Microsoft has quietly introduced the option to automatically block connections to unsanctioned cloud apps from the Microsoft Cloud App Security (MCAS) console. This is accomplished by integrating MCAS with Microsoft Defender Advanced Threat Protection (MDATP).
Based on the information available in Cloud App Security, the app’s domains are used to create domain indicators in the Microsoft Defender ATP portal. Within Windows Defender the Exploit Guard Network Policy option is used to block the access to the URLs. This will eventually result in the following notification sent to the user.
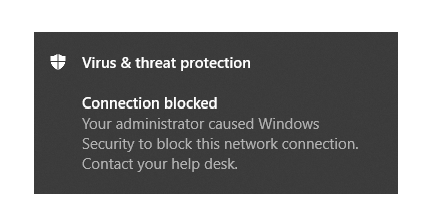
In this blog post I will explain how to setup this functionality when Microsoft Intune is used and what the behavior is within Windows 10. This assumes that you are licensed for both MCAS and MDATP, in my case by using a Microsoft365 E5 license.
- Setting up the necessary options in the Microsoft Defender Security Center
- Setting up a Device Configuration Policy to enable Exploit Guard Network filtering Microsoft Intune in audit mode
- Configuring Microsoft Cloud App Security (MCAS)
- Testing Network Filtering in audit mode on Windows 10
- Modifying the Device Configuration Policy to enable Network filtering
Setting up the necessary options in the Microsoft Defender Security Center
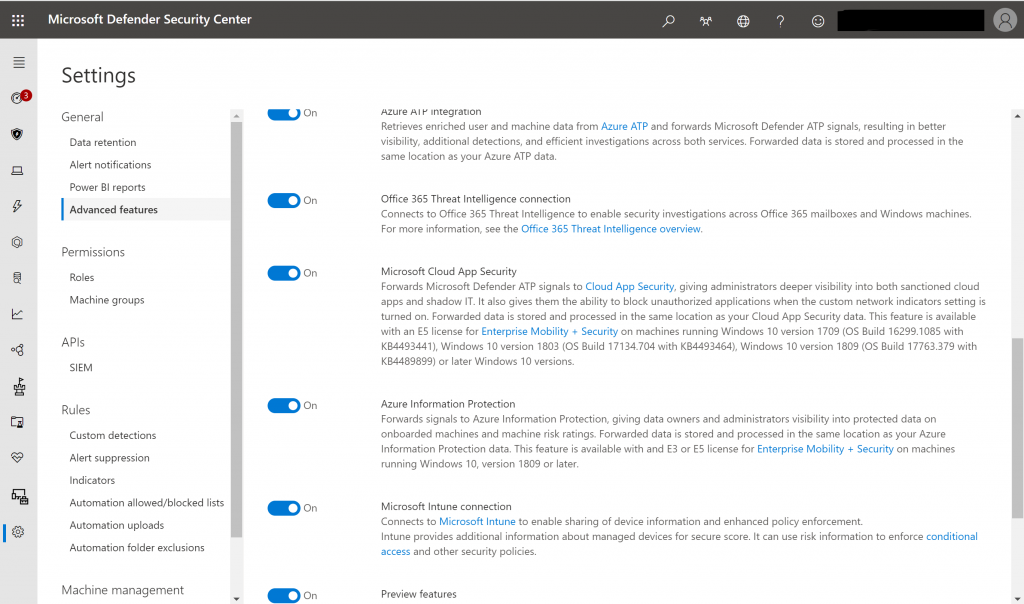
We have to start with setting up the connection between the Microsoft Defender Security Center and MCAS. This can be accomplished by turning the Microsoft Cloud App Security setting to “On” under Advanced features.
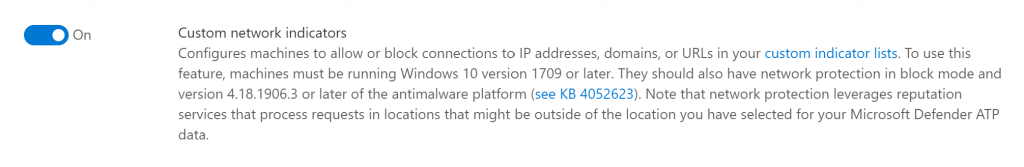
Next we need to enable the Custom network indicators as well, this setting can also be found under Advanced features.
