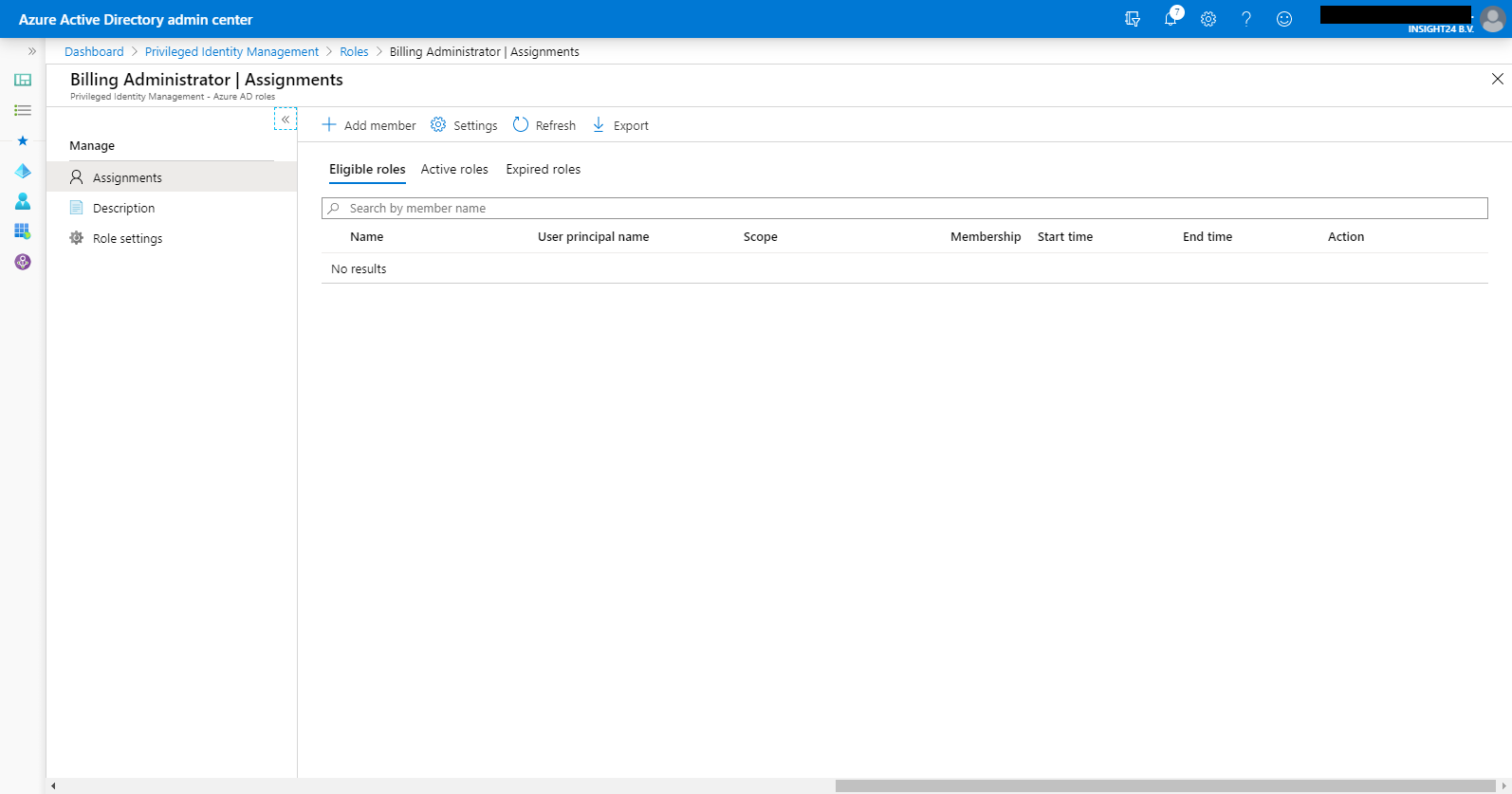
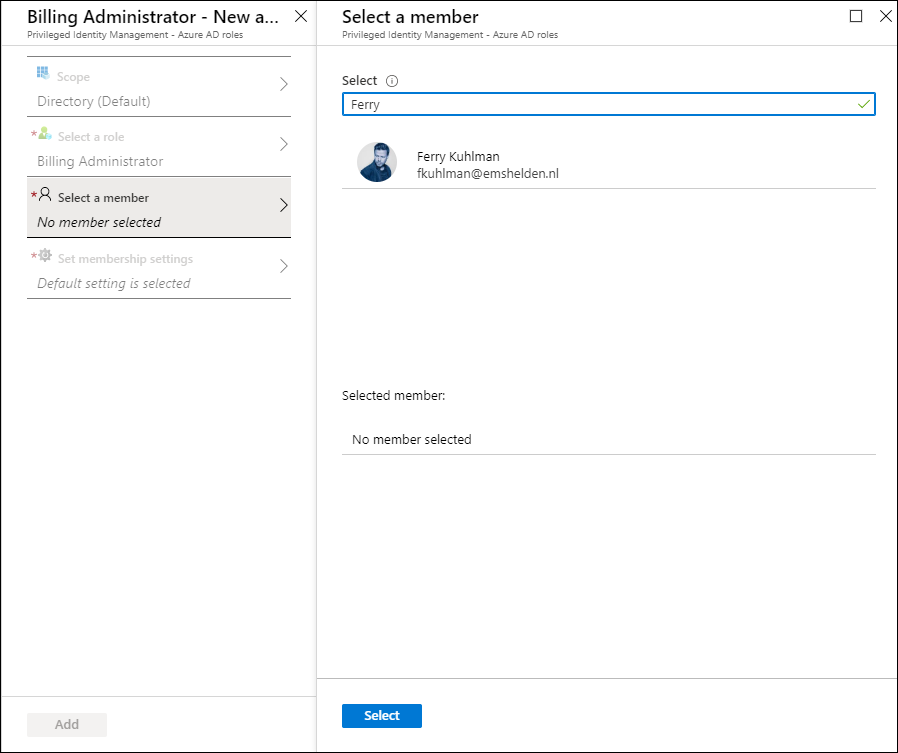
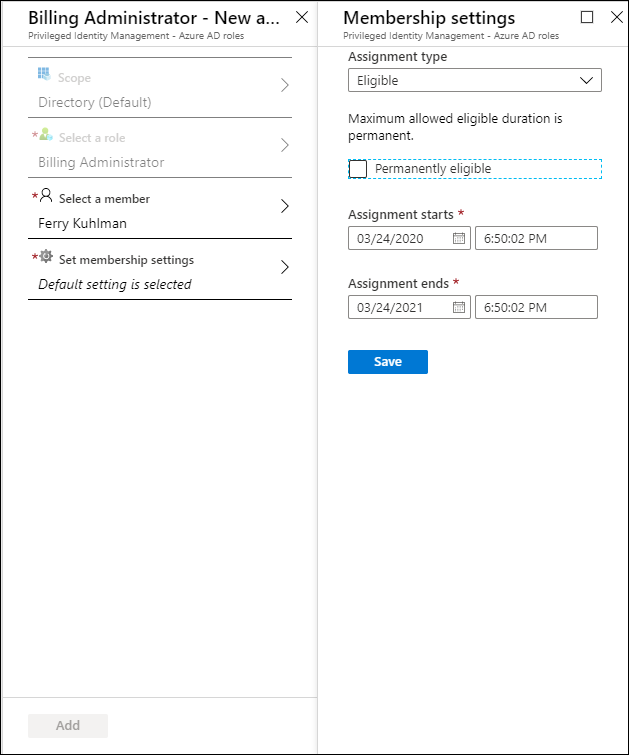
Adding user as Eligible to Azure AD Roles
You can add users to roles using the following example, in this example we are going to add Ferry Kuhlman to the Billing Administrator role
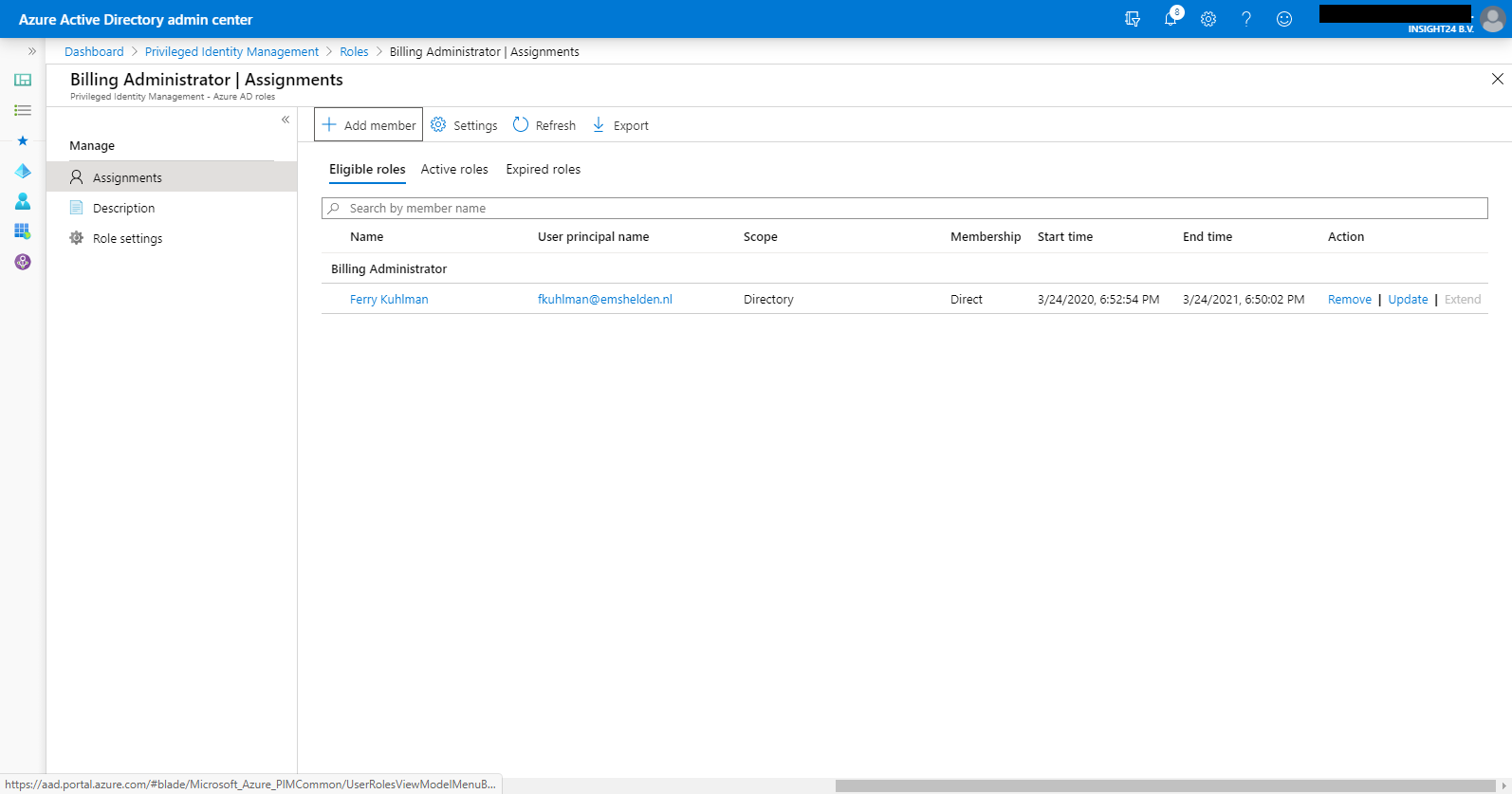
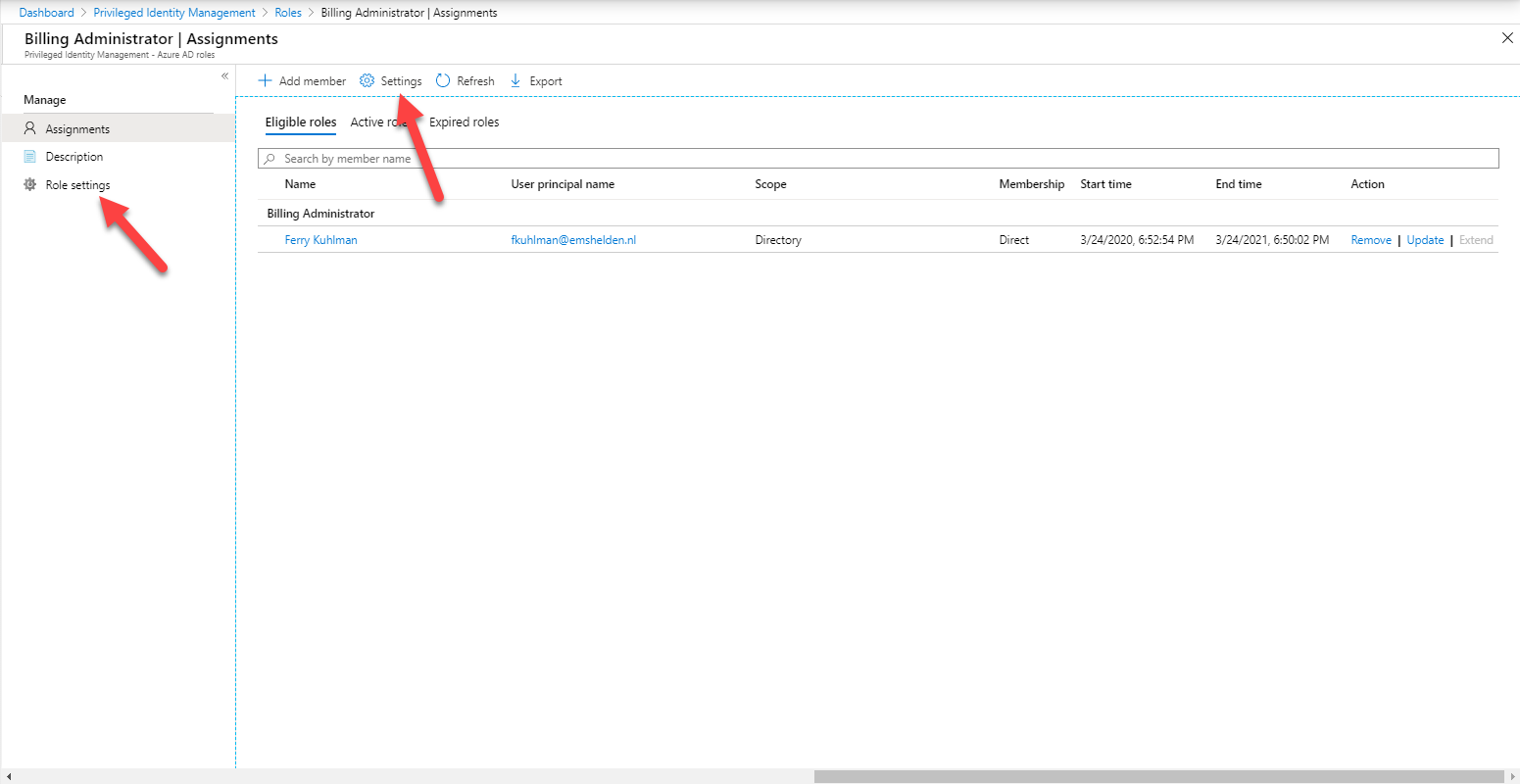
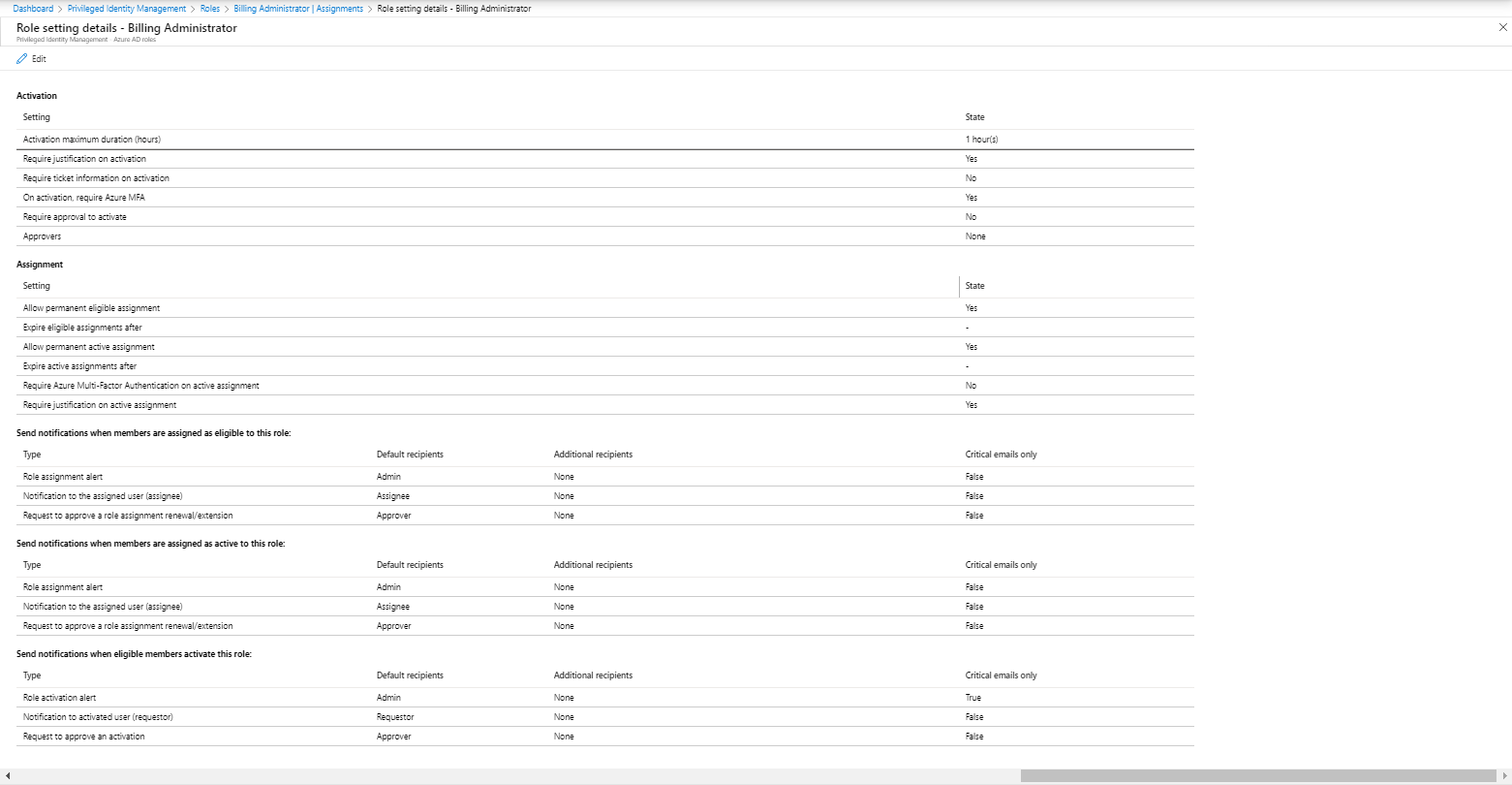
Modifying default role settings
Each role has some default settings, which can be modified individually. You can do this by clicking on either on Settings or on Role Settings, within the selected role. The same settings are accessible via Settings under the Manage section in the main portal.
