By default, on Windows 10 devices which are Azure AD joined, the user performing the join is added to the Local Administrator group. Besides the user and the local administrator (which is disabled by default), two other SIDs are added without any friendly name which explain who they are. So where are those SIDs coming from?
It is possible to make the user a normal user while enrolling the device, but then you have to create a Deployment Profile and use Windows Autopilot. See: Configure Autopilot profiles or use Bulk enrollment. See: Bulk enrollment for Windows devices
Note: This post reflects the status of Azure AD local administrative privileges as of February 11th 2020. Functionality may change, even right after this post has been published.
When searching through the documentation (How to manage the local administrators group on Azure AD joined devices) you will read that these 2 SIDs represent the Azure AD Global Administrator and the Device Administrator roles.
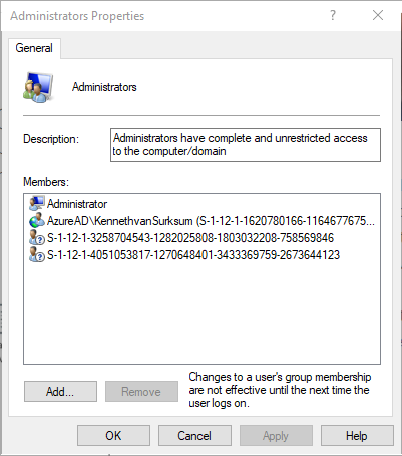
So basically this is really handy, you can add a user in the Azure AD role and therefore the user becomes a local administrator on the Azure AD joined devices. These a global settings, meaning that if you receive the device administrator role, you will be a local administrator on all Azure AD joined devices for your tenant.
When searching for the Device Administrator role under “Roles and Administrators” in the Azure AD portal you will notice that the Device Administrator role isn’t available.
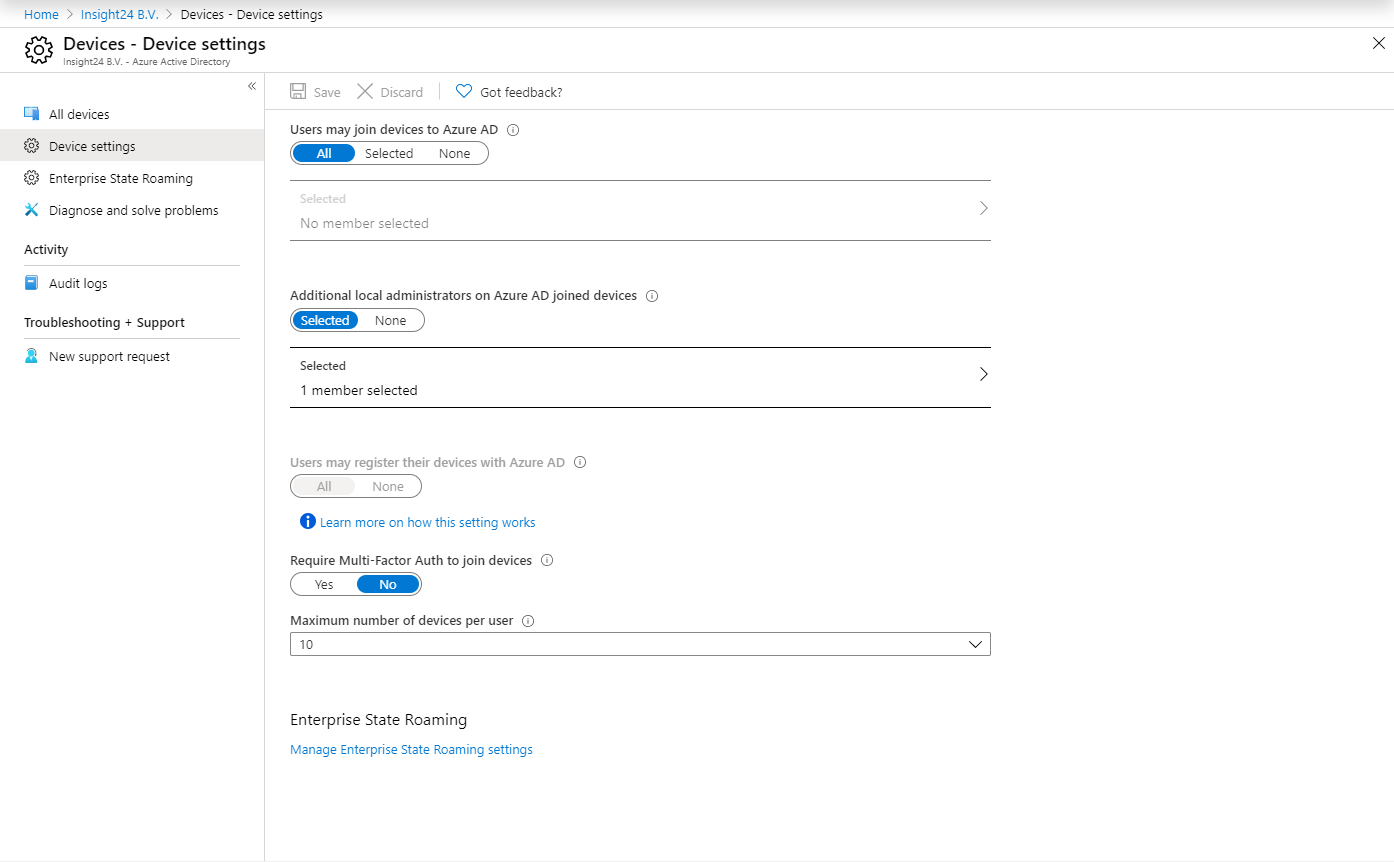
Adding device administrators is done in a different way, you’ll need to go to “Devices -> Device Settings” where you will find the option “Additional local administrators on Azure AD joined devices”. When you add a member to this option, it will receive the Device Administrators role.
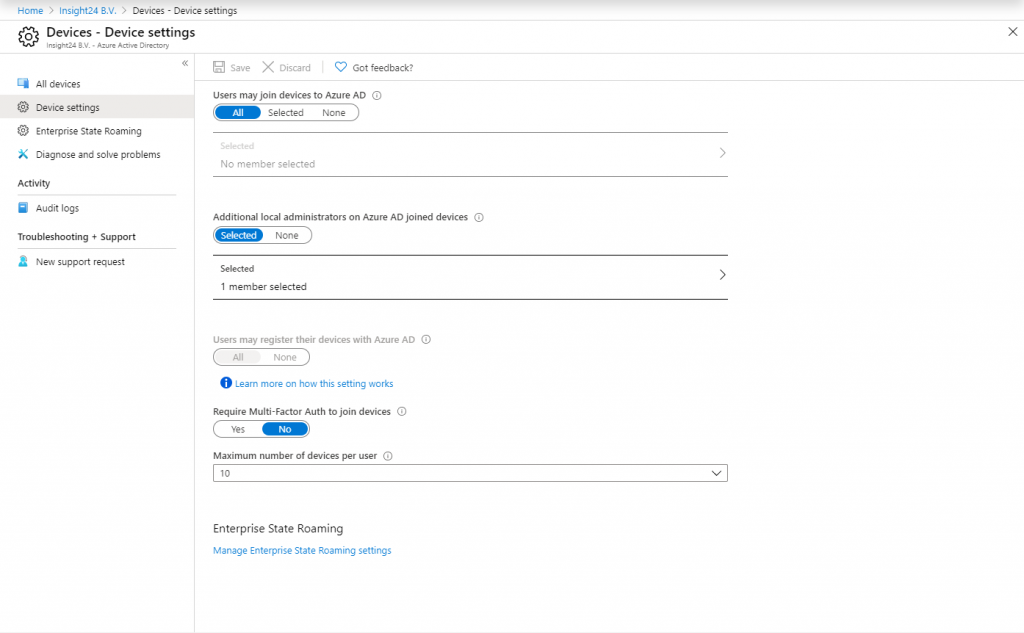
Note that being able to add local administrators on the Azure AD joined devices is a Azure AD premium feature.
