Organizations face increasing challenges in securing internet traffic and enforcing web access policies in today’s hybrid work environment. Two key tools from Microsoft, Microsoft Entra Internet Access (Global Secure Access) and Microsoft Defender for Endpoint (MDE), offer robust capabilities for managing security and productivity on the endpoint. This article provides an in-depth comparison between the web filtering and security functionality of these tools, highlighting their differences, features, and use cases to help IT professionals make better informed decisions.
Technical Differentiators in Microsoft Web Filtering and Security Solutions
Understanding the technical configurations and capabilities of Microsoft’s web filtering and security tools is essential for IT professionals. This article focuses on how Microsoft Entra Internet Access (Global Secure Access) and Defender for Endpoint address modern security challenges through advanced threat protection and policy enforcement mechanisms.
Table of Contents
- What is Microsoft Entra Internet Access (Global Secure Access)?
- What is Microsoft Defender for Endpoint (MDE) Web Content Filtering?
- Security Profiles vs. Filtering Policies in Global Secure Access
- Key Differences Between Global Secure Access and MDE
- Detailed Comparison: Security vs. Filtering
- Enforcing Continuous Protection: Key Considerations
- Integration Scenarios and Use Cases
- Summary
What is Microsoft Entra Internet Access (Global Secure Access)?
Microsoft Entra Internet Access (Global Secure Access) is a modern secure web gateway solution designed to enhance security and visibility over internet traffic. It provides robust threat protection, flexible web filtering policies, and network-level enforcement to secure all users and devices, whether on-site or remote.
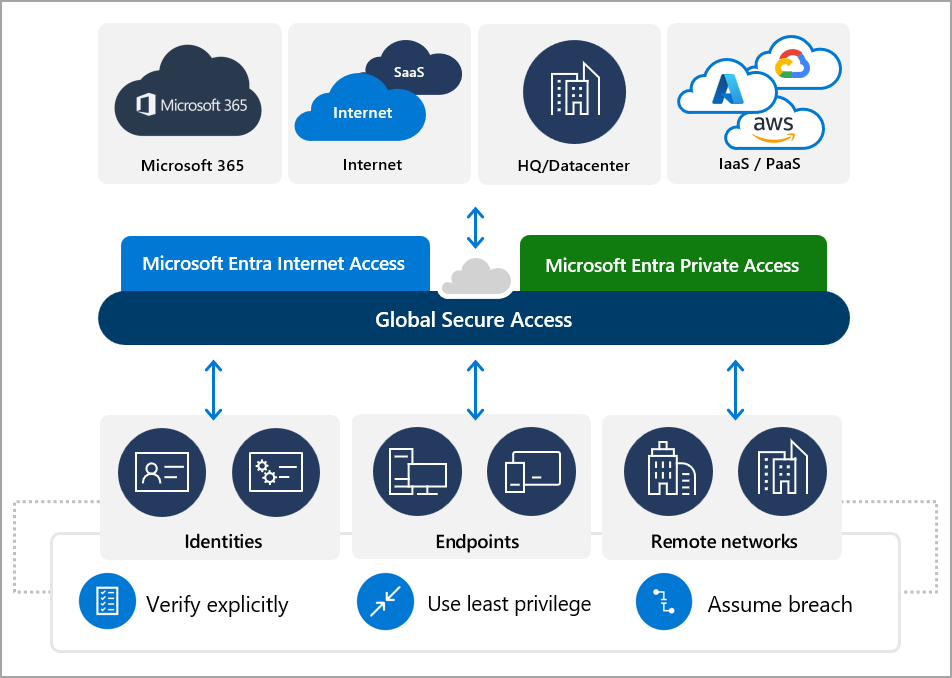
Key Features
- Threat Intelligence:
Leverages Microsoft’s global threat intelligence to block phishing, malware, and other malicious activities.Enforces security policies to restrict access to malicious or high-risk websites based on predefined categories. - Category-Based Web Filtering: Ensures compliance and productivity by restricting non-business-related content.