From here you can make some adjustments for when this role is assigned to a user using PIM, you can modify these default settings by clicking on Edit. This will open the Edit role settings configuration wizard.
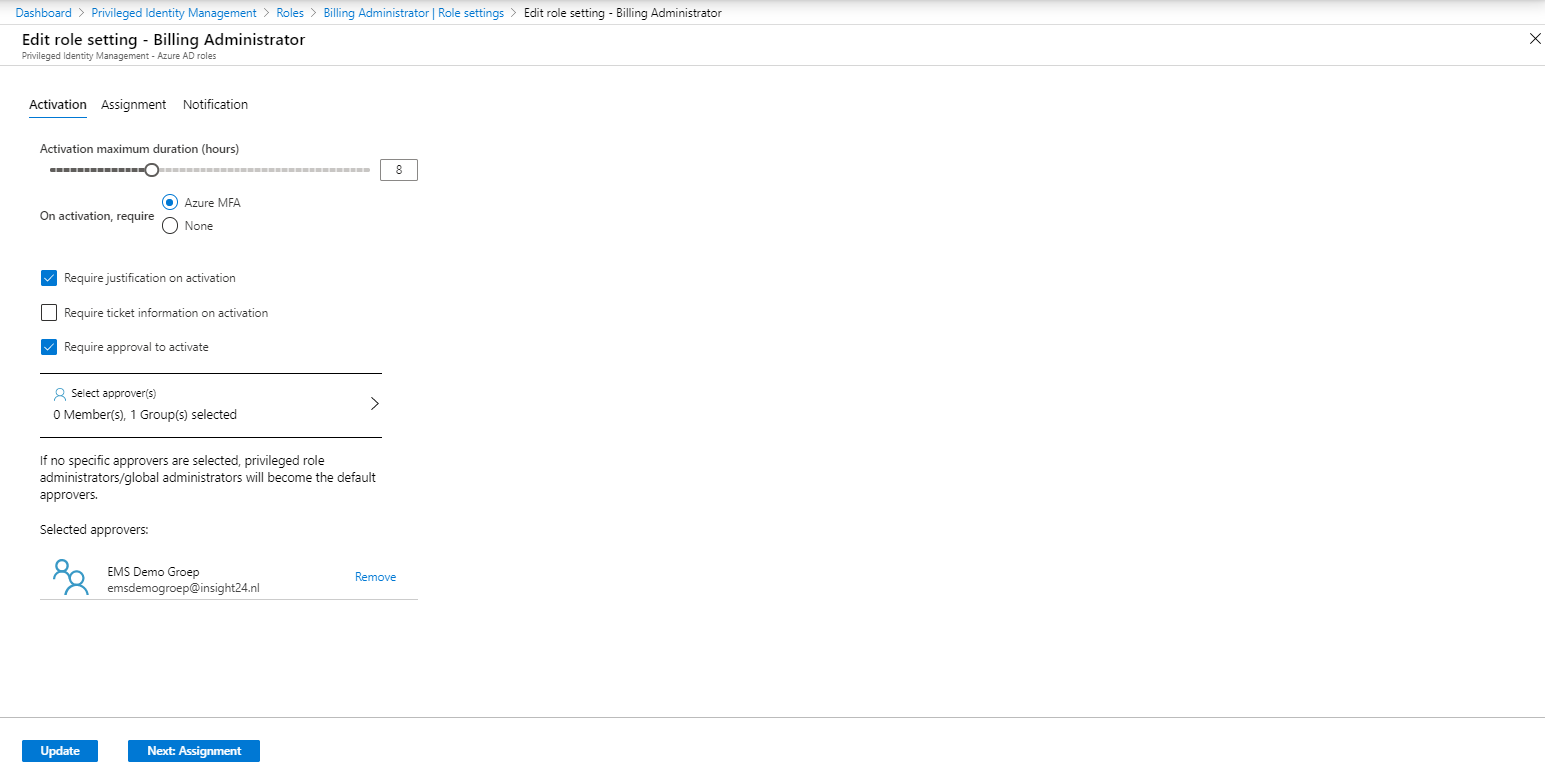
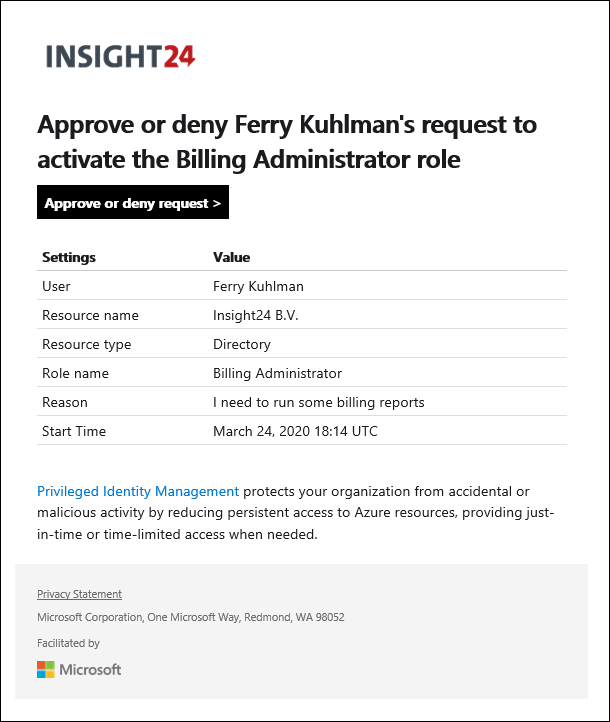
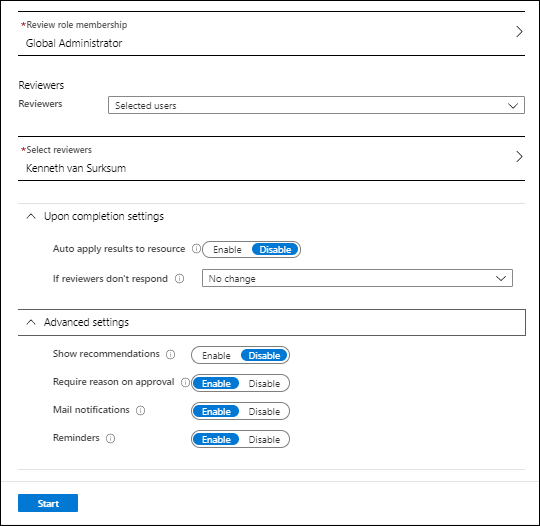
The Edit role settings are provided in a tabbed wizard. The first tab provides settings for Activation of the role, here you can define the maximum duration of the activation, whether MFA is required for activation of the role, whether the activation must be justified, ticket information must be added and if the request must be approved. If so, here you can provide either a user or group who can approve the request.