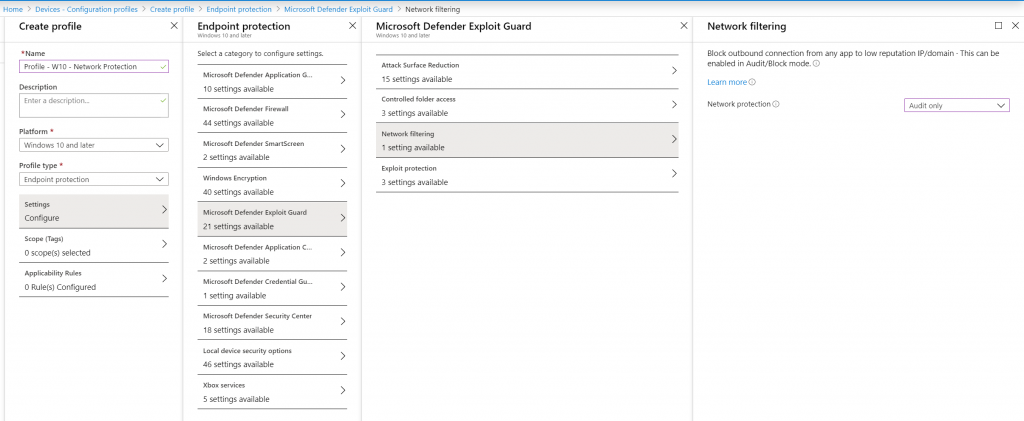
Setting up a Device Configuration Policy to enable Exploit Guard Network filtering Microsoft Intune in audit mode
In order to enable network filtering on our Windows 10 devices with MDATP configured, we are going to define a Device Configuration policy in Microsoft Intune which we will target to our Windows 10 Devices. We will do this in audit mode first and test the outcome on one of our Windows 10 machines.
Microsoft provides guidelines on how to enable this option using other products like ConfigMgr and Group Policy, this is described in the following article: Enable network protection
Configuring Microsoft Cloud App Security (MCAS)
The first thing we need to do is enable the Cloud app control option in MCAS, this can be done from the Cloud app control section under settings.