- TLS Inspection (In Development): Decrypts and inspects encrypted traffic for threats, ensuring comprehensive security.
- Cloud-Native Architecture: Scales effortlessly with hybrid and remote workforces.
- Integration with Microsoft 365: Seamlessly integrates with Microsoft 365 for a unified management experience.
Use Case
Ideal for organizations that need network-level security for diverse devices, including BYOD, IoT, and remote workers.
For more details, visit Microsoft Entra Internet Access Overview.
What is Microsoft Defender for Endpoint (MDE) Web Content Filtering?
Microsoft Defender for Endpoint (MDE) provides endpoint-based web content filtering among other functionality, focusing on protecting individual devices through policies tailored to specific user groups or scenarios. It is a key part of Microsoft’s comprehensive endpoint security stack.
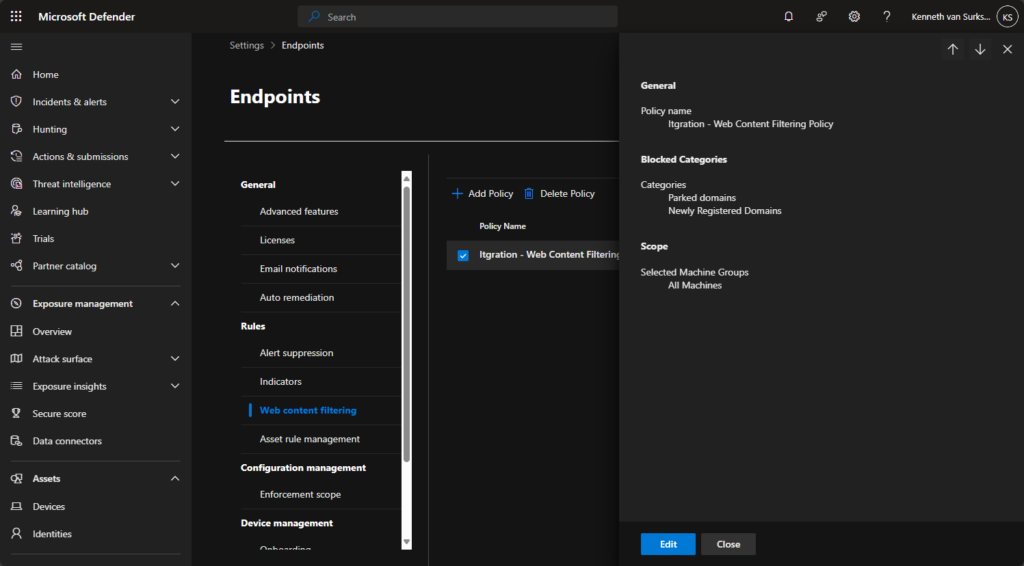
Key Features
- Category-Based Filtering: Blocks or allows specific web content categories, such as social media, gambling, and streaming.
- Offline Enforcement: Ensures protection and policy enforcement even when devices are disconnected from the corporate network.
- Network Protection: Uses Microsoft’s threat intelligence to block malicious domains in real time.
- Tamper Protection: Prevents unauthorized modifications to security configurations.
Use Case
Best suited for organizations looking to enforce acceptable use policies on managed and non-managed (through MDE management channel) devices, especially for remote work scenarios.
Learn more at Overview of Microsoft Defender for Endpoint Web Content Filtering.
Security Profiles vs. Filtering Policies in Global Secure Access
Security Profiles and Filtering Policies in Microsoft Entra Internet Access serve distinct but complementary purposes. Understanding their differences can help organizations effectively secure traffic and enforce web access policies:
Security Profiles
- Purpose: Focused on threat prevention by blocking access to malicious websites and high-risk categories.
- Key Features:
Leverages Microsoft Threat Intelligence to identify phishing sites, malware, and command-and-control (C2) servers.Protection policies based on category filtering.- Includes TLS Inspection (In development) to analyze encrypted traffic for threats.
- Applied at the network level, covering all devices (managed or unmanaged).
- Example Use Case: Ensuring that all users are protected from malicious activities, regardless of their location or device.
