Introduction
Password managers have become a default convenience in modern browsers, including Microsoft Edge. Microsoft now recommends enabling the built-in password manager as part of the Edge Security Baseline, allowing credentials to roam securely across devices. However, in enterprise environments, this roaming capability may become a security concern, especially when users sign into Edge from unmanaged or personal devices.
This article explains how you can prevent Microsoft Edge from syncing passwords on unmanaged devices, using Conditional Access and the Edge Management Service. It also clarifies how policy precedence works when both Conditional Access and the Edge Policy Service are in use.
Understanding Edge Password Sync
What Microsoft Suggests
According to the official Microsoft Edge Enterprise Sync FAQ, Microsoft emphasizes that:
- All Edge sync data is encrypted in transit using TLS 1.2+ and encrypted at rest using AES128.
- Data for Entra ID (work or school) accounts is stored securely in Microsoft’s cloud, geographically located according to your tenant’s region.
- Applying Conditional Access and MAM (Mobile Application Management) policies to the Edge app will block sign-in entirely on unmanaged devices, not just disable sync.
Side note: This recommendation can only work on non-managed Windows devices and is therefore not a one-size-fits-all solution. Even though MAM for Windows is GA, there are still some caveats especially when device registration goes wrong on non-managed devices. Additionally, MAM for Windows is currently not available for macOS, which further limits its applicability in mixed-device environments. This recommendation should be seen as part of a broader, layered approach rather than a complete solution, since blocking sign-in affects all browser capabilities and may conflict with scenarios such as enabling Windows MAM, where browser sign-in is required for App Protection Policies to function.
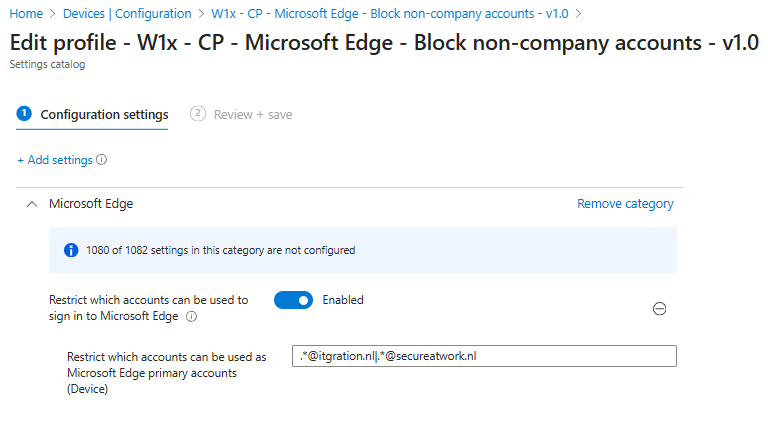
- You can limit which accounts can sign in to Microsoft Edge using the
RestrictSigninToPatternpolicy. For more information about what regular expression you can use see: Regular Expression 2 (re2.h) syntax
When a user signs into Microsoft Edge, passwords are stored and synced depending on the account type:
Microsoft Account (MSA):
- Passwords are stored in the Microsoft Password Vault.
- Synced across devices when Edge Sync is enabled.
- Managed via account.microsoft.com/passwords.
Work or School Account (Entra ID / Azure AD):
- Passwords are stored in Entra ID (cloud-only or hybrid).
- Sync is controlled by organizational policy.
Edge for Business vs Standard Edge: Sign-in Account Matters
When users sign into Microsoft Edge, the account type determines how the browser behaves and which enterprise policies apply:
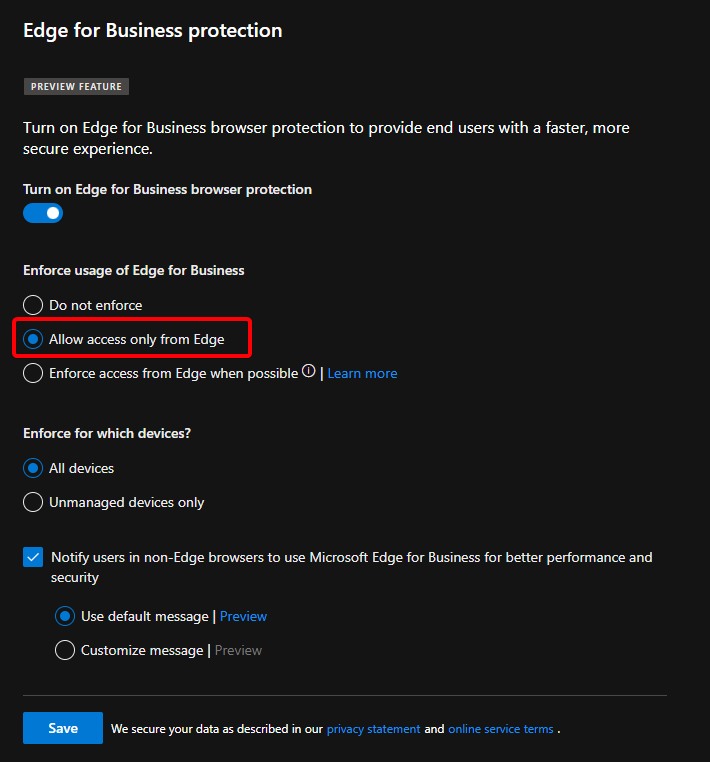
- Edge for Business is automatically activated when users sign in with their Entra ID (work or school) account. In this mode, enterprise management features are fully supported, including Group Policy, Conditional Access, and Edge Management Service controls. This mode ensures corporate data separation and provides a visual indicator that the session is work-related.
