Introduction
Within Microsoft 365, users can extend app functionality directly from built‑in app stores. Outlook add‑ins, Teams apps, and Office extensions for Word, Excel, PowerPoint, and OneNote provide powerful integration options but also introduce governance and compliance risks if unmanaged. By default, users can access Microsoft and third‑party apps freely through these app stores, allowing data flow to external services and creating potential security exposure.
This article outlines how to centrally govern app store access across Microsoft 365 apps, explains where these controls are configured, and provides a reference design to help administrators standardize governance. It concludes with a short look ahead to Microsoft 365 Copilot, whose introduction has shown why strong governance over app integrations is critical.
Table of contents
- Understanding app store integration in Microsoft 365
- Default behavior and associated risks
- Governance configuration
- Outlook (Exchange Online)
- Microsoft 365 Apps (Word, Excel, PowerPoint, OneNote)
- Teams
- Summary
- References
1. Understanding app store integration in Microsoft 365
Microsoft 365 provides in‑app marketplaces where users can install add‑ins, connectors, and applications designed to extend functionality:
- Outlook Add‑ins: Allow integration with third‑party services (e.g., CRM, task management, signature tools).
- Office Add‑ins (Word, Excel, PowerPoint, OneNote): Extend productivity apps with additional capabilities such as data connectors or content generation tools.
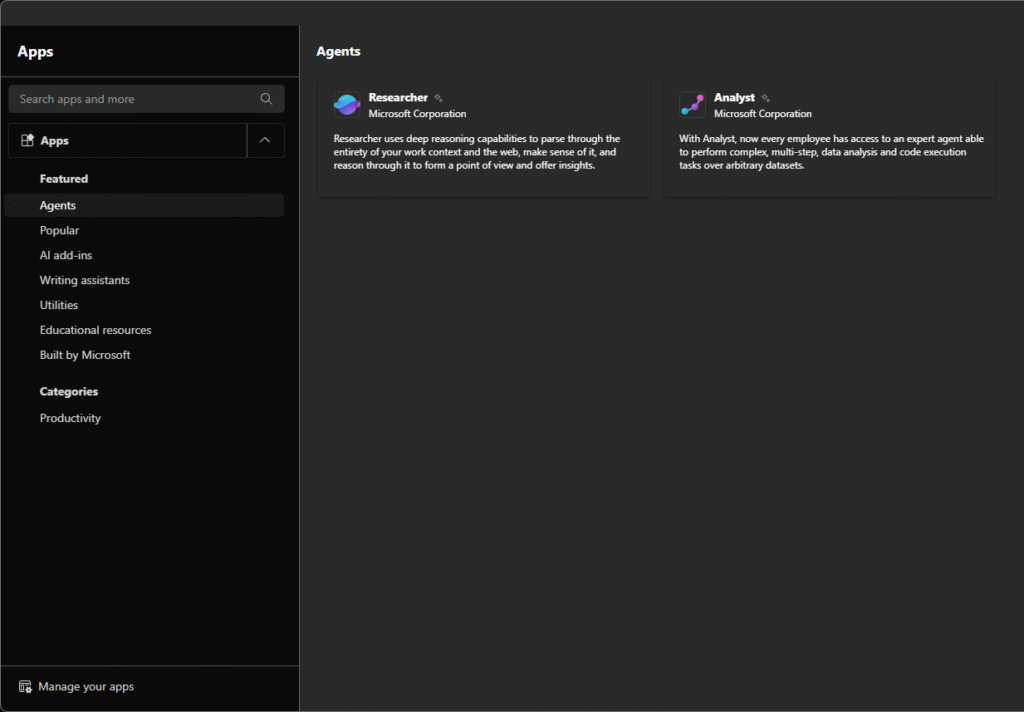
- Teams Apps and Tabs: Integrate collaboration tools, workflows, or bots directly into the Teams environment.
Each of these experiences uses a separate governance surface. Understanding and managing them holistically ensures consistent security posture across the Microsoft 365 suite.
2. Default behavior and associated risks
By default, all users can install available apps and add‑ins from their respective app stores. This behavior provides flexibility but can result in:
- Data exposure – Users may connect sensitive organizational data to unverified third‑party services.
- Shadow IT – New integrations appear in the environment without IT visibility.