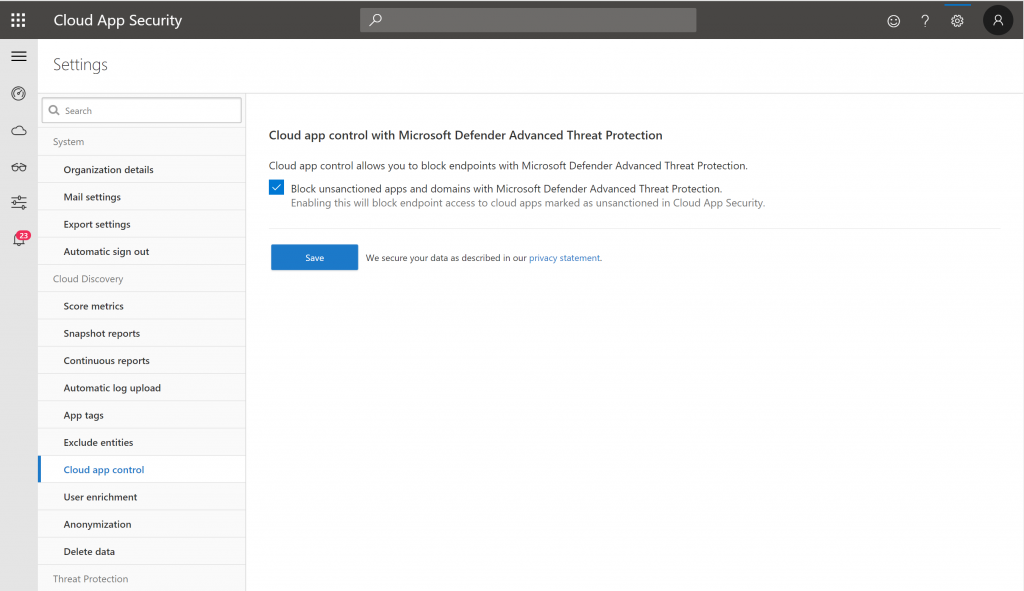
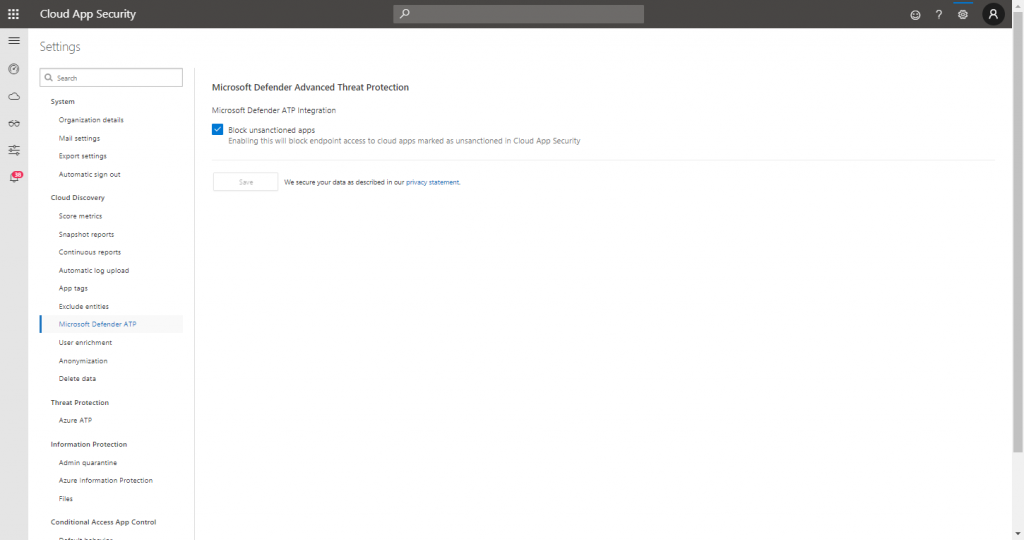
Edit April 2020: Cloud app Control is now called Microsoft Defender ATP, from here you have the option to enabled “Block unsanctioned apps”
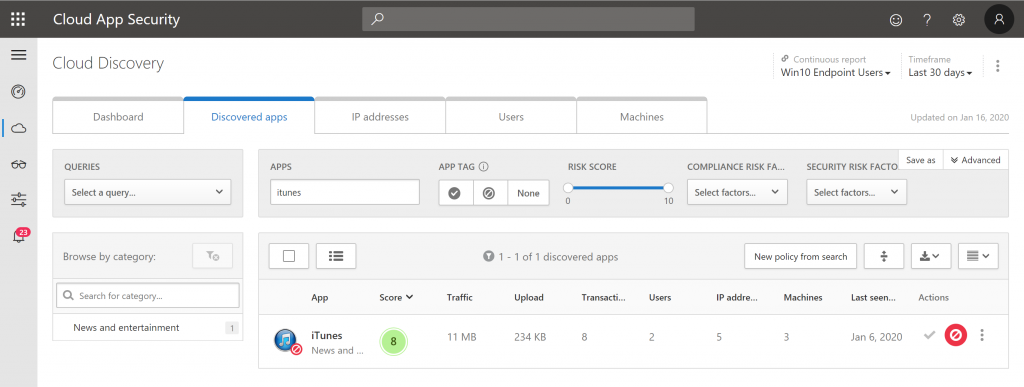
In our example we are going to block access to iTunes, the screenshot details that iTunes has been unsanctioned in our Cloud App Security portal.
Testing Network Filtering in audit mode on Windows 10
In order to start testing the network filtering in Windows 10, we first need to make sure that the Device configuration policy set in Microsoft Intune has landed on our test device. Once set, we can find the following entry in the Windows Defender eventlog.