- Standard Edge (Personal Browser) is used when users sign in with a Microsoft Account (MSA). In this case, the browser behaves like a consumer instance of Edge. Enterprise policies from the Edge Management Service generally do not apply to this profile, and it does not receive business-mode protections.
According to Microsoft’s Edge for Business documentation and personal browser policies overview, only the work browser profile receives full policy enforcement. If users sign into Edge with an MSA on a managed device, they can unintentionally bypass enterprise settings—such as password manager restrictions or sync limitations since those policies won’t apply to personal profiles.
The key challenge: disabling the password manager does not remove already synced passwords. Existing credentials remain accessible on any device that previously had sync enabled.
Even when the password manager is disabled, any previously saved credentials remain retrievable on unmanaged Windows devices. In these cases, users can still access or export passwords that were previously synced to the Microsoft account or Edge profile. Therefore, simply disabling the password manager is not sufficient blocking Edge Sync through Conditional Access is the only effective method to ensure those credentials cannot roam or be retrieved from non-managed systems. This is for newly added passwords only, blocking sync after initial sync has taken place will not remove the passwords either.
Best practice: Use the RestrictSigninToPattern policy to prevent sign-in with personal accounts on corporate devices. This ensures the browser always operates in Edge for Business mode when users sign in.
Available Control Mechanisms
This section describes the different policy options available to control Microsoft Edge password sync and browser behavior across device types:
- Conditional Access (CA) policies for restricting Edge Sync access based on compliance or device state.
- Edge Management Service (Cloud Policy) for applying browser-level restrictions on unmanaged or BYOD devices.
Together, these mechanisms provide a layered enforcement model, ensuring coverage across both managed and unmanaged scenarios.
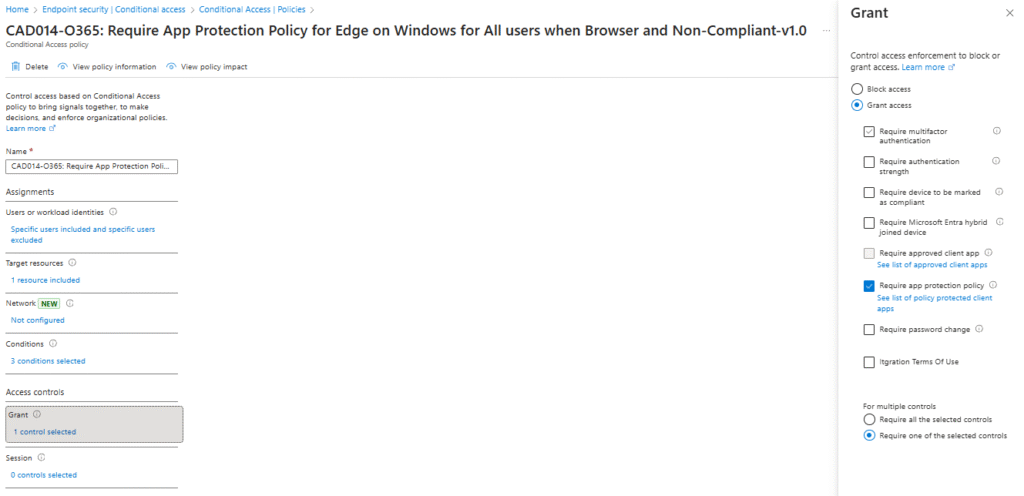
1. Restrict Edge Sync Using Conditional Access (CA)
When Conditional Access blocks Edge Sync on unmanaged devices, users can still sign in to Microsoft Edge, but synchronization—including favorites, passwords, and other browser data—will not occur. This ensures that no organizational data is synced from non-compliant devices, though it may impact user experience by preventing even benign data like favorites from synchronizing.