Filtering Policies
- Purpose: Enforces acceptable use policies by managing access to specific categories of web content.
- Key Features:
- Provides category-based filtering (e.g., social media, streaming, gambling).
- Supports custom allow/block lists to fine-tune access controls.
- Can target specific groups or users based on organizational needs.
- Example Use Case: Restricting access to non-work-related websites to maintain productivity during business hours.
Key Differences
| Aspect | Security Profiles | Filtering Policies |
| Focus | Threat prevention. | Acceptable use policy enforcement. |
| Driven By | Microsoft Threat Intelligence. | Admin-configured policies. |
| Scope | Network-wide for all devices and traffic. | Targeted for specific users or groups. |
| Customization | Predefined threat-based categories. | Fully customizable by administrators. |
For more information, visit Configure Entra Internet Access web content filtering.
A security profile can be selected in Conditional Access policies, and a Security profile can have one or more filtering policies attached to it.
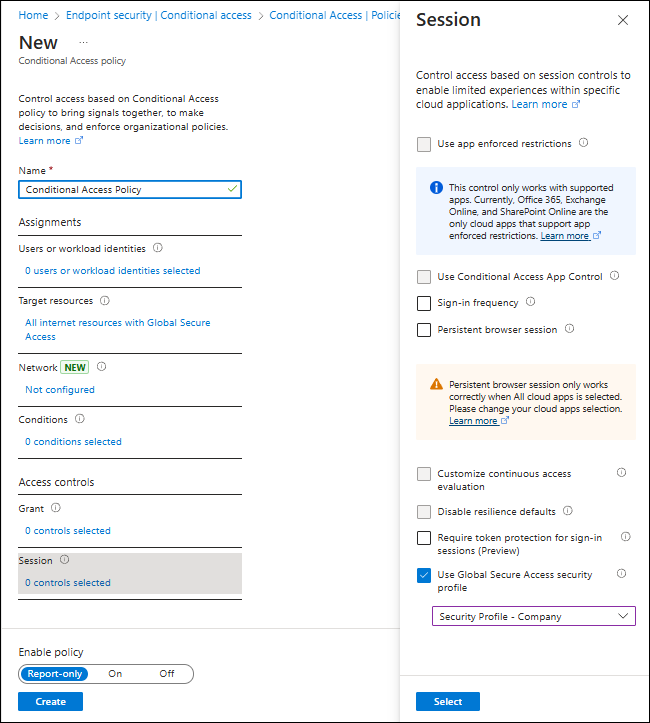
Key Differences Between Global Secure Access and MDE in Web Filtering and Security
| Aspect | Microsoft Entra Internet Access (Global Secure Access) | Microsoft Defender for Endpoint (MDE) |
| Primary Goal | Network-level security and web filtering. | Endpoint-level web filtering and threat protection. |
| Deployment | Cloud-based enforcement via a secure web gateway. | Policy enforcement through endpoint agents. |
| Scope | Protects all traffic, including connected unmanaged devices. | Limited to managed devices with Defender for Endpoint. |
| Threat Intelligence | Security Profiles enforce category-based protections but do not dynamically integrate with Microsoft’s Threat Intelligence. | Integrated with Microsoft’s global threat intelligence, differentiating it from GSA. |
| Traffic Inspection | Full TLS decryption and inspection.(In development) | Limited to endpoint-visible traffic. |
| Customization | Flexible network-wide policies. | User and device-specific policy enforcement. |
Detailed Comparison: Security vs. Filtering
Security Features
Microsoft Entra Internet Access (Global Secure Access)
- Enforces category-based protections.
- TLS inspection (In development) provides deeper analysis of encrypted traffic.
- Applies policies network-wide to all devices, whether managed or unmanaged.
Microsoft Defender for Endpoint (MDE)
- Includes Web Threat Protection to block malicious URLs.
- Offers Tamper Protection to secure endpoint configurations, ensuring policies are enforced even on unmanaged devices.
- Focuses on device-specific security, with real-time updates from Microsoft’s threat intelligence.