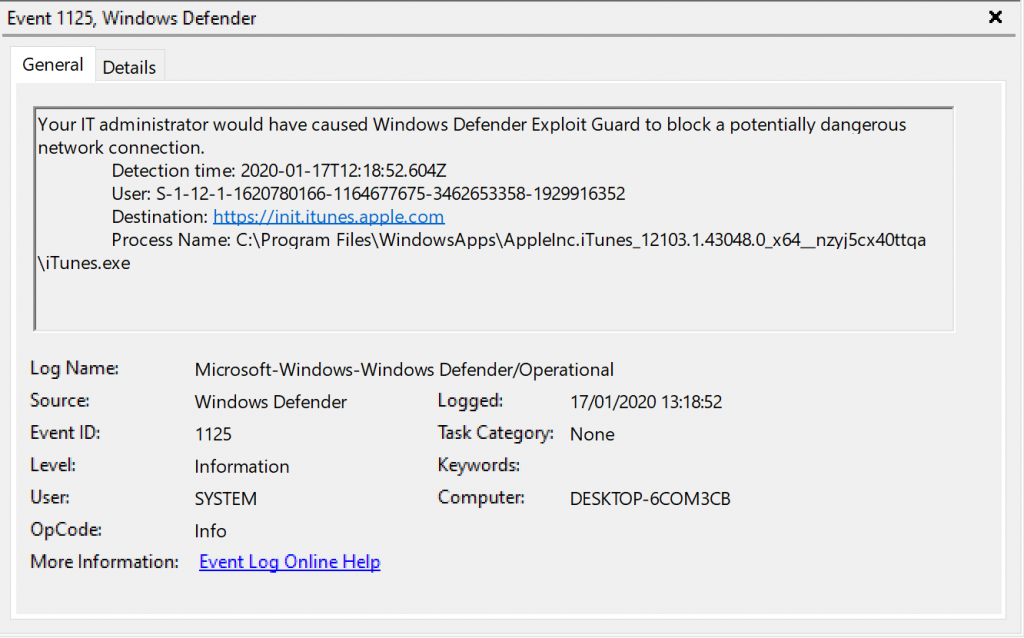
Once we start iTunes on our Windows 10 test device, we see EventID 1125 appear, detailing that the destination https://init.itunes.apple.com would have been blocked by the Network policy.
Modifying the Device Configuration Policy to enable Network filtering
Now that we tested the Network filtering policy in audit mode, we are ready to enable the Network protection by modifying our earlier created Device Configuration Policy.
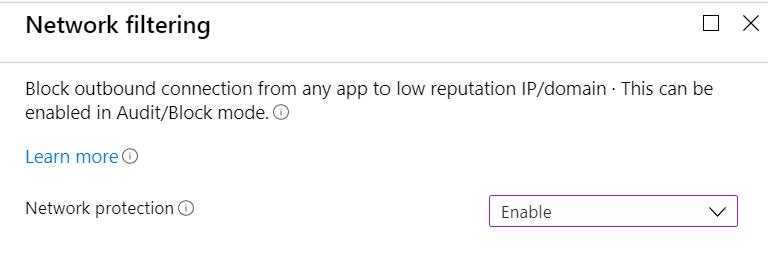
Network filtering behavior after Network protection is enabled
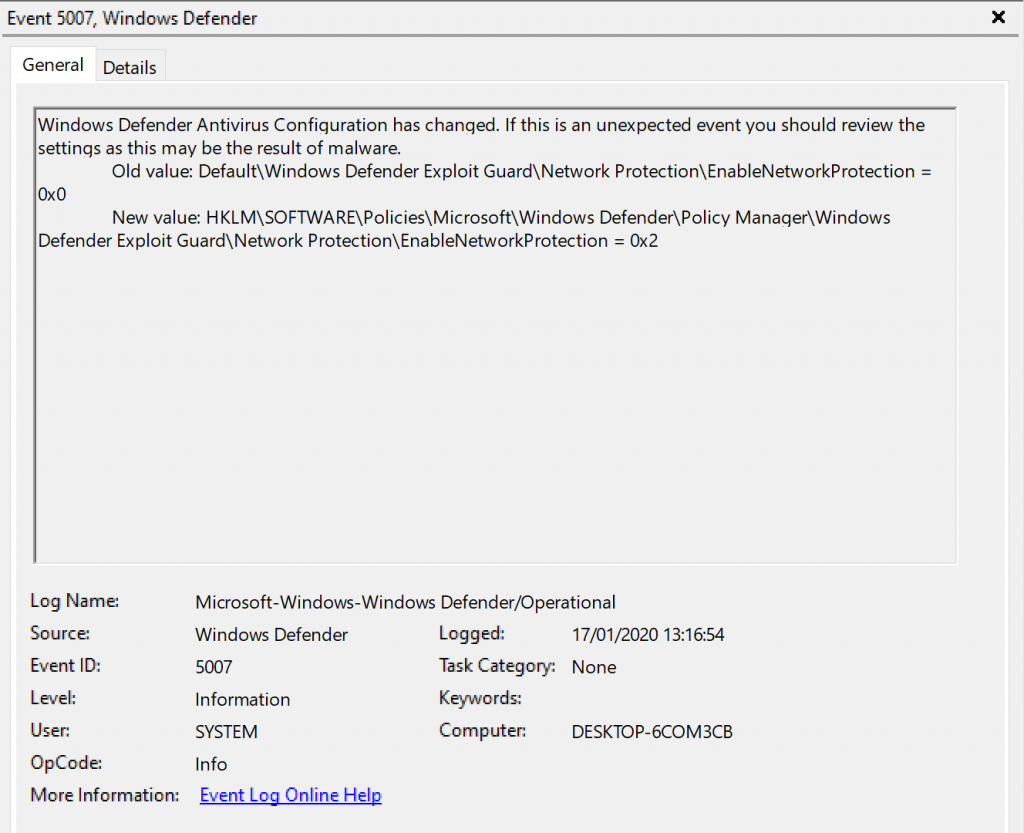
Once we modified the Device Configuration policy, it’s best to trigger a synchronization on our Windows 10 device so that the device configuration policy becomes active.