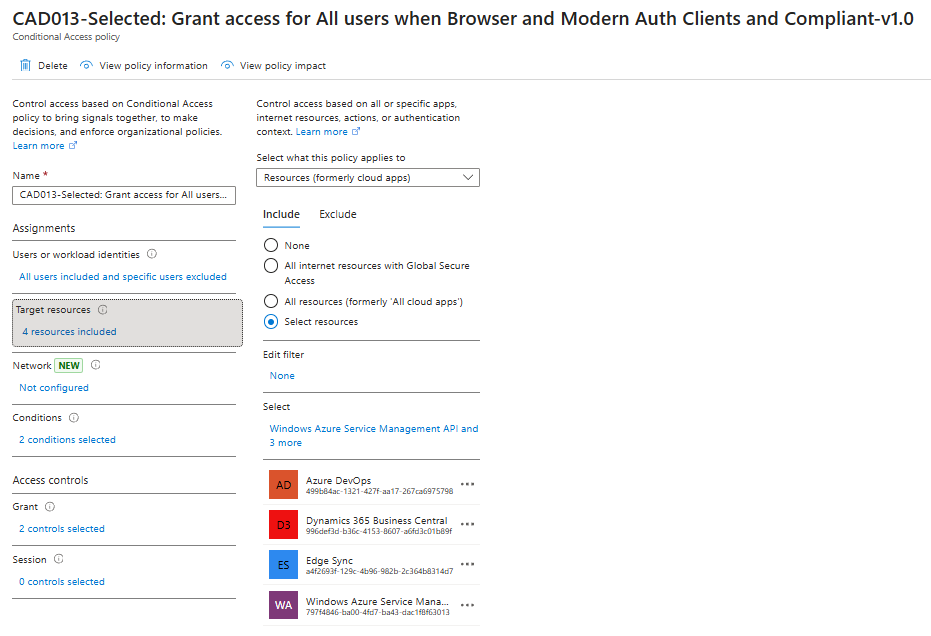
A stronger approach involves blocking Edge Sync entirely on unmanaged devices. This can be done using a Conditional Access policy, which targets the Edge Sync enterprise app. The app can be added to Entra ID using:
New-MgServicePrincipal -BodyParameter @{appId = "a4f2693f-129c-4b96-982b-2c364b8314d7"}
You can then create a Conditional Access policy that only allows Edge Sync when the device is compliant or hybrid Azure AD joined. This ensures password sync only occurs on managed devices.
2. Leverage the Edge Management Service for Unmanaged Devices
Note: Edge Cloud Policies (Edge Management Service) currently apply only to Windows desktop versions of Microsoft Edge. These policies do not apply to Microsoft Edge for mobile (iOS and Android), or macOS. Mobile and macOS devices must instead be managed through MDM/MAM or Intune app configuration settings.
For unmanaged devices (BYOD), you can use the Edge Management Service (available in the Microsoft 365 Admin Center) to deploy browser-level policies.
On Windows, you can also create an App Protection Policy (APP) to protect corporate data in the browser from leaking outside of Microsoft Edge. This includes using settings such as ‘Send org data to’, ‘Allow cut, copy, and paste for’, or disabling printing. These settings provide additional containment for organizational data within the browser environment, ensuring that sensitive content remains within managed applications and cannot be exfiltrated via standard OS or browser-level interactions.