Web Filtering Features
Microsoft Entra Internet Access (Global Secure Access)
- Comprehensive category-based filtering for organizational compliance.
- Fully customizable allow/block lists for specific needs.
- Network-wide enforcement, ensuring consistency across all traffic.
Microsoft Defender for Endpoint (MDE)
- Tailored filtering options for managed devices.
- Ensures offline policy enforcement for productivity and security.
- Simple integration with Microsoft Endpoint Manager.
Even though web content filtering in Global Secure Access and web content filtering in Microsoft Defender for Endpoint offer similar functionality, their configuration settings are not on-par.
Some examples:
In Microsoft Entra Internet Access we have a category called Alcohol and Tobacco, which is not available in Microsoft Defender for Endpoint. Child Abuse images category is available in both products though. Therefore when using both products we have to be really thoughtful on where we want to block a certain category (on the endpoint or on the network level). Also the Parked domains and Newly Registered domains category option is missing in GSA while available in MDE.
From the GSA FAQ: Global Secure Access Frequently asked questions
What is the difference between Microsoft Entra Internet Access web categories and Microsoft Defender for Endpoint web categories?
Microsoft Entra Internet Access and Microsoft Defender for Endpoint both leverage similar categorization engines, with a few distinct differences. The Microsoft Entra Internet Access engine aims to provide a valid categorization of every endpoint on the internet, while Microsoft Defender for Endpoint supports a smaller list of site categories, focused on categories of sites that could introduce liability for the organization that operates the endpoint. This means that many sites are not categorized, and an organization wishing to allow or deny access must manually create a Network Indicator for the site.
Enforcing Continuous Protection: Key Considerations
Comparing Tamper Protection in MDE and Registry Settings for GSA Client
Microsoft Defender for Endpoint (MDE) provides Tamper Protection, a robust feature designed to prevent unauthorized changes to security configurations. This functionality offers several advantages:
- Global Enforcement: Tamper Protection can be enabled globally across all or selected devices within an organization using Intune or security.microsoft.com.
- Protection for Non-Managed Devices: Even unmanaged devices can enforce tamper protection when connected via the MDE security channel, ensuring that critical settings remain intact.
- Administrator Control: Tamper Protection ensures that even local administrators cannot override security configurations, providing a significant advantage over standard registry modifications.
Using Registry Modifications for the GSA Client
Allowing users to pause the GSA client undermines the enforcement of defined security and web access policies, as the client stops applying those protections when paused.
To ensure the GSA client cannot be paused by end users, administrators can modify the following registry keys:
- Restrict Non-Privileged Users:
- Registry Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Global Secure Access Client\RestrictNonPrivilegedUsers
- Value: Set to 1 to restrict non-administrator users from pausing or disabling the client.
- Hide Disable Private Access Button:
- Registry Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Global Secure Access Client\HideDisablePrivateAccessButton
- Value: Set to 1 to hide the ‘Disable Private Access’ button in the system tray menu.
These settings can disable certain functionality for normal users, but cannot be compared to tamper protection in Microsoft Defender for Endpoint.
Using Scripts to Deploy Registry Modifications for GSA Client
Since the GSA client does not natively support tamper protection, registry modifications must be distributed to prevent users from pausing the client. These changes can be deployed through Microsoft Intune using scripts, proactive remediations, or a Win32 app package.
Below is an example of a PowerShell script to enforce the required registry changes:
Example PowerShell Script
# Prevent non-privileged users from pausing or disabling the GSA client
New-ItemProperty -Path “HKLM:\SOFTWARE\Microsoft\Global Secure Access Client” -Name “RestrictNonPrivilegedUsers” -PropertyType DWORD -Value 1 -Force
# Hide the ‘Disable Private Access’ button in the GSA client menu
New-ItemProperty -Path “HKLM:\SOFTWARE\Microsoft\Global Secure Access Client” -Name “HideDisablePrivateAccessButton” -PropertyType DWORD -Value 1 -Force
Deploying the Script via Intune
- Create a PowerShell Script Profile in Intune:
- Navigate to Devices > Scripts > Add > Windows 10 and later > PowerShell.