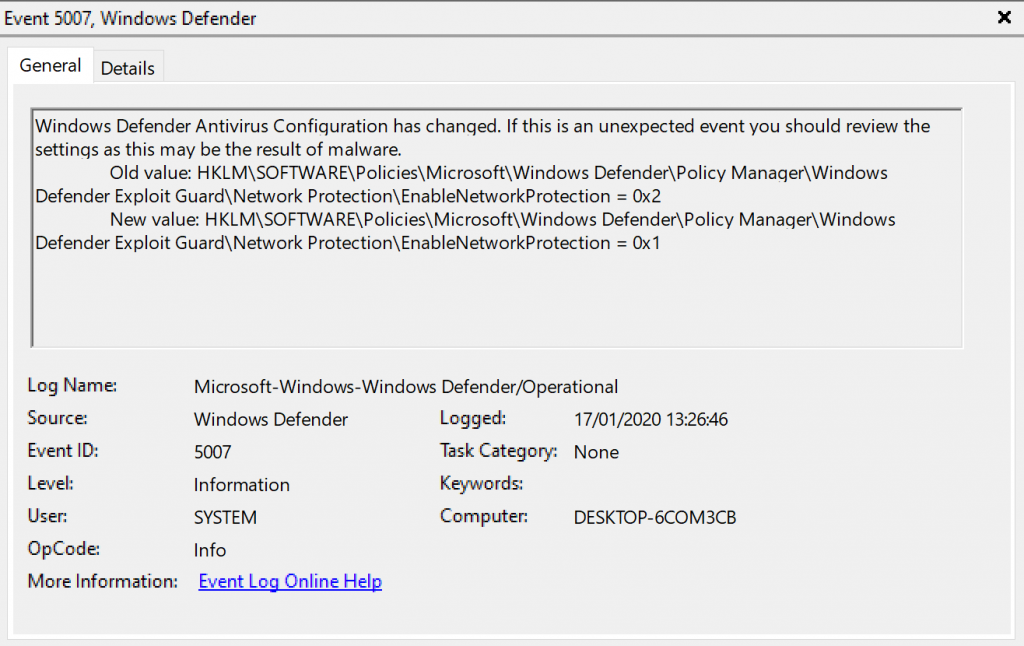
This will be reflected by EventID 5007 in the Windows Defender eventlog, detailing that Network
If we start iTunes now, we receive the following notification
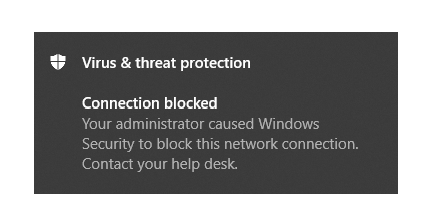
If you don’t receive a notification, it might be that you need to enable notifications first