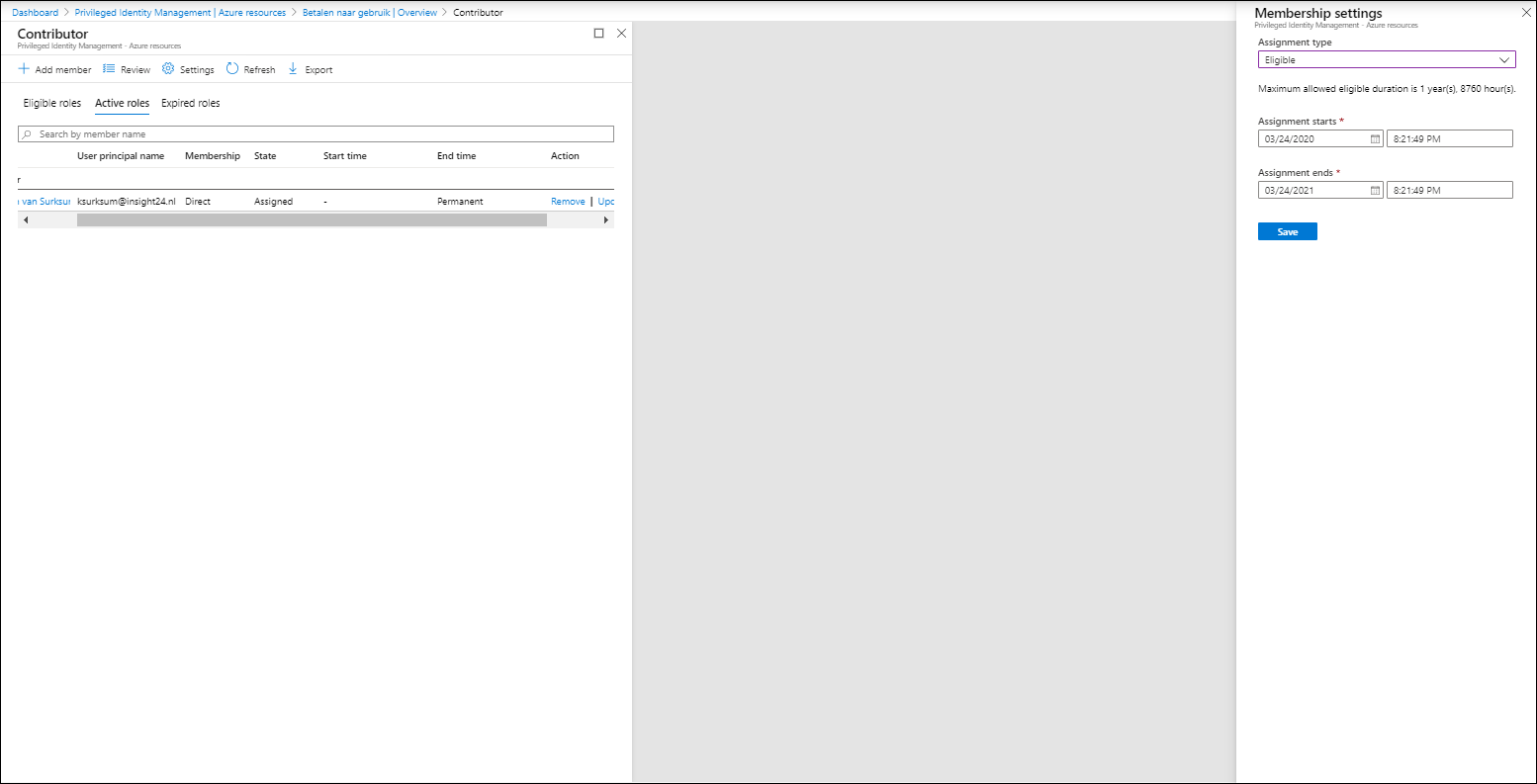
The second tab provides settings for Assignment, here you can define whether the Eligible assignment can be assigned permanently (still get it?) or if each Eligible assignment should expire after a certain timeframe. Whether someone can be assigned permanently to the role (so the role is always active), and if that assignment expires whether or not. It’s also possible to require MFA when active assignments are being activated, and if justification for active assignments are needed.
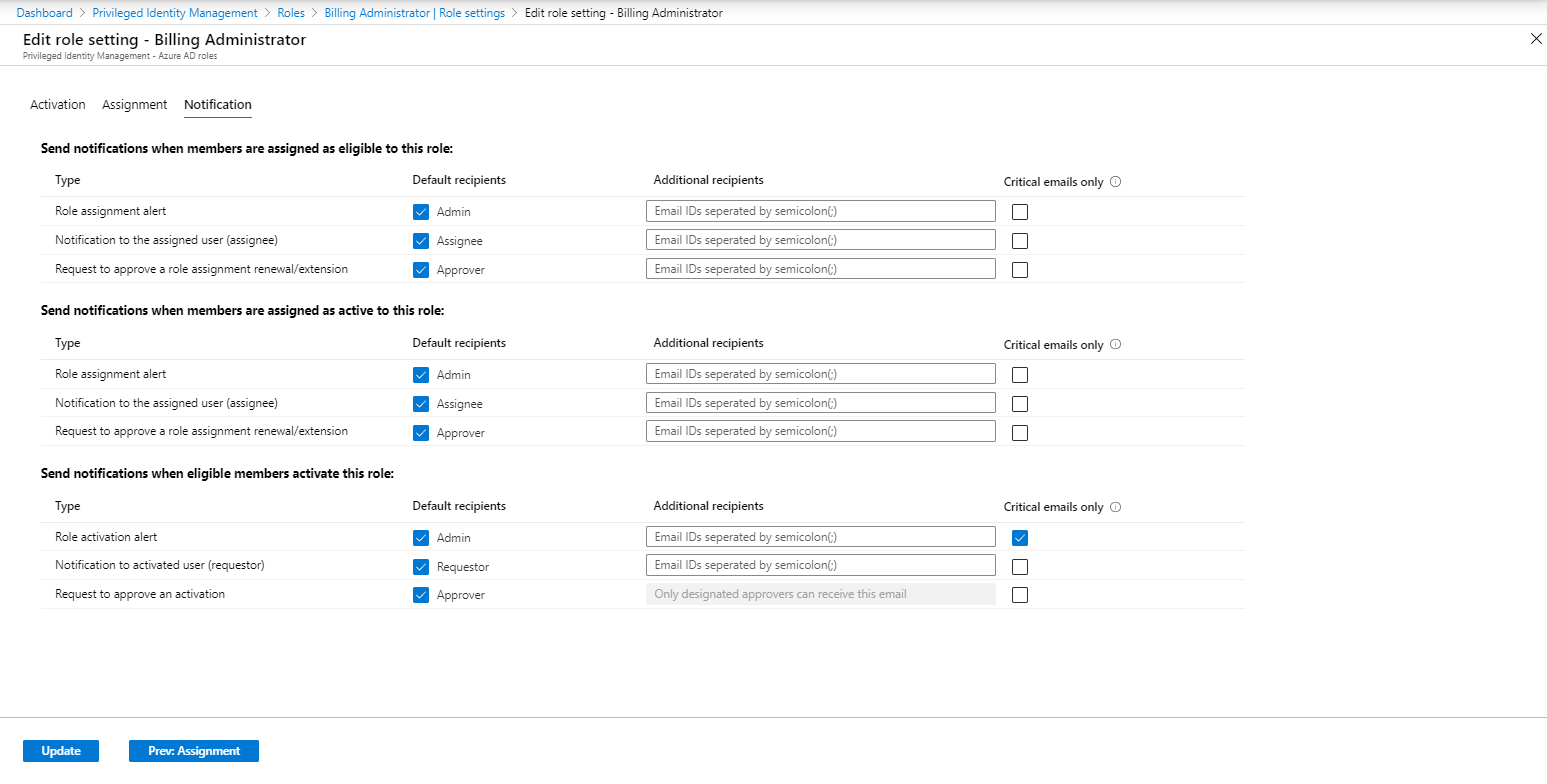
The last tab provides settings for Notification, by default role assignment alerts are send to “Admin”, which translates to everyone having the Global Administrator role either permanent or eligible. When critical emails only is selected PIM only sends out emails requiring an immediate action.