- Upload the script and configure the execution settings (e.g., run as administrator).
- Assign the Script to Devices:
- Select the target user or device groups to apply the script.
Why Scripts Are Necessary
Unlike MDE’s Tamper Protection, GSA lacks a centralized method to prevent local administrators from overriding settings. These scripts or packages ensure that registry changes are enforced but remain vulnerable to modifications by administrators unless other measures (e.g., monitoring via proactive remediations) are implemented.
Practical Comparison Between MDE and GSA Client Enforcement
- MDE Tamper Protection: Fully integrated and requires minimal configuration to prevent users from disabling or modifying critical security settings. Tamper Protection also enforces security configurations even on non-managed devices, ensuring consistent protection.
- GSA Client Registry Modifications: Offers more granular control but requires custom configurations via registry changes or Intune custom profiles. This approach provides flexibility but allows local administrators to potentially override settings.
Integration Scenarios and Use Cases
When to Use Microsoft Entra Internet Access
- Best for securing hybrid and remote work environments with BYOD or IoT devices.
- Organizations needing centralized, network-level policy enforcement.
- Enterprises adopting a Zero Trust model.
When to Use Microsoft Defender for Endpoint
- Ideal for enforcing AUPs on managed devices.
- Organizations requiring offline device protection.
- Businesses using Microsoft’s endpoint management stack.
Combining Global Secure Access and MDE
For maximum security, organizations can combine the strengths of both solutions:
- Global Secure Access: Secures all network traffic at the gateway level.
- MDE: Protects endpoints with granular policies and offline capabilities.
Summary
Microsoft Entra Internet Access (Global Secure Access) and Microsoft Defender for Endpoint (MDE) are complementary tools that provide comprehensive protection for today’s hybrid workforces:
- Use Global Secure Access for network-wide security and compliance.
- Use MDE for endpoint-specific policy enforcement and threat protection.
By leveraging both solutions and configuring them appropriately, organizations can implement a layered security approach that aligns with Zero Trust principles, securing devices, users, and traffic across their entire environment.
Thank you for the insightful article! I recently implemented global secure access in my lab a few weeks ago, and I find the subscription price to be quite competitive compared to Zscaler. While it’s still a work in progress, I’m optimistic that Microsoft will continue to invest in its development. One feature I appreciate that would work on asap is a friendly block page that explains why certain platforms, like personal email or social media sites, are restricted. Additionally, the Universal tenant restrictions are a valuable feature set, restrictling access to other tenants emails or resources such as sharepoint, owa, etc
Greetings Kenneth. Thank you for the post. I agree that there is overlap between MDE and Entra Internet Access. I’m a bit confused with the Microsoft Threat Intelligence powered aspects of Entra Internet Access you mention. I know that under Global Secure Access > Secure, there are headings for both “Security profiles” and “Web content filtering policies”. Aren’t Security profiles just collections of Web content filtering policies? https://learn.microsoft.com/en-us/entra/global-secure-access/concept-internet-access#security-profiles
I’m aware that Microsoft currently has a partnership with Netskope (in preview) that does all the threat intelligence powered stuff, but I wasn’t aware that this was included out of the box by Microsoft.
Can you point me to some docs that explain this?
P.S. Many of the links to MS Docs in your post go to 404. Are you able to update them?
Hi Greg,
Thanks for your comment, and after research I came to the conclusion that your are totally right. Within the Security Profiles of GSA there is no integration with Threat Intelligence (hopefully “Yet”) – I updated the article to reflect this, the documentation is very vague about this and contains some hints to protecting against threats but no mention of TI integration – I also updated the links to working URLs.
Thanks for doing this analysis, I recently asked some people at MSFT some questions about this topic and did not get very satisfactory answers :). the link above for “For more information, visit Configure Entra Internet Access web content filtering” is still broken.
Have attempted to evaluate how the blocking features of MDCA compare to GSA and MDE?