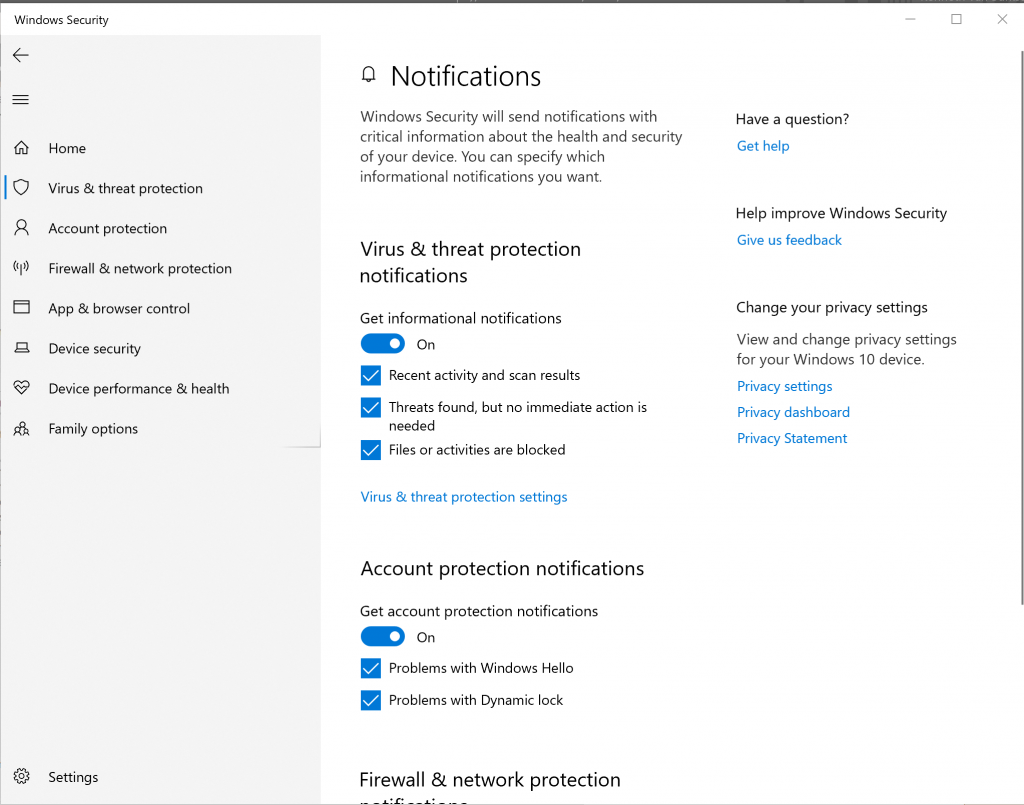
The corresponding entry in the Windows Defender eventlog is EventID 1126 now detailing that the network connection has been blocked.
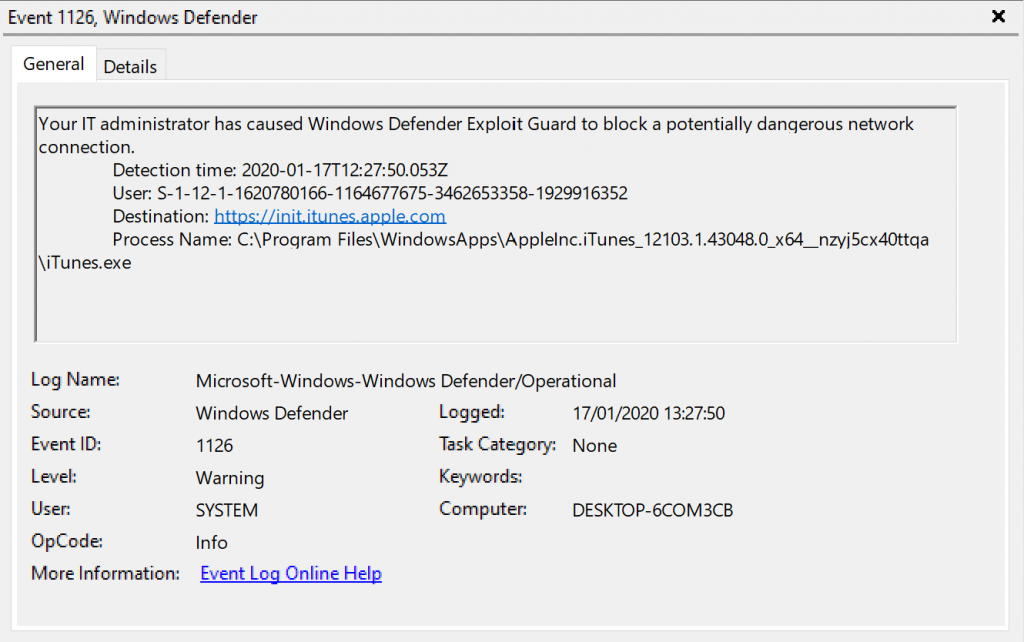
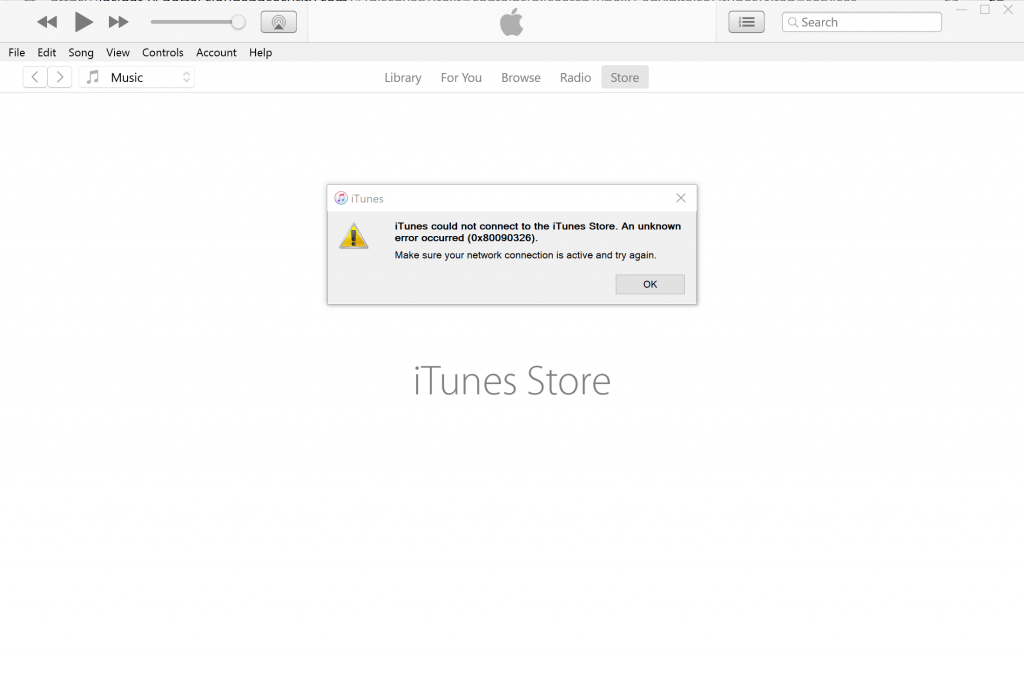