This service enforces policies based on the signed-in Entra ID account rather than device enrollment, allowing you to:
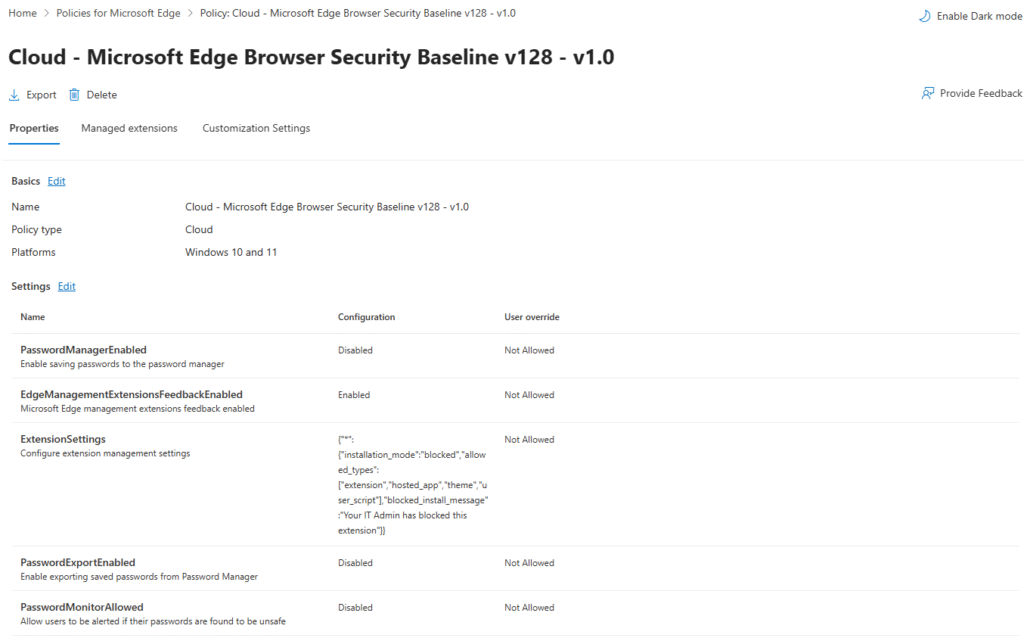
- Disable the password manager.
- Apply policies to signed-in corporate browser sessions (note: restricting sign-ins to corporate accounts only isn’t enforceable on unmanaged devices).
- Block sync on non-managed devices.
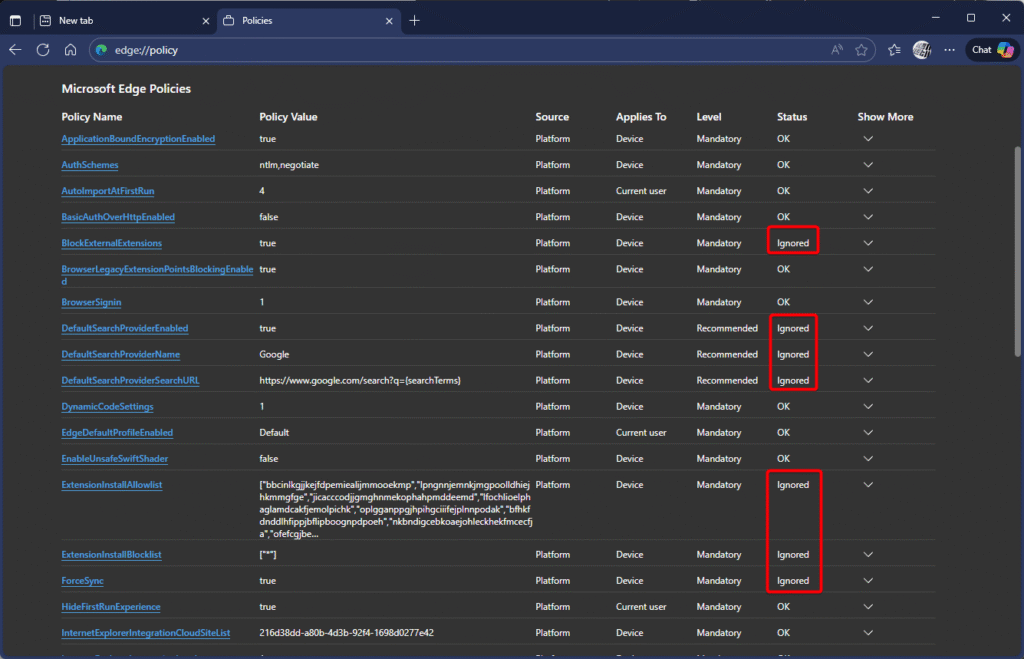
Administrators can also apply restrictions on which browser extensions can be installed or loaded within the signed-in corporate profile. Through the Edge Management Service, you can configure:
- Control which extensions are allowed or blocked (using the
ExtensionInstallBlocklistandExtensionInstallAllowlistpolicies). - Force-install specific security-related extensions, such as Microsoft Defender Browser Protection or compliance tools, via the
ExtensionInstallForcelistpolicy.
These measures help reduce exposure to malicious or unapproved extensions on unmanaged devices, ensuring that even limited control remains effective within the signed-in corporate profile.