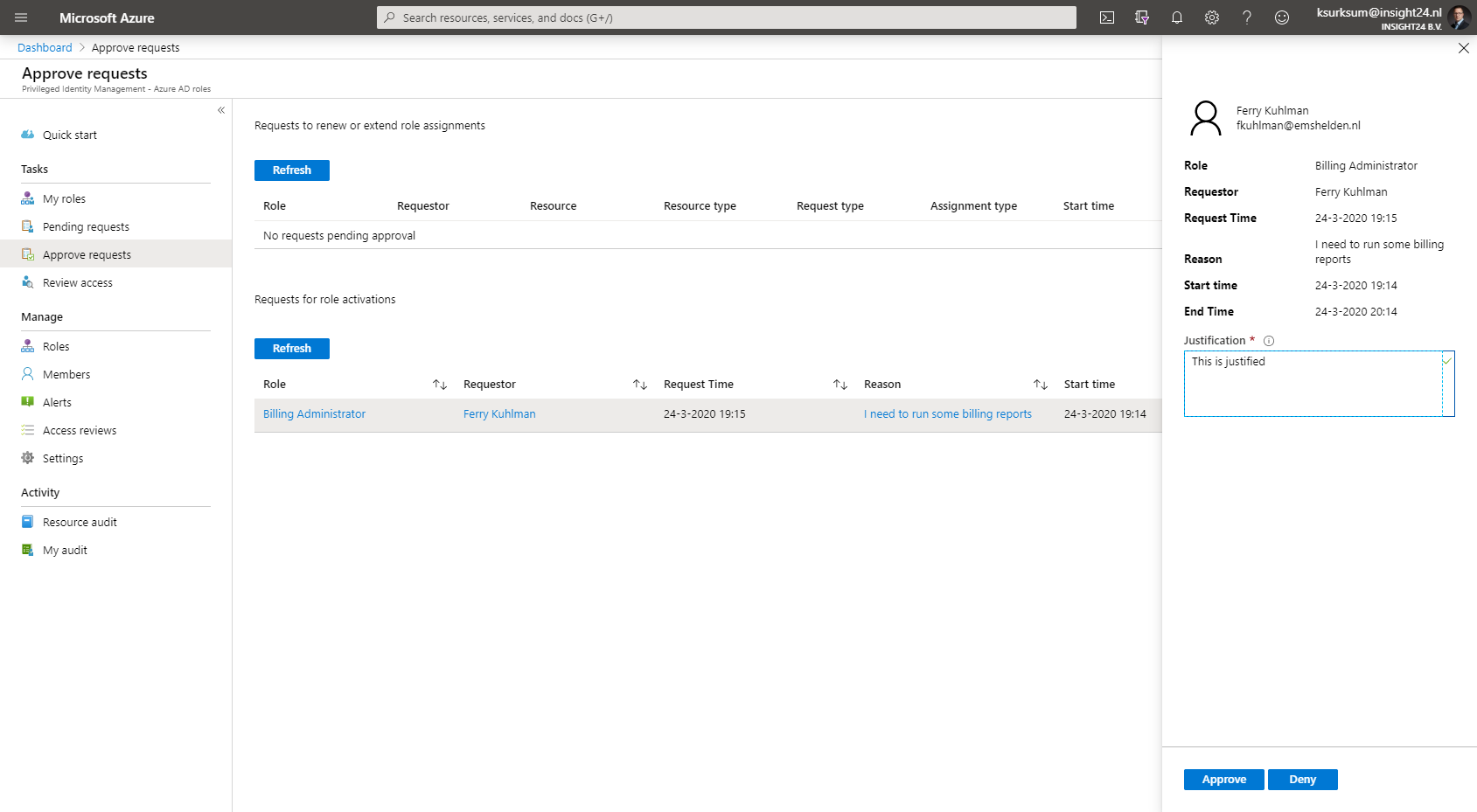
How to approve requests for administrative rights
When approvement of the requested rights is needed, the user requesting the rights fills in the request form as normal. Instead of being activated directly, the request will have the status of Pending approval.
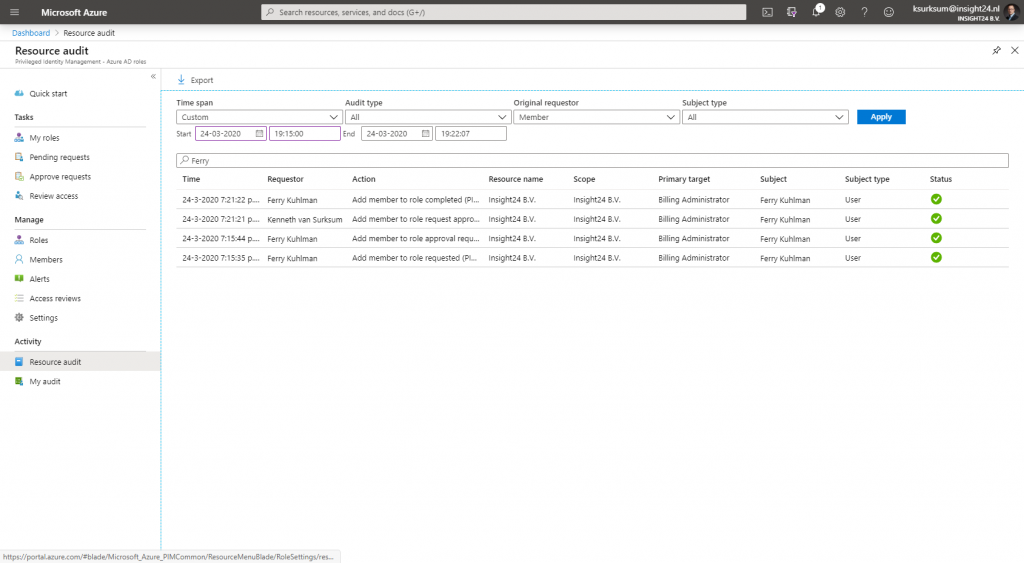
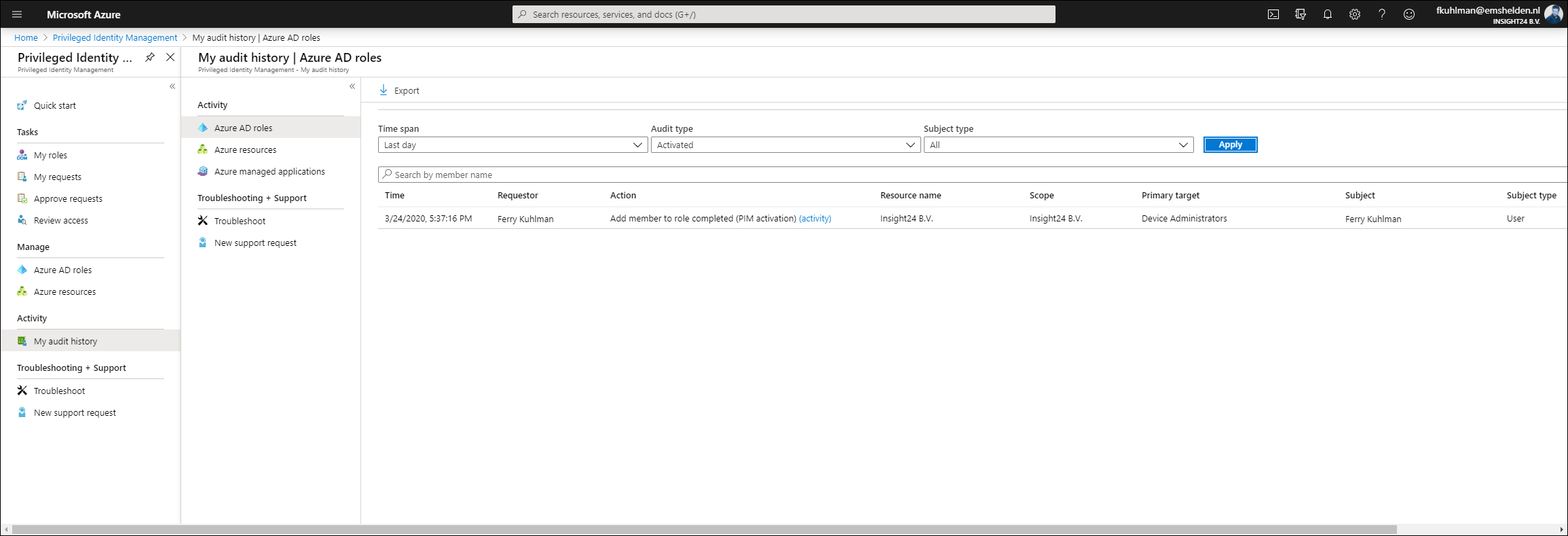
Reviewing all given access using Resource Audit
As a Privileged Role Administrator you can use the Resource Audit functionality to review of the PIM activities, in the example below we filtered on