- Inconsistent governance – Outlook, Teams, and Office apps have separate admin settings, leading to fragmented control.
Strong app store governance ensures that only approved, compliant integrations are available, protecting both data and user experience.
3. Governance configuration
3.1 Outlook (Exchange Online)
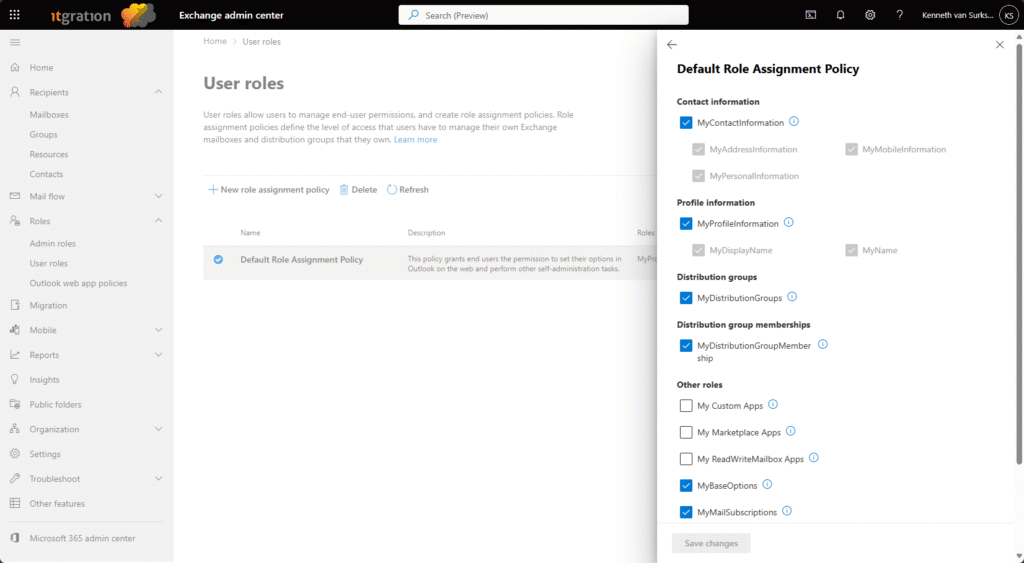
Governance for Outlook add‑ins is managed via role assignment policies.
Path: Exchange admin center → Roles → User roles → Default Role Assignment Policy
Disable the following roles to prevent self‑installation of unapproved apps:
- My Marketplace Apps
- My Custom Apps
- My ReadWriteMailbox Apps
These roles can be re‑enabled later for approved users or admin‑curated catalogs. For more granular control, consider defining multiple assignment policies and linking them to specific user groups.
Learn more – Role assignment policies in Exchange Online
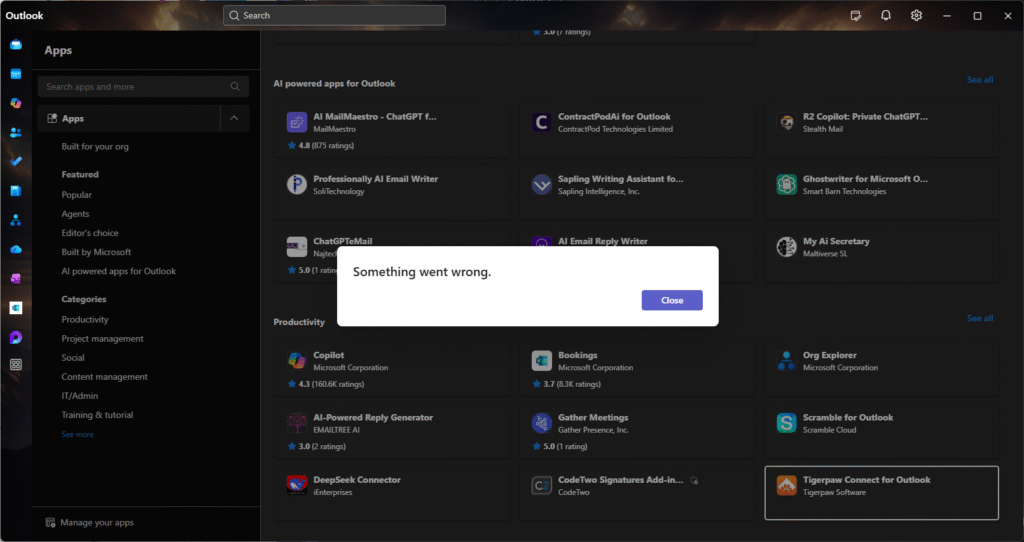
Once Configured the end-user experience is not that good though, because users can still browse the app store from the New Outlook client, but once they want to install the App, they get an error “Something went wrong” giving users no clue on what they should do next.
