Introduction
Modern collaboration tools such as OneDrive and SharePoint depend on efficient browser communication to deliver both online and offline functionality. When specific content delivery endpoints are blocked by browser policies, users may experience reduced performance or complete loss of offline file access. Configuring the correct browser policies ensures seamless integration between the browser and Microsoft 365 services.
Table of Contents
- Understanding the impact of browser restrictions on SharePoint and OneDrive
- Required URLs for performance and offline access
- Configuring Microsoft Edge in Intune Settings Catalog
- Configuring Google Chrome using imported ADMX templates
- Summary
- References
Understanding the impact of browser restrictions on SharePoint and OneDrive
When browsers enforce strict site access rules, OneDrive and SharePoint can lose the ability to cache files for offline use or properly connect to synchronization endpoints. Microsoft communicated this in Message Center post MC1150662, recommending that administrators explicitly allow certain domains used by these services to preserve functionality. Chrome and Edge will roll out this privacy related change as part of Chromium 142 at the end of October 2025 (previously end of September).
By default, browsers may block or limit communication to non-listed endpoints, impacting:
- File synchronization and offline availability
- SharePoint web performance and caching
- Seamless authentication via Microsoft 365 session tokens
Required URLs for performance and offline access
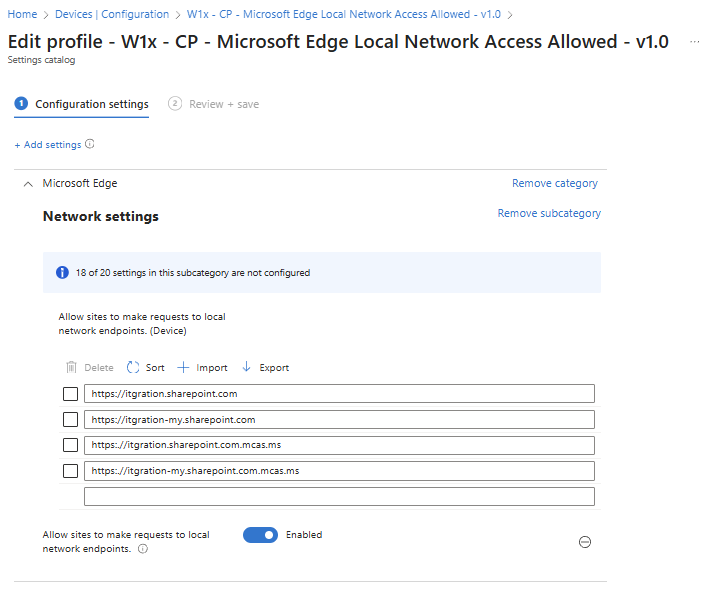
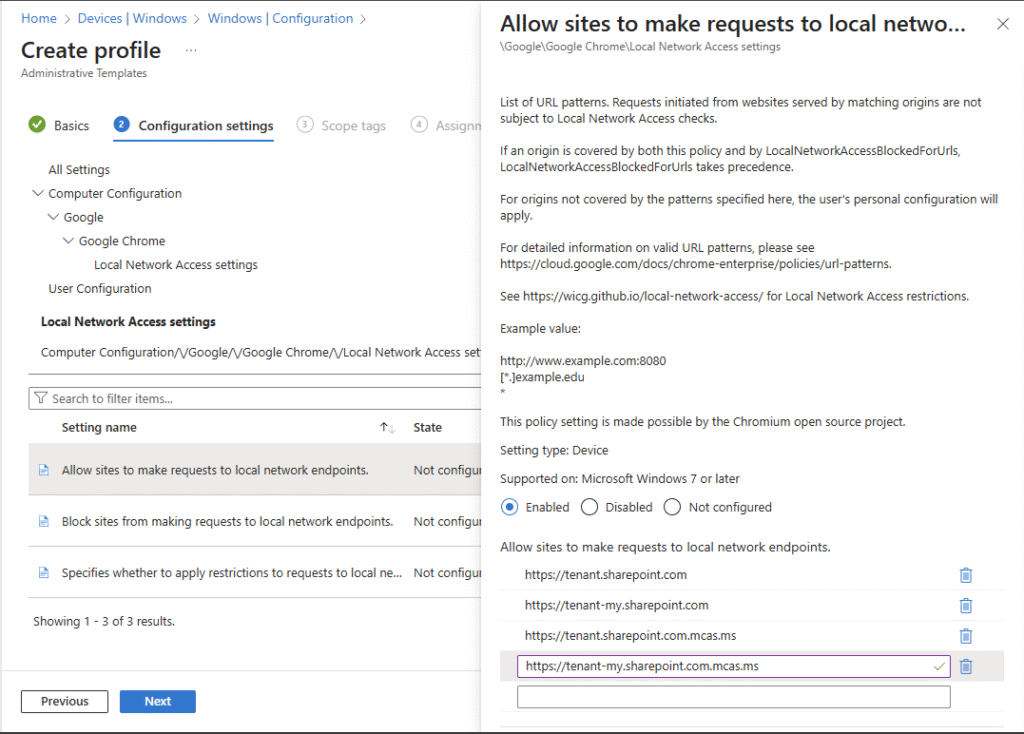
To maintain full web performance and offline capability, the following URLs must be allowed in both Microsoft Edge and Google Chrome under the policy setting named ‘Allow sites to make requests to local network endpoints’ in the browser configuration:
https://tenant.sharepoint.comhttps://tenant-my.sharepoint.comhttps://tenant.sharepoint.com.mcas.mshttps://tenant-my.sharepoint.com.mcas.ms
Replace tenant with your organization’s SharePoint Online tenant name. The additional mcas.ms entries correspond to Microsoft Defender for Cloud Apps proxy endpoints, ensuring compatibility with environments where session controls are enforced. Note that when Defender for Cloud Apps integration is enabled in Microsoft Edge, these mcas.ms entries may not be strictly required, but including them is still recommended for full compatibility. However, for Google Chrome these mcas.ms URLs remain necessary to ensure proper connectivity when Defender for Cloud Apps session controls are active.
Configuring Microsoft Edge in Intune Settings Catalog