You will also notice that you’ll start receiving errors in the iTunes application itself, an example below:
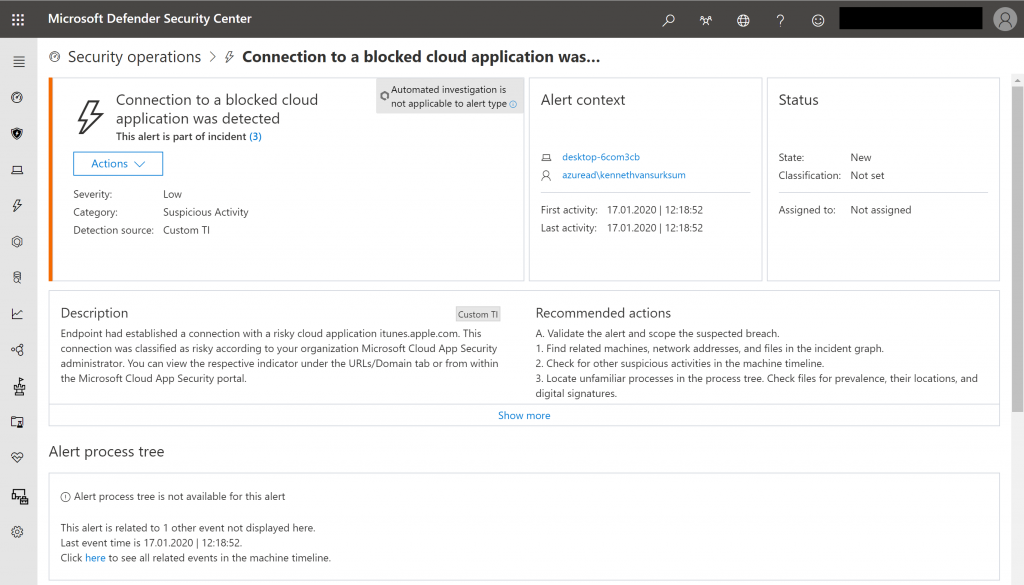
From the Microsoft Defender Security Center we can now see the following Alert appear which gives us central control about all our unsanctioned cloud apps.