Ferry and provided a very specific timeframe. If you click Export, a .CSV file will be downloaded which then can be used in either Excel, or even better PowerBI
Azure resources
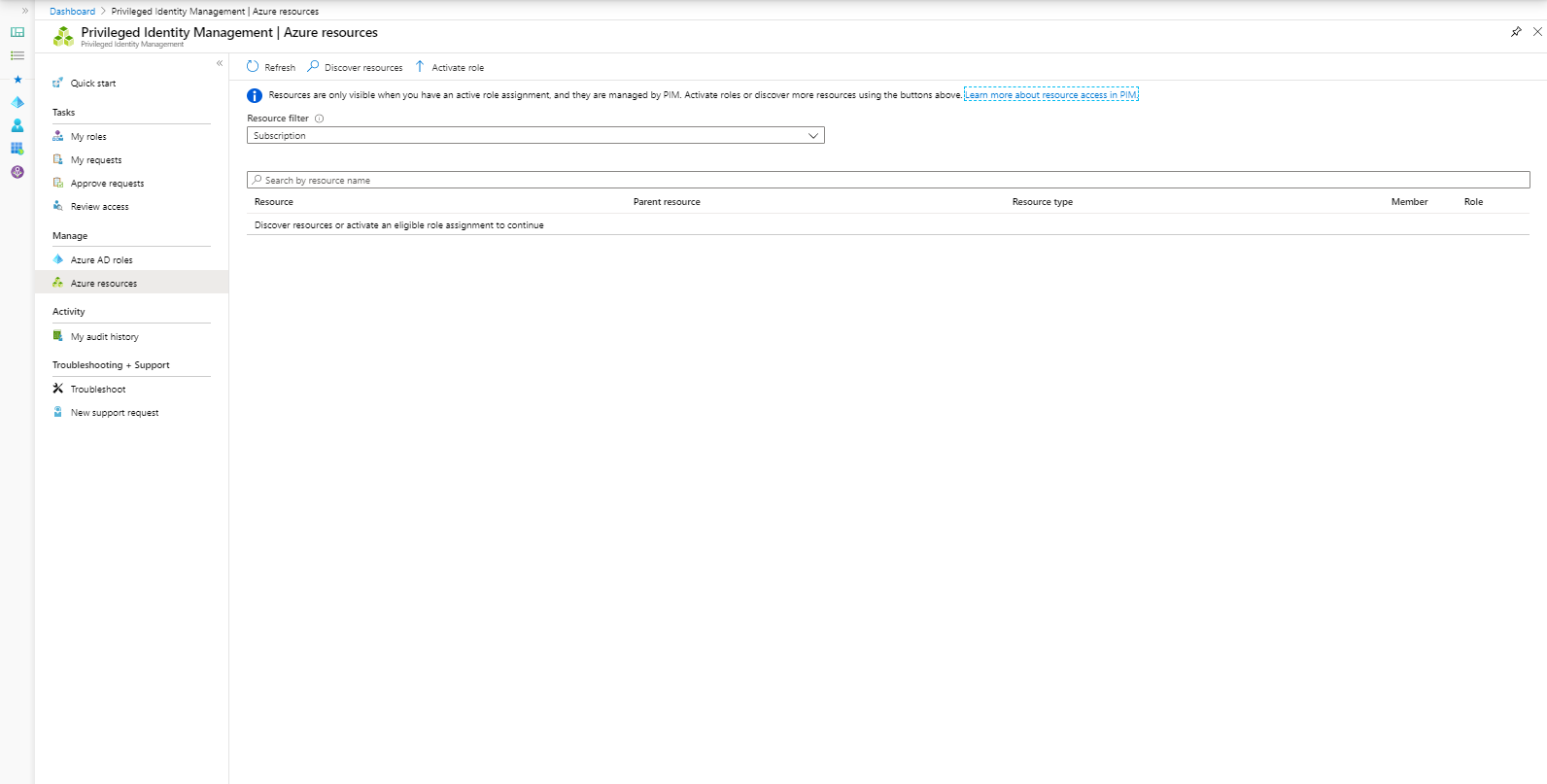
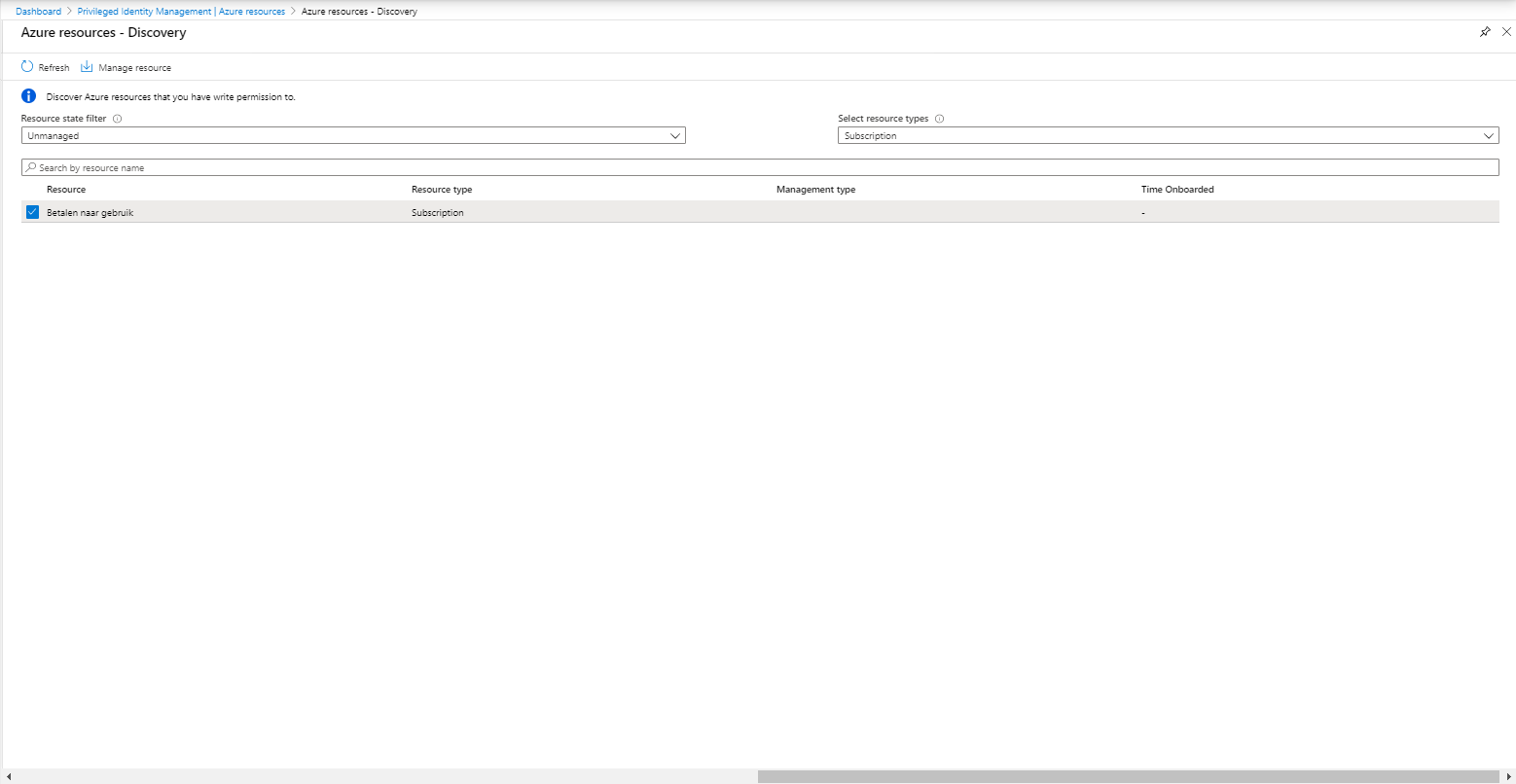
Besides providing access to Azure roles, it’s also possible to use PIM to give access to your Azure resources.
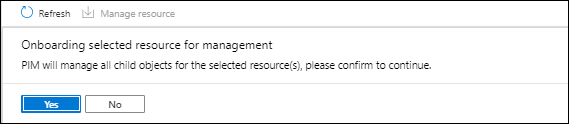
In order to do so, the Azure resources must be discoverable, if you want to discover all it’s best to discover the Root Management Group since that will cover all subscriptions underneath. In the example below we will add a subscription.