For Microsoft Edge, this configuration can be achieved directly through the Settings Catalog in Microsoft Intune:
- Open the Intune admin center and navigate to Devices → Configuration profiles → Create profile.
- Choose Windows 10 and later as the platform and select Settings Catalog as the profile type.
- Under Microsoft Edge, locate the setting Allow sites to make requests to local network endpoints.
- Add the required URLs listed above.
- Assign the profile to your desired device or user groups.
This approach automatically applies the allowlist to managed Edge browsers, maintaining compatibility with SharePoint and OneDrive web applications.
Configuring Google Chrome using imported ADMX templates
Unlike Edge, Google Chrome does not yet expose this policy directly in the Intune Settings Catalog. To configure it, administrators must import the latest Google Chrome ADMX templates.
- Download the latest ADMX files from the Chrome Enterprise download page.
- Import google.admx first, followed by chrome.admx. The import order is important for dependency handling.
- Even though Intune displays the version as 1.0, the actual Chrome version is noted in the ADMX file as a hidden comment, for example:
<!--chrome version: 141.0.7390.123--> - If you have previously imported an older Chrome ADMX version, remove it first. Intune detects both as version 1.0 and will otherwise report a conflict even though the content differs, since it identifies the same targetnamespace and fails the upload.
- The import ADMX interface in Intune is not always intuitive. You may need to refresh the page multiple times and remove dependent policies in the correct order before successfully deleting the old templates. Also when you want to delete an ADMX and you have policies using it, you need to remove those policies first (backup), remove the ADMX, import the new one, and recreate every policy again.
- Once imported, create a new configuration profile using Templates → Imported Administrative templates (Preview) and locate the relevant Chrome policy to configure the URL allowlist.
- Add the same SharePoint and OneDrive URLs to the Chrome policy as defined for Edge.
Following these steps ensures both browsers support SharePoint and OneDrive web operations without performance degradation or loss of offline access.
Summary
Applying the correct browser policies in Intune ensures a consistent user experience when accessing SharePoint and OneDrive resources through Microsoft Edge or Google Chrome. Without these allowlisted URLs, users may face unexpected issues such as slow file browsing, missing offline features, or blocked synchronization endpoints. For environments using Microsoft Defender for Cloud Apps, including the mcas.ms domains is essential to retain full session control functionality.