Users receive these settings once they sign into Edge with their work account.
📘 Important: When applying Edge policies on unmanaged devices, these settings can only be enforced within the browser session where the user has signed in using their corporate credentials. If users sign into Edge using a personal Microsoft Account or another profile, those sessions will not inherit the organizational policies. The only way to enforce that users can access company data using a managed browser session is to enforce App Protection Policies.
Comparing the Available Options
To make it easier to choose the right approach, the following table summarizes the available options, their main characteristics, and their pros and cons:
| Option | Description | Pros | Cons |
|---|---|---|---|
| 1. Restrict Edge Sync via Conditional Access | Uses Conditional Access to only allow Edge Sync on compliant or hybrid Azure AD joined devices. | Strong enforcement; integrates with compliance posture; ideal for managed environments. | May break or complicate future scenarios like MAM for Windows or browser-based App Protection if not tested. |
| 2. Manage Edge via Edge Management Service | Applies browser-level policies to users on unmanaged/BYOD devices. | Extends control to unmanaged devices; no enrollment required; flexible deployment. | Limited precedence; not supported on macOS or mobile Edge; may not cover all device scenarios. |
Platform Limitations
Edge Cloud Policies are currently not available or functional on macOS. Administrators should rely on Intune configuration profiles or Conditional Access to enforce browser and data access policies in macOS environments which can then only be managed. This ensures that data leakage risks are minimized while maintaining consistent control across platforms.
macOS and Edge Cloud Policies
While Microsoft Edge is supported on macOS, testing confirms that the Edge Cloud Policies (Edge Management Service) do not function on macOS. Administrators should treat this as a known limitation.
As a mitigation, consider blocking Edge sign-in on unmanaged macOS devices using a custom Conditional Access policy targeting the Edge cloud resource to prevent data leakage through browser sync. Given that Edge Cloud Policies currently do not function on macOS, administrators should strongly consider blocking Edge sign-in on unmanaged macOS endpoints entirely. This ensures that no credentials, browsing data, or password-related information can sync from non-compliant macOS devices. Of course you can allow access to company data from the browser, but not with a signed-in user.
For reference, see Microsoft Edge policies documentation and Managing Edge for Mac (By Peter Klapwijk).
Summary
In summary: Preventing Edge password sync requires combining policy layers Conditional Access and Edge Cloud Policy to ensure protection across both managed and unmanaged devices.
Future Outlook
To effectively prevent password syncing in Microsoft Edge on unmanaged devices, organizations must adopt a layered approach where Conditional Access and Edge Cloud Policy are carefully configured to complement one another:
- Conditional Access ensures only compliant or hybrid Azure AD joined devices can use Edge Sync or sign into the browser with work accounts.
- Edge Cloud Policy (Edge Management Service) extends limited control to unmanaged Windows devices by enforcing browser-level restrictions within signed-in corporate profiles.
By aligning these layers, administrators can maintain a secure, consistent browser experience across both managed and unmanaged environments protecting credentials, minimizing data exposure, and maintaining a balance between productivity and control.
Hopefully in the future, we can get rid of passwords altogether. However, as we move toward passwordless authentication with passkeys, similar risks remain when those passkeys are not device-bound. If an attacker tricks a user into granting access to their keychain or synced credential store containing passkeys, the result could mirror today’s password-related compromises—demonstrating that secure storage and access control remain just as critical in a passwordless world.
With all the security capabilities being added to Microsoft Edge such as enterprise data separation, enhanced Conditional Access integration, and deep policy support it might also be time to reconsider whether allowing third-party browsers on managed systems still aligns with your organization’s security objectives. Standardizing on Edge can simplify policy enforcement, improve telemetry, and reduce exposure to unmanaged or noncompliant browser behavior. For a nuanced take on this topic, see Peter van der Woude’s blog post, which explains the implications of blocking other browsers and why administrators should balance user experience and manageability when enforcing such policies.
References
- Microsoft Edge management service overview
- Microsoft Edge enterprise sync FAQ
- Conditional Access for unmanaged devices
- Microsoft Edge security baselines
Thank you for this post. However, my goal is to achieve exactly the opposite. I already have a policy that requires a compliant device, but I want to exclude Edge Sync (AppId: a4f2693f-129c-4b96-982b-2c364b8314d7) in order to allow it. Unfortunately, excluding the Edge Sync enterprise app does not help here; in the sign-in log, I only see that “Microsoft Graph” is blocked. Is there perhaps another resource I can exclude so that the sync works?