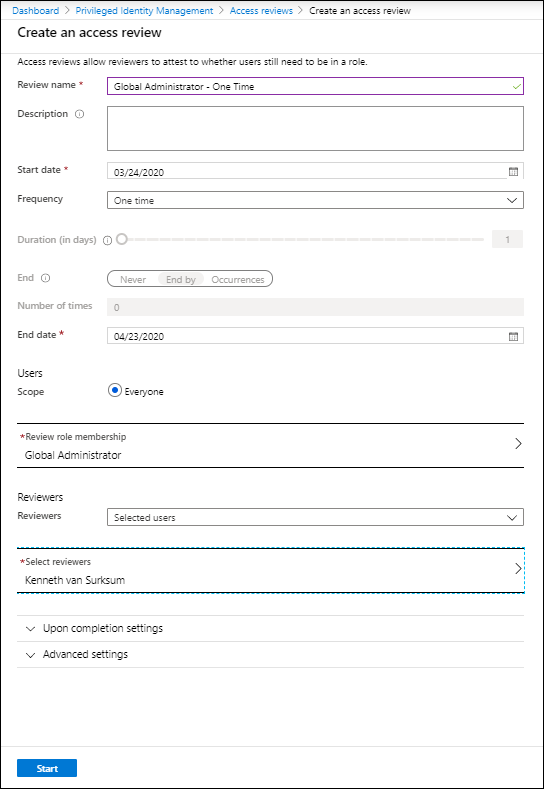
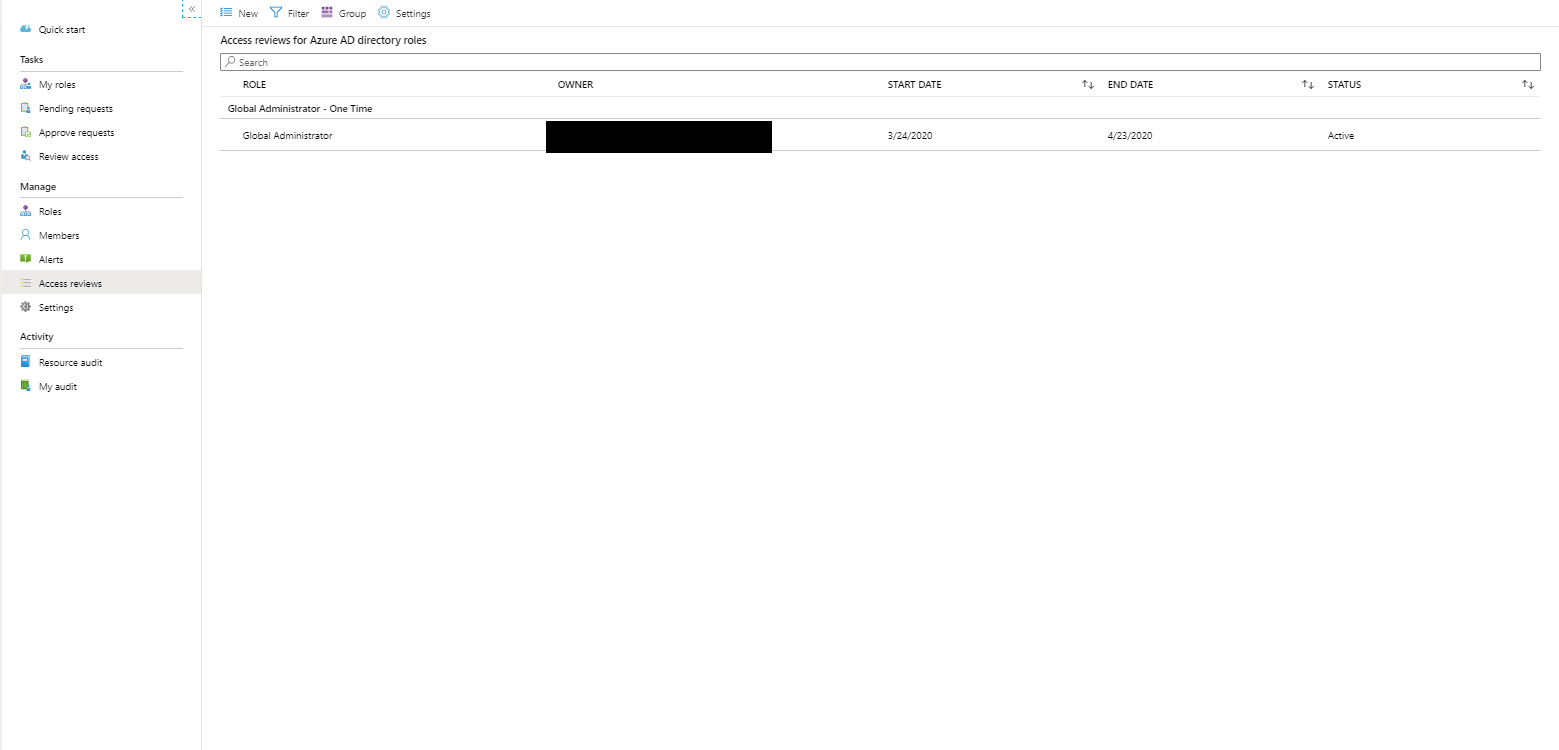
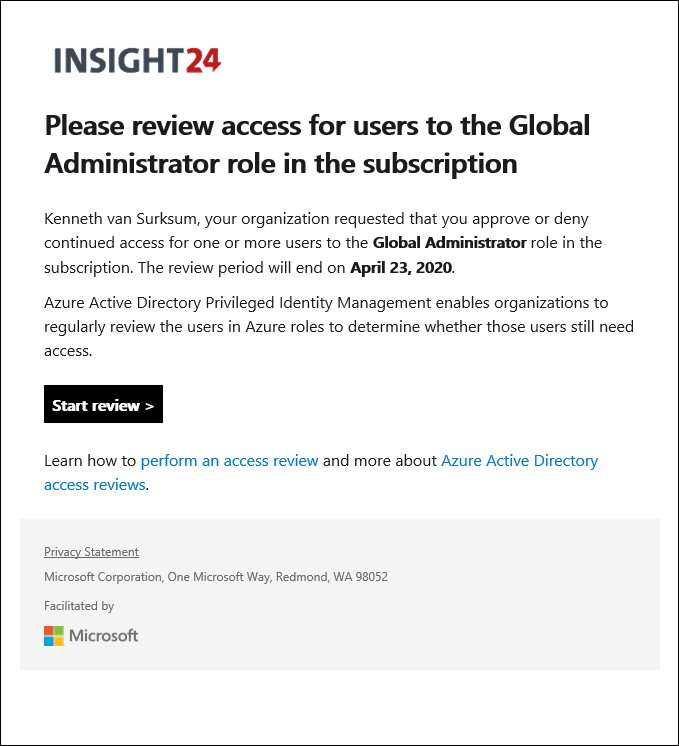
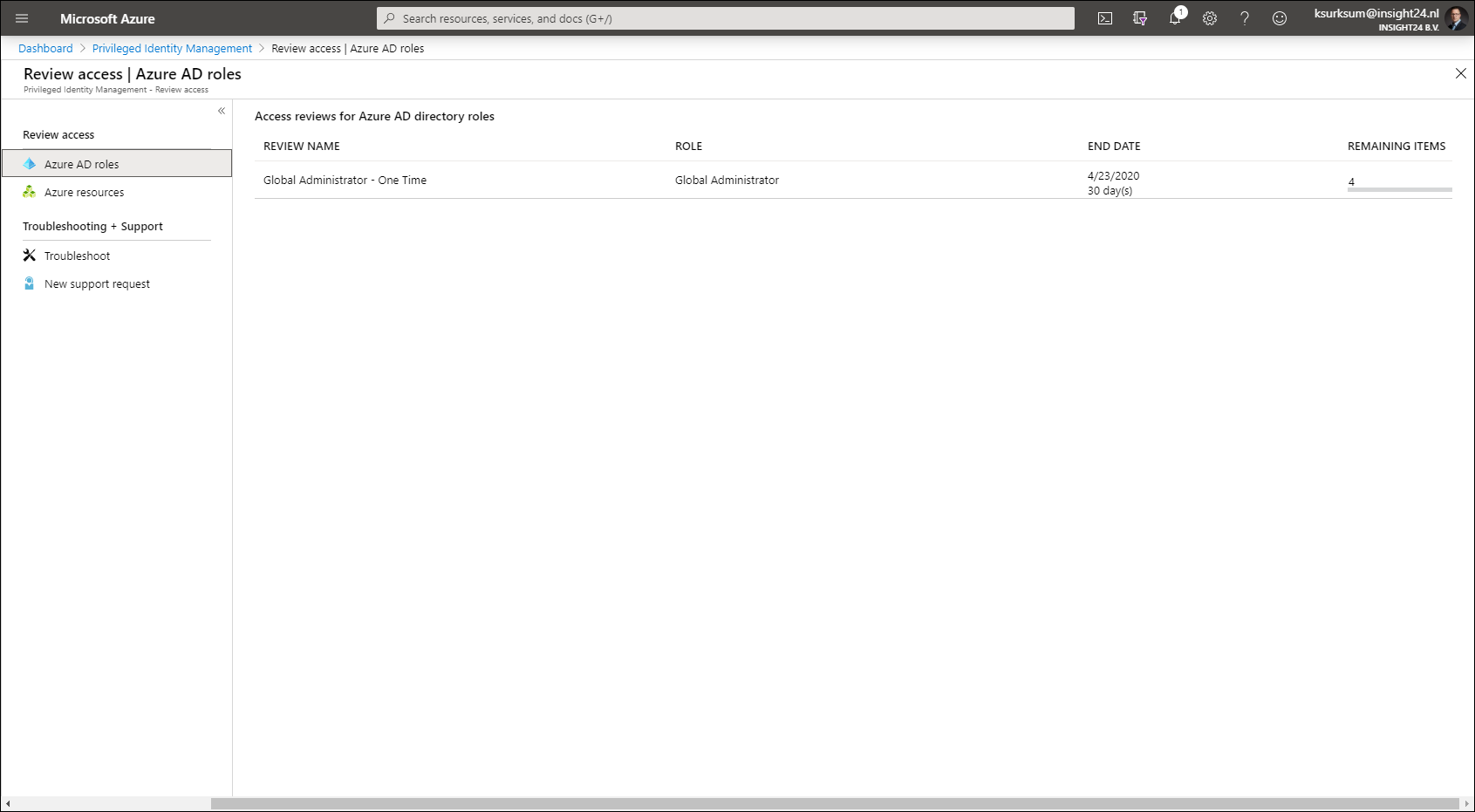
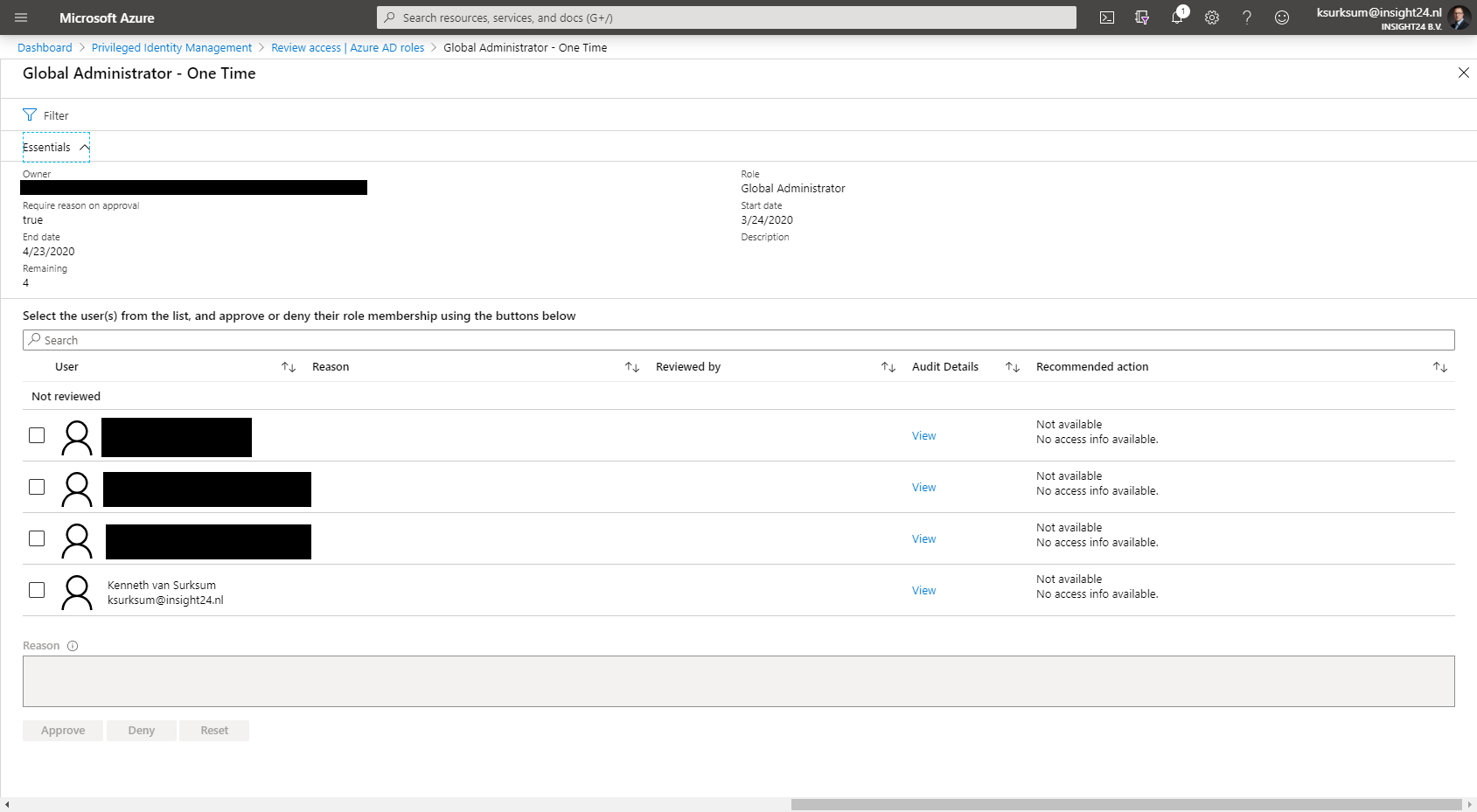
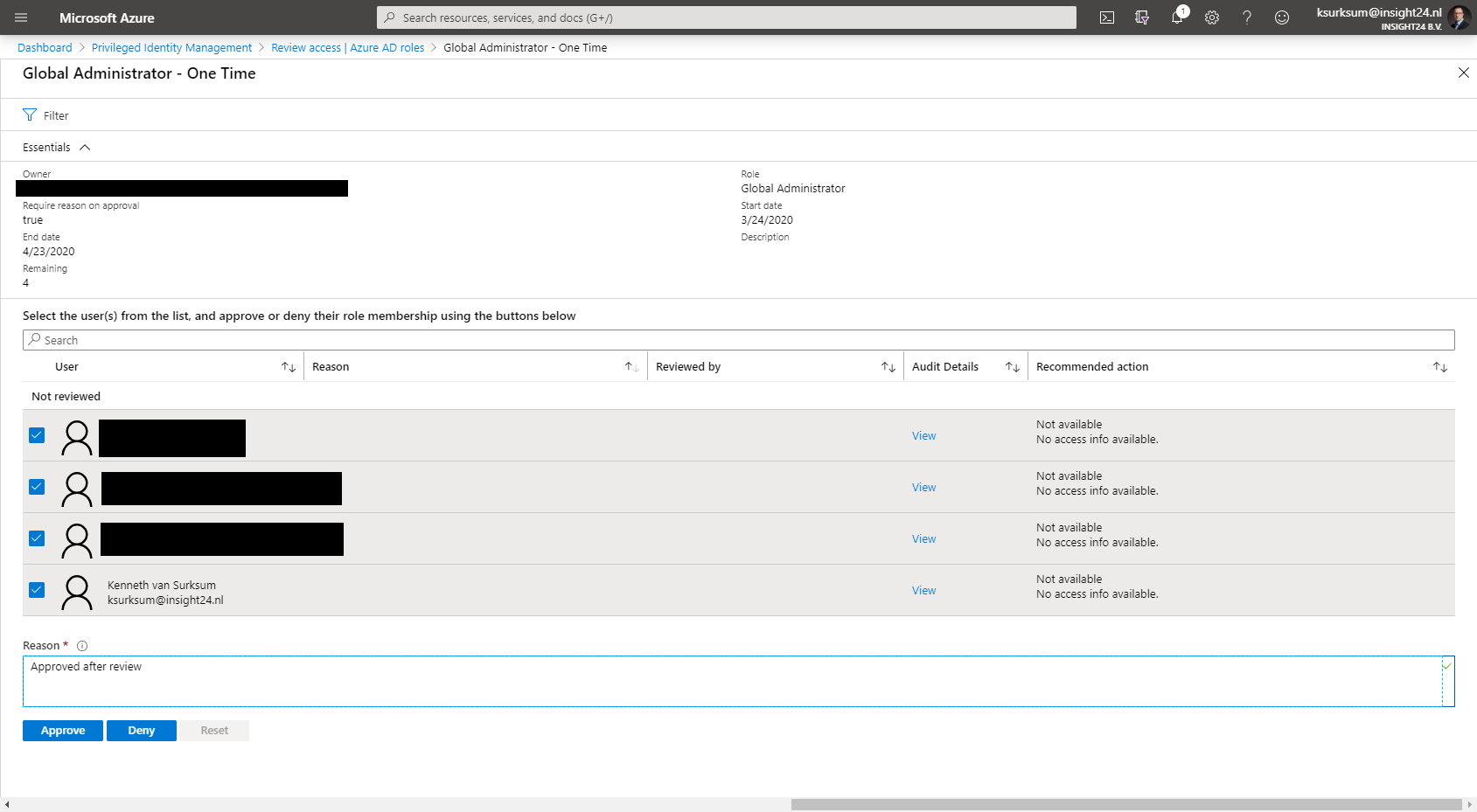
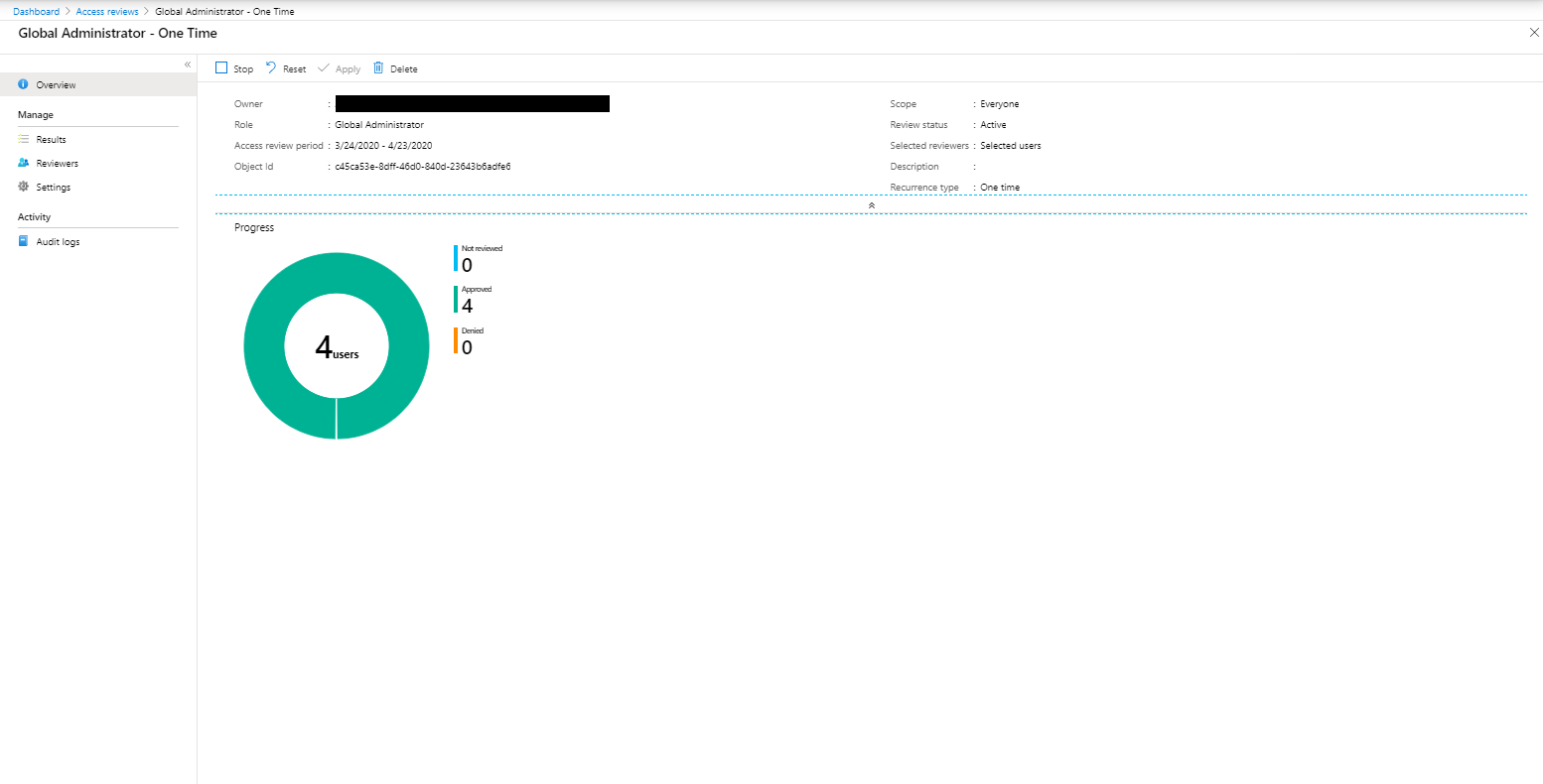
Access Reviews
Access reviews are tasks with the purpose of reviewing who is member of a Azure AD role, for highly privileged roles it’s recommended to create Access Reviews which are performed by a Security administrator for example.
