I’m proud to announce the December 2022 update of my Conditional Access demystified whitepaper. With this release, we have reached the fifth iteration of the whitepaper and accompanying files.
I released the first version in in August 2019 after writing several blogposts on the subject. In May last year I released the second version containing a lot of updates. In February this year I released another update, and in October 2021 I released update 4. Today I’m releasing a new update, the December 2022 version 1.4 update.
The paper has had some updates, including all information from the blogposts I’ve written about the subject since the latest release. The paper therefore has grown from 95 to 140 pages at this point in time, for reference the May 2020 version contained only 30 pages.
You can download the paper from my GitHub page here: Conditional Access demystified-v1.4 – December 2022.pdf
In this version I added the following updates:
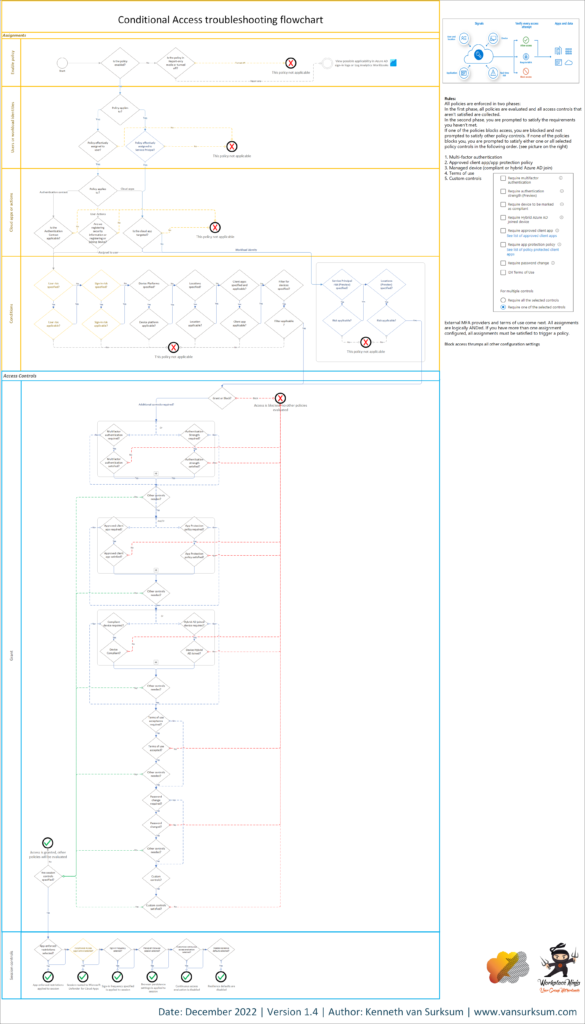
Workflow cheat sheet
The workflow cheat sheet has been updated to reflect the current status of the Conditional Access policies. With the workflow I want to provide IT pro’s with a handy cheat sheet which they can use while building or troubleshooting conditional access policies. If you print the cheat sheet or display it on a secondary monitor it can be quite handy and I use it all the time.
The workflow cheat sheet is available separately for download from my GitHub page here: Conditional Access Workflow – v1.4.pdf
My recommended set of Conditional Access policies
I’ve included my recommended set of conditional access policies. The reasoning behind the policies is described, and I will detail each policy which needs to be created. Also a reference to a spreadsheet is included, containing all the necessary settings in the Conditional Access policy: Conditional Access Policy Description-v1.4.xlsx
New in this version is that I also exported the CA policies from my environment using the Intune Manager tool written by Mikael Karlsson, with this tool you should also be able to import the baseline policies in your own environment. Please make sure that you import the policies as “Report-Only” first and not import them turned on.
You can find the baseline policies provided in this version here: https://github.com/kennethvs/cabaseline202212
Further updates
I also added other information like:
- Filtering for Apps and Workload Identities
- Granular Guest control
- Authentication Strength
- Cross tenant settings
- More information about CA Templates
- Updated Approved Apps versus Require App Protection policy information
- Updated information about break glass accounts
- And more..
I hope you enjoy and learn something from reading the paper and that it helps you to setup Conditional Access for the tenant(s) you are administering. Feel free to reach out if you have any questions or remarks.