3.2 Microsoft 365 Apps (Word, Excel, PowerPoint, OneNote)
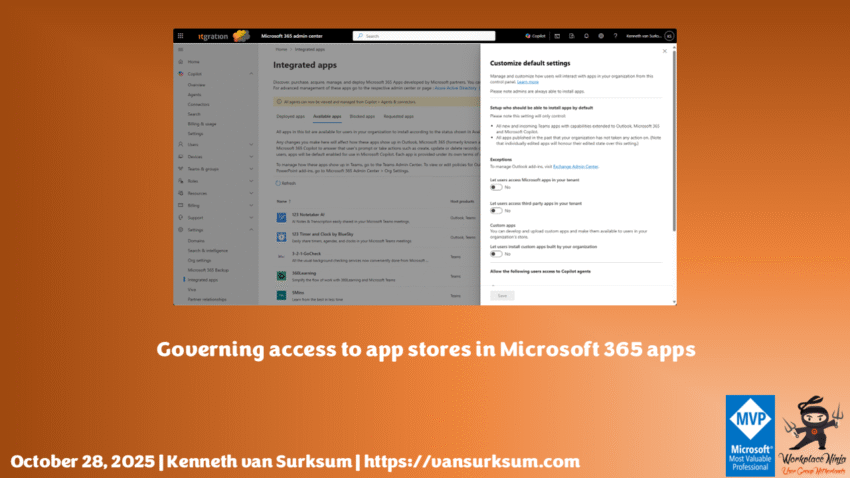
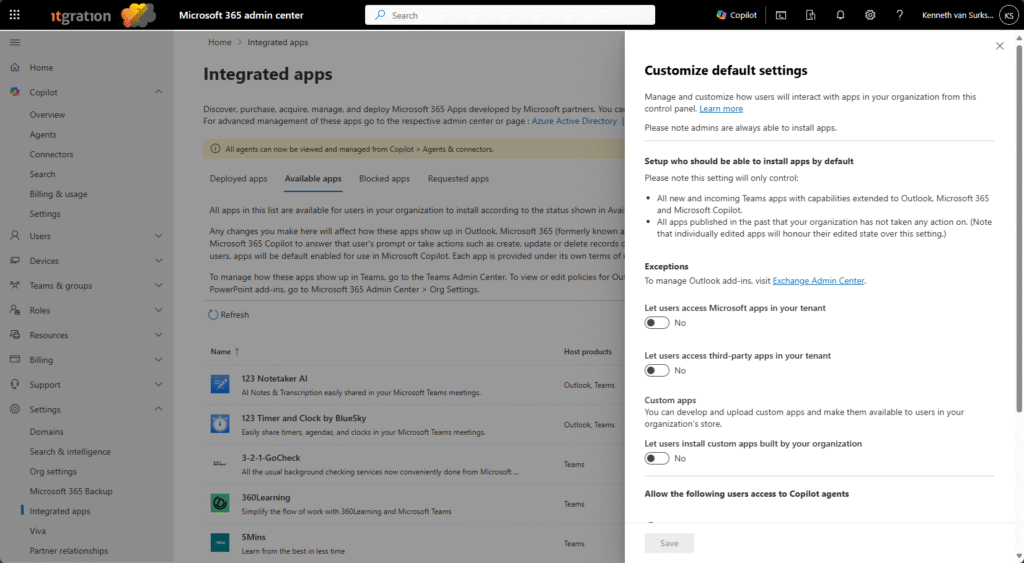
Governance for Office add‑ins is controlled from the Microsoft 365 admin center.
Path: Microsoft 365 admin center → Settings → Integrated Apps -> Available apps -> gear icon ->
Change the following options:
- Let users access Microsoft apps in your tenant: No
- Let users access third‑party apps in your tenant: No
- Let users install custom apps built by your organization: No
After disabling general access, administrators can selectively approve apps or manage custom deployments using the Integrated Apps panel and deploy to groups of users instead of making them available to everyone.
Learn more – Manage integrated apps in Microsoft 365
The end-user experience is different here, since only approved apps will be available to choose, user experience in my opinion is also bad since they can’t see what’s available so that they can for example request this as an approved app.
3.3 Teams
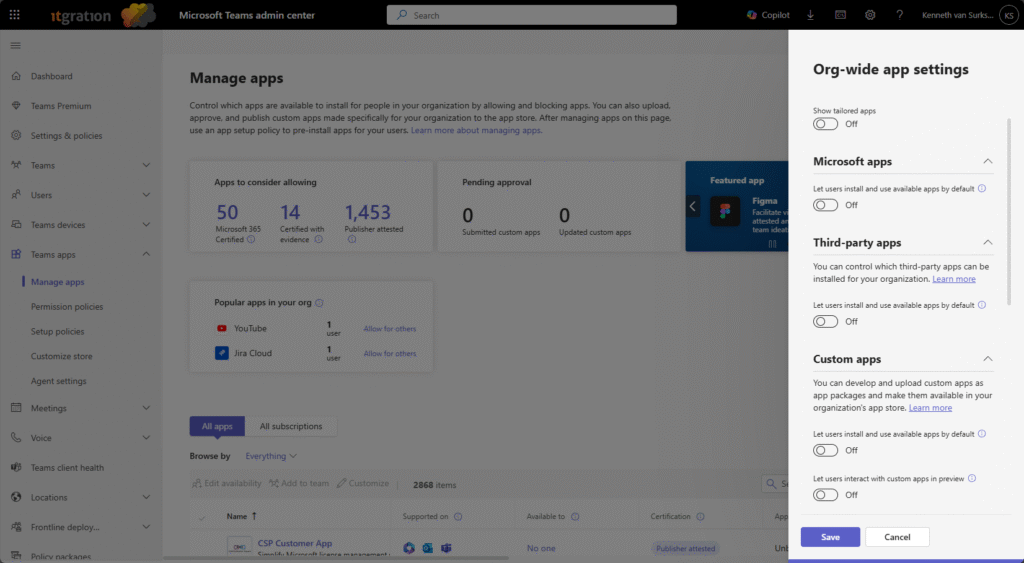
Teams governance requires configuration of app policies within the Teams admin center.
Path: Teams admin center → Teams apps → Manage apps -> Actions -> Org-wide App Settings
Recommendations:
- Allow Microsoft apps: Off by default
- Allow third‑party apps: Off by default
- Allow custom apps: Off by default
- Let users interact with custom apps in preview: Off
To streamline governance:
- Use Permission policies to specify allowed apps by making them available to groups of users
- Use Setup policies to pre‑pin approved apps for user convenience.
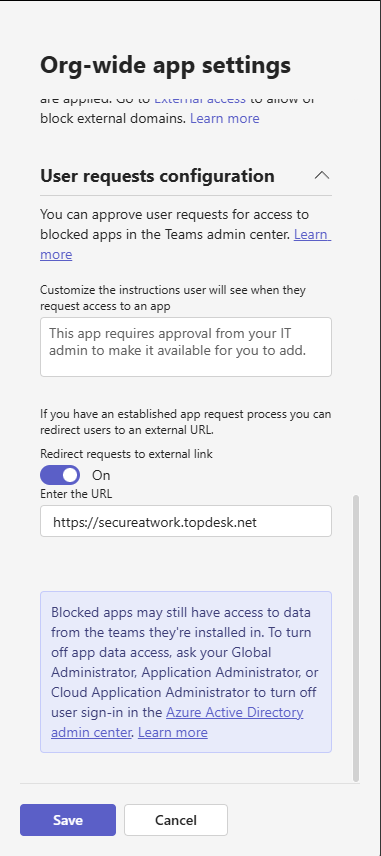
- Redirect user requests for blocked apps to an internal ITSM portal for evaluation.
Learn more – Manage apps in Microsoft Teams
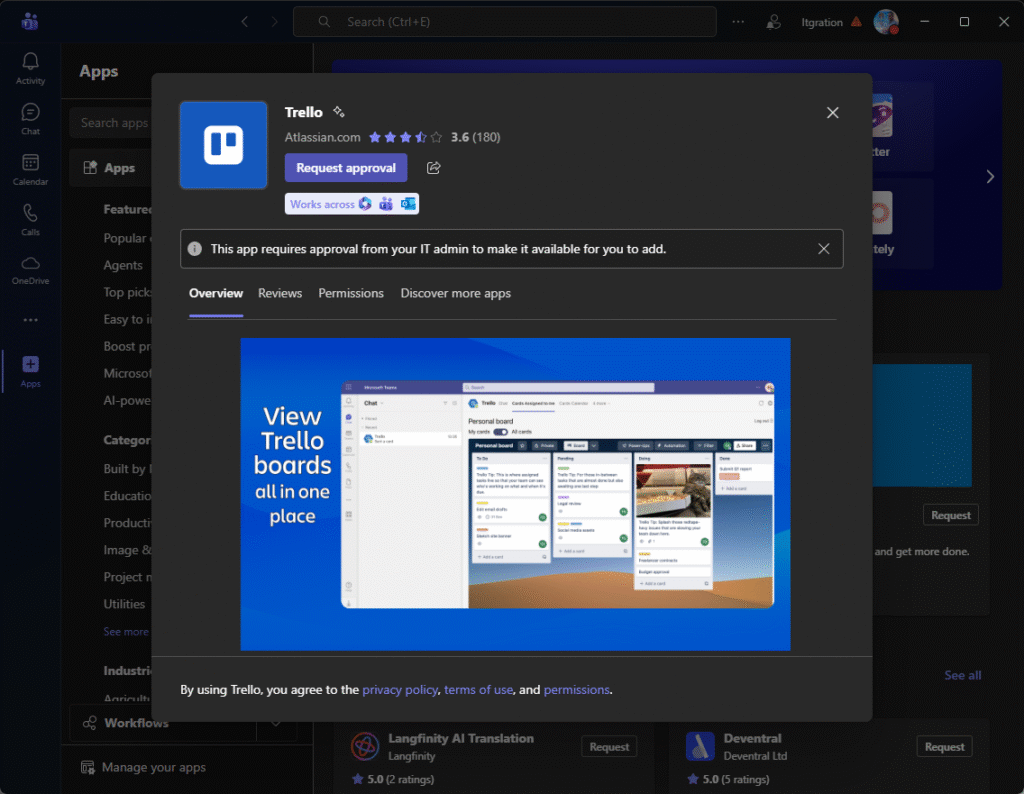
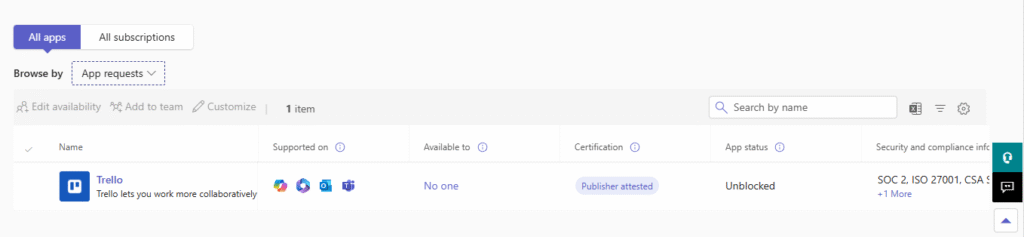
From an end-user perspective this is very friendly, instead of adding the App, the button changes to Request approval. In the teams admin Center the Administrator can then see the requested App and approve if necessary.
4. Summary
App store governance is a foundational control for any Microsoft 365 environment. Outlook, Teams, and Microsoft 365 Apps each have separate administration layers that together determine which integrations users can install. Ensuring those are properly configured reduces risk and creates a predictable, secure user experience.
With Microsoft introducing new experiences such as Microsoft 365 Copilot, maintaining strict control over integrated app availability becomes even more important. The next article in this series focuses on governing Copilot rollout and configuration, where governance settings, Intune app management, and the new Copilot Control System come into play.
1 thought on “Governing access to app stores in Microsoft 365 apps”