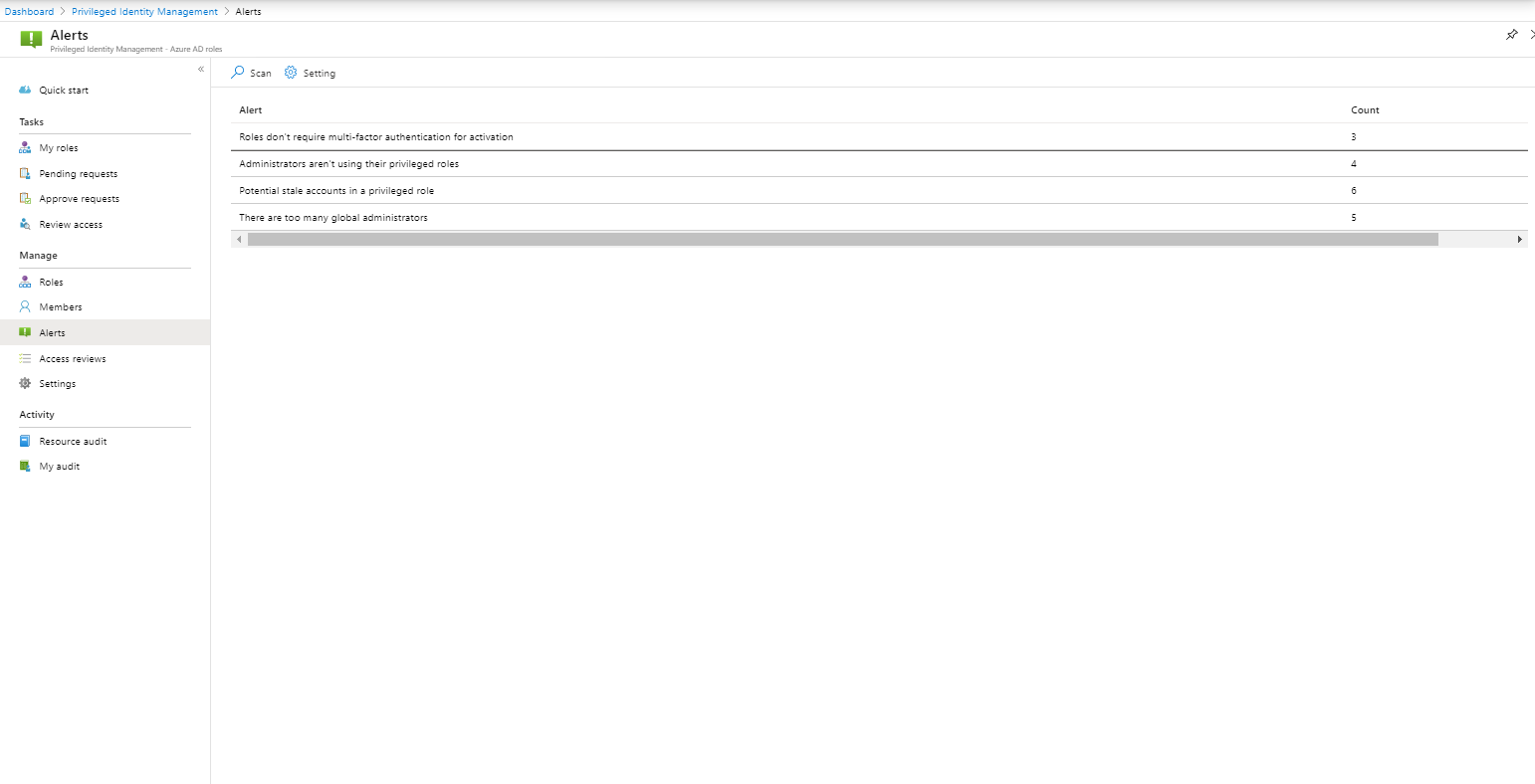
Alerts
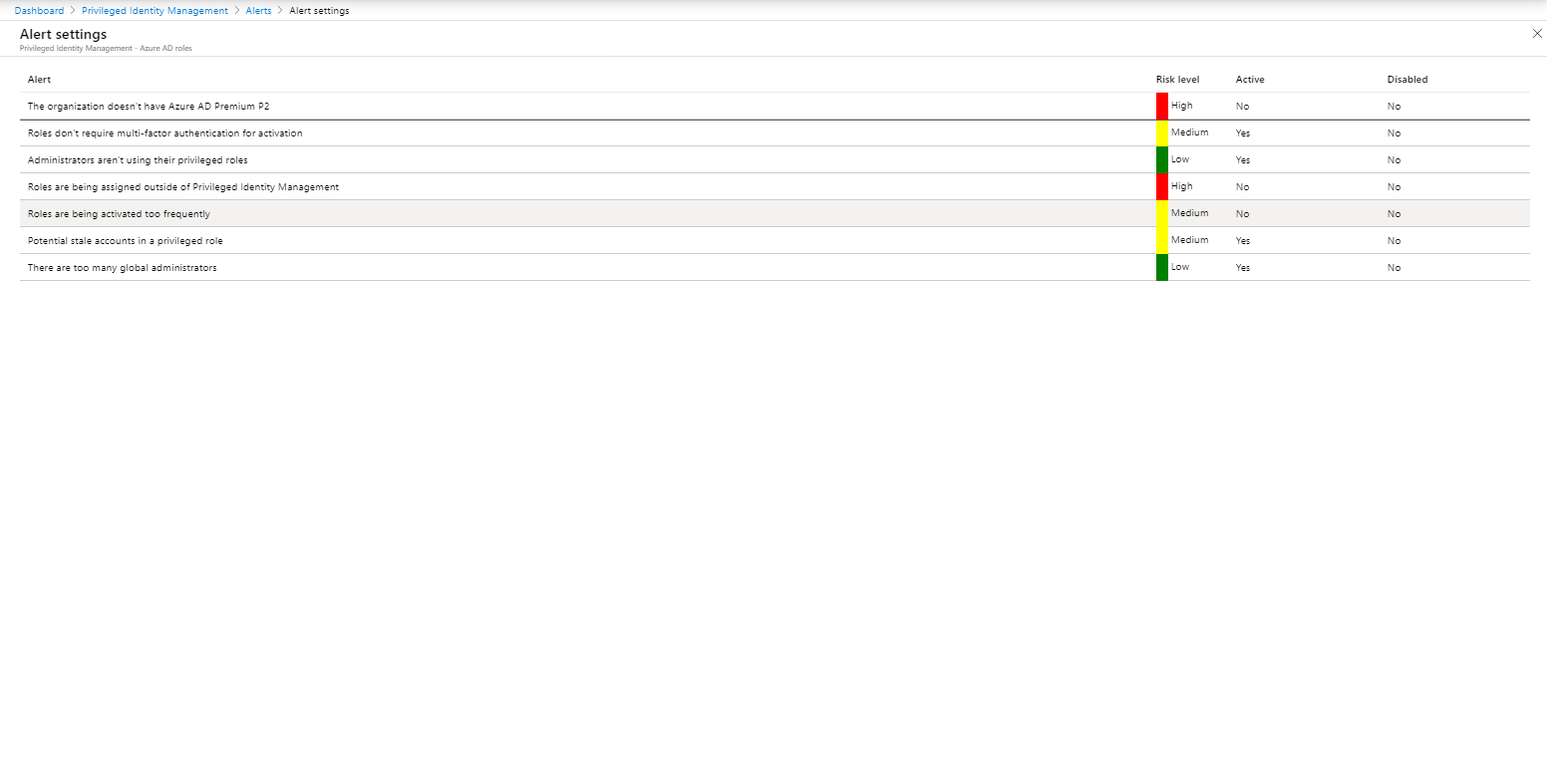
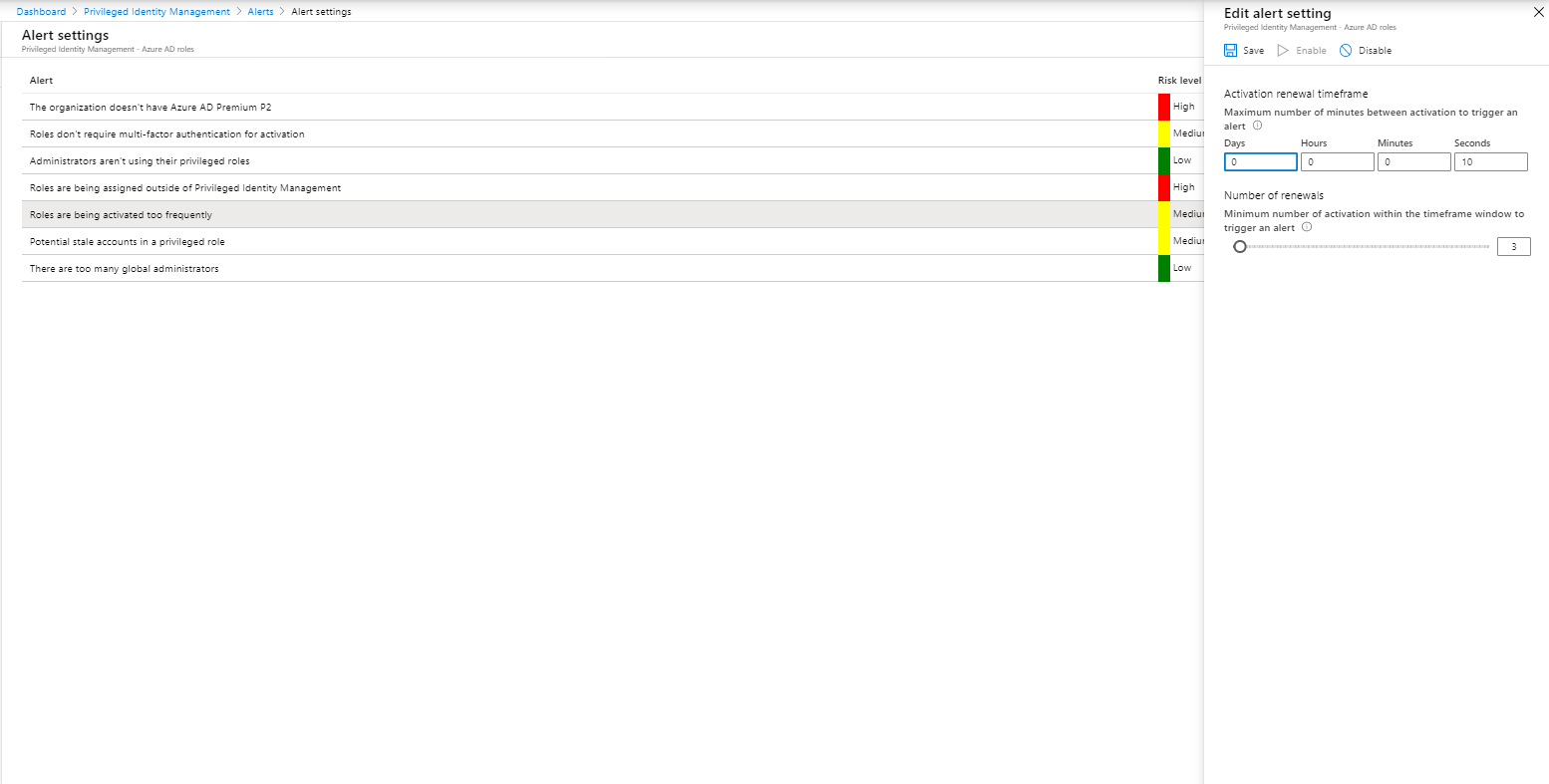
Alerts can help to keep the environment optimized, it would better to call them recommendations, since they don’t provide the same functionality as Alerts in for example Azure Monitor. The following “Alerts” are available:
- The organization doesn’t have Azure AD Premium P2
- Roles don’t require multi-factor authentication for activation
- Administrators aren’t using their privileged roles
- Roles are being assigned outside of Privileged Identity Management
- Roles are being activated too frequently
- Potential stale accounts in a privileged role
- There are too many global administrators
Caveats and challenges
Based on my experiences so far, I found the following challenges, missing functionality and caveats.
Admins in notifications and no options to define default settings applicable to all roles at once
When you modify the role, you can define the notifications. For example, a Role activation alert is by default sent to Admin. But who is Admin? – after some testing I found out that Admin are permanent and eligible Global Administrators, and not the Privileged Role Administrator.
While you can provide additional recipients, you have to define that per role, which is a lot of work.
Feedback item: PIM – Configure default settings for all role assignments
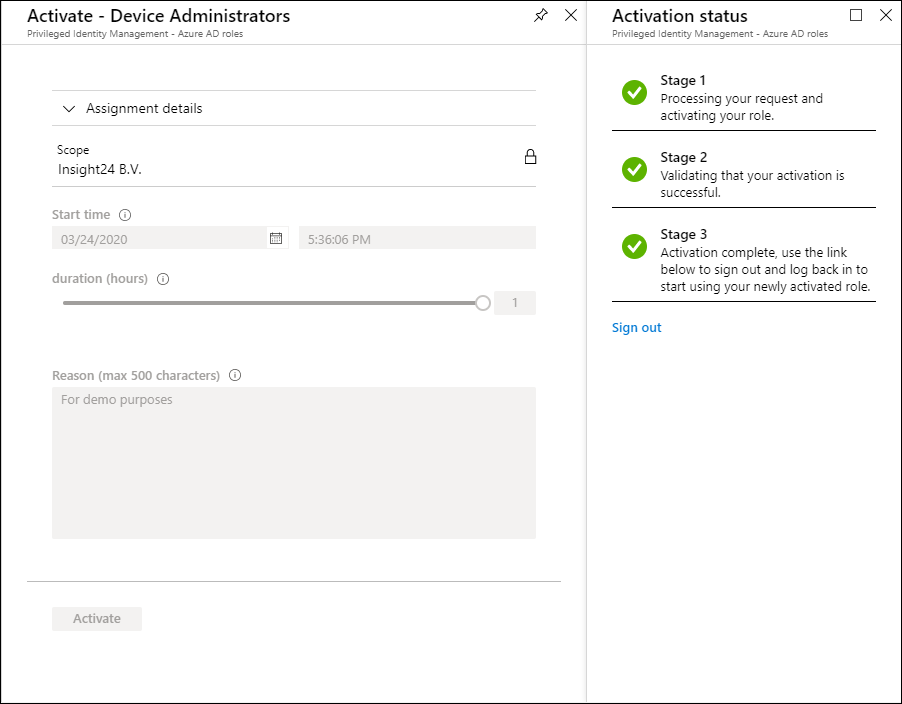
Logging out from browser necessary in order to activate roles
I’ve seen a lot of admins struggle with the fact that they must logout from the browser and login again in order to receive their rights. While the reason for this is somewhat obvious when you are used to adding rights to on-premise accounts, I sometimes see issues where not all browser windows are closed and users have some strange experiences.
Not available from any of the other (Security) portals (M365,O365)
Azure AD PIM is only available to start from the Azure portal (or the Azure AD Admin portal) – but most of the time the rights are used for Intune, Exchange, SharePoint and other Office 365 related tasks. I would be nice to have links to PIM or PIM integrated from the portals in those environments as well.
Feedback item: PIM in Office 365 Admin Portal
You cannot make modifications to your own account
While from a security perspective this makes sense, you are not able to modify your own account. So when you are finished setting up PIM, make sure that you ask one of your colleagues to help you setup your own account correctly in PIM as well.
Exchange Administrator and other roles can take a while to propagate
In my experience it takes too long to propagate the Exchange Service Administrator role into the Exchange Administrative Center (EAC). In my experience it takes sometimes more than 20 minutes before the activated rights to become effective, which is not acceptable.
Experiences a similar issue while after activating the Global Administrator role, I was not able to make modifications to a Conditional Access policy. Even though the Azure AD portal listed me as a Global Administrator. After waiting a while, logging out and back on again, I was able to save the changes in the Conditional Access policy.
Microsoft recommends the following in that case:
In case of any delay after activation, follow these steps after you activate to use your Azure AD roles immediately.
- Open Azure AD Privileged Identity Management.
- Select My roles to see a list of your eligible Azure AD roles and Azure resource roles.
- Select Azure AD roles.
- Select the Active roles tab.
- Once the role is active, sign out of the portal and sign back in. The role should now be available to use.
Feedback item: PIM to work correctly with the Exchange Admin role
Device Administrator takes a long time to propagate
Keep in mind that Device Administrators are being added to the local administrator group of your Azure AD joined machines, even though the group is added, it can take up to 4 hours (the refresh time of the client) before a change to the group is reflected on the client itself. I’ve even seen longer times in the forums. Therefore using PIM for the Device Administrator role is not acceptable yet. See also my other blogpost on this topic: Challenges while managing administrative privileges on your Azure AD joined Windows 10 devices
Sometimes roles must be activated if you want to add them to other Azure AD configurations
Let’s take for example Admin consent requests, here you can define the users who can perform reviews. When selecting you can select only the active members of the Global, Application or Cloud Application Administrator role. Workaround is to either ask any users who you want to include to activate their role, or to make users temporarily permanent member of the role, include in reviewers and then make them Eligible again.
Feedback item: Make sure that in some situations Eligible users are selectable
Some more granular roles missing
Besides Exchange Service Administrator, EOL provides some other custom roles not available through Azure AD. It’s therefore not possible to make these roles available via PIM
Feedback item: Azure PIM support for custom Exchange RBAC Role Groups
Alerts are not send out
Alerts are only available in the console, no options to send them to other products like Azure Monitor, or email them when they are raised.
Feedback item: Expose AzureAD PIM Alerts via an API
Access Reviews on Azure roles
Currently it’s not possible to define Access Reviews on Azure roles, like contributor.
Feedback item: Access review
You cannot activate multiple roles at once
Say, for example you want to activate both Exchange Service Administrator and User Administrator you have to do that twice, which is time consuming.
I’ve found a utility called: “PIM ME NOW !” which is written by Jan Geisbauer which is capable of activating multiple roles at once. Jan provides the source, and some good examples on how to use the tool,
Feedback item: Be able to select multiple roles for a single user in PIM
License needed on your Admin account
See also my other blogpost on this topic, I really hope Microsoft is going to clarify this soon and make every license person based on not account based. See also my other blogpost on this topic: License requirements for administering Microsoft 365 services
Conclusion
While this article only touched some of the functionality that PIM provides I hope it gives a good idea of what it can do.
Even though there are many issues and caveats with the product, it’s still better than not having it implemented at all. Let’s hope Microsoft addresses the faced challenges with Azure AD PIM on short notice, making it an even more attractive must have tool.
References
License requirements for administering Microsoft 365 services
Securing privileged access for hybrid and cloud deployments in Azure AD
Create an access review of Azure AD roles in Privileged Identity Management


Hi, excellent post. Question, did you run into any production issues or other issues when enabling PIM for Azure Resources?
Hi Bilal,
Sorry for my late reply.
To be honest, I haven’t done a big implementation in a production environment yet, so for now it was only limited to setting this up and verifying in my own test environment. I’m planning an implementation of PIM for Azure Resources at this moment though and if I find any lessons learned I will definitely post them online.
Regards,
Kenneth
I am currently running PIM in production, and have had some issues due to the lack of enterprise features in PIM. For example they didn’t have a search feature for the Azure AD role assignment for months. The Azure resources PIM, is lacking the ability to add users directly to services with RBAC, it must be done at the subscription level. You can also work with management groups to standardize your RBAC and policies for auditing, with Azure PIM you can assign roles to management groups and that would only extend to the subscriptions in that management group. There are other weird things, but by and large it is a pretty good product.
Thanks for sharing this. Excellent and great attention to detail.
Hi Kenneth,
Nice information sharing and your experience, Thank you. I have one question about managing non-email enabled user who are some sort of Administrators in Azure AD. How do you run access review for such accounts where they need to respond to the reviews, etc.?
Regards,
Gaurang
Hi Guarang,
I actually found a really nice article written by Michael Mardahl explaining a possible solution, see: https://msendpointmgr.com/2020/08/08/2-for-1-mail-enable-unlicensed-admin-accounts/
Regards,
Kenneth
Hi,
We are looking into PIM and seems to work fine.
The only issue we have is conditional access, we have a conditional access policy that blocks access to the azure portal if there is no role assigned, and to go to PIM you need to go to the Azure portal…..
Like a chicken and egg problem, does anyone has the same issue and have a nice solution for this ?
Tnx.