Thanks Alain for the great update Kenneth.
Would it make sense to scope CAD002 to all cloud apps? Doing so unfortunately blocks edge profiles from signing in.
Is there a way to scope CAD002 to everything except for edge profile sign-in?
Or should we add all relevant apps to the CAD002 rule on top of O365?
Hi Roel,
Thanks for visiting my blog –
CAD013 is what you are looking for, I would never scope this to ALL apps since it will certainly break things, it will break the apps which you cannot select in the Conditional Access properties and you will have a really hard time figuring out which. But you can add Apps on a per-app basis and add an additional layer above Office 365.
Hope this helps, if not please let me know.
/Kenneth
Hi Ken, First off, let me say thank you for the guidance, structure, and knowledge that you’ve imparted upon me. I’ve learned so much from reading your blog and using all of the tools.
I have a general question pertaining to device enrollment. I would like your opinion, generally speaking, about device enrollment.
It seems to me that an organization should not be in the business of forcing device enrollment for “All Cloud Apps.” In fact, it seems to me that an organization should only enroll devices – Certainly, company-owned devices – whereby there’s a reason to completely control the device. In the case of company-owned devices, it seems obvious that device enrollment and compliance is necessary, simply by nature of the device being company-owned. Furthermore, it seems to me that when it comes to BYOD’s, an organization should not make it a requirement to enforce enrollment (i.e. a grant control of “device must be compliant.”) when accessing “All Cloud Apps.” Rather, the more obvious option is, an organization should enforce device compliance and app protection policies ONLY on apps which are on the list of Intune supported apps – https://learn.microsoft.com/en-us/mem/intune/apps/apps-supported-intune-apps.
For instance, we have a conditional access policy called “CAD002-O365: Grant iOS and Android access for All users when Modern Auth Clients and Approved App and Compliant-v1.0.” Given the naming convention, you can see that this policy is scoped only to Office 365 and mobile device platforms. Thus, we have a grant control of compliance and approved apps.
I welcome your thoughts.
Warm regards,
John Barnes
Hi John,
The way I see it is quite simple, when the device is MDM managed (and we can measure compliance) we can allow Modern Authentication Clients and Browser access to both O365 and other Cloud Apps. When the device is not compliant (BYOD, but also any other computer in the world which the company doesn’t manage), we only allow Browser access, or MAM (on mobiles with the App Protection Policies). Within Browser access, we have restrictions (the App Enforced Restrictions, in combination with the Sensitivity Labels for Containers) or by routing the session through Microsoft Defender for Cloud Apps (MDCA) where we can define policies on what is allowed on non-managed devices.
With all the Webifying of Apps going on, standarizing on Browser access for non-managed devices is the way forward in my opinion, especially if most apps can be installed as a Progressive Web App (PWA) where the user in most cases doesn’t even notice that he/she is working in a Web browser.
My 2 cents, feel free to ask further questions if you have.
Regards,
Kenneth
Hi Kenneth,
first off: Big “thank you” for your continuous work and guidance along MSFT Azure/Conditional Access! I highly appreciate your work!
My question is related to the document “Conditional Access Implementation Workflow – V1.4.pdf”. I believe that the answers (Y/N) to the question “Is legacy/basic authentication still in use?” are in reverse order.
It says: “IF legacy authentication IS NOT in use –> then use Azure AD to detect legacy sign-ins.”
I believe, that it should say “IF legacy authentication IS in use –> then …detect legacy sign-ins”
I am looking forward to be reading from you.
Have a great day.
kind regards,
Dominik
Hi Dominik,
Thanks for your comment, I will look into it and reflect necessary changes in the version 1.5 of the paper.
/Kenneth
Hi,
The conditional access policy set is great and been incredibly useful, thank you for your considerable effort. Are there any updates to it incorporating the many changes to conditional access policies that Microsoft have made as of late?
Many thanks,
Ben
Hi,
Great document, had a nice learning experience from it. Was wondering if there is comming a new version of the document since there have been a lot of changes in CA from 2022 till now. Looking forward to your reply.
Tnx,
Stefan