Conclusion
Cloud app control is a very welcome addition to the MCAS portfolio, even though Microsoft provided integration with 3rd party solution in order to block network connections in the past, having a direct integration and being able to block cloud app usage directly from the MCAS portal is a really nice solution.
It would be nice though to also be able to block the actual execution of the application on the client as well, by being able to automatically create Applocker policies or configure Device Guard. Perhaps in the future, time will tell.
References
Microsoft Defender Advanced Threat Protection integration with Microsoft Cloud App Security – https://docs.microsoft.com/en-us/cloud-app-security/wdatp-integration
Sanctioning/unsanctioning an app – https://docs.microsoft.com/en-us/cloud-app-security/governance-discovery#BKMK_SanctionApp
Create indicators for IPs and URLs/domains (preview) – https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/manage-indicators#create-indicators-for-ips-and-urlsdomains-preview
Enable network protection – https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/enable-network-protection
Evaluate network protection – https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/evaluate-network-protection
Enable network protection in audit mode – https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/evaluate-network-protection#enable-network-protection-in-audit-mode
Windows 10 Device Guard Versus AppLocker – https://www.petri.com/windows-10-device-guard-versus-applocker
Greate article :hearteyes:. Unfortunatly i’m having mixed success with this 🙁
Running: Office E3 licenses, on prem domain joined Windows 10 – 2004 (19041.113) and Windows 10 – 1909 (18363.693) Machines are not Intune-managed.
App in question: Discordapp.com (Action in Cloud App Security: Unsanctioned-tag)
Cloud App Security and Microsoft Defender Security Center are integrated, and data flow between the two.
All things turned on under “Advanced features” in Microsoft Defender Security Center.
PowerShell: EnableNetworkProtection set to Enabled (1/Block mode)
Using Microsoft Edge (80.0.2361.66) visting discordapp.com gets the blocked message with Microsoft Defender SmartScreen.
Using any other browser, or running app on one of the two test computeres, things fly past Microsoft Defender.
Any thoughts on what I’m missing (or misunderstanding)?
Hi Peter,
I have no idea, I do see that you use another setup compared to mine.. what edition of Windows 10 are you running for example? (ENT or PRO?) – it must be related to something in that area i’m afraid.
Please let me know, hope I can help you out from there
/Kenneth
We integrated Defender ATP with Cloudapp Security and data is visible on the Cloud Discovery Dashboard. But within CAS/Settings no entry can be found to Cloud App Control!! Unsanctioning an app doesn’t seem to work. Within Defender ATP all settings are correct, incl Custom Network indicators. Network Filtering is in audit mode.
Do you have any idea why we can’t access Cloud App cControl within CAS?
Hi Marc,
The Cloud app Control section is now called Microsoft Defender ATP, from here you have the option to enabled “Block unsanctioned apps” – I modified the article to reflect this change.
Regards,
Kenneth
Hello Kenneth,
Thanks for your reply, but I also don’t have an entry called Microsoft Defender ATP. We’re using the latest version of Cloudapp Security.
Regards, Marc
Hi Marc,
What kind of License do you have? It must be license related then – For the functionality described in my blog posting a M365 E5 license was used.
Regards, Kenneth
Hello Kenneth,
We use E3-licenses combined with separate ATP and CAS-licenses. So it should be sufficient.
Regards Marc
Should be sufficient indeed – Did you enable the integration from the MDATP security center? And how long ago was that? If you followed my steps exactly, then you should probably log a call with Microsoft on this.
Sorry for not being able to help you out directly..
I will log a call with Microsoft. Thanks for your help.
Regards, Marc
Hi Marc,
Good luck – also please let me know the outcome !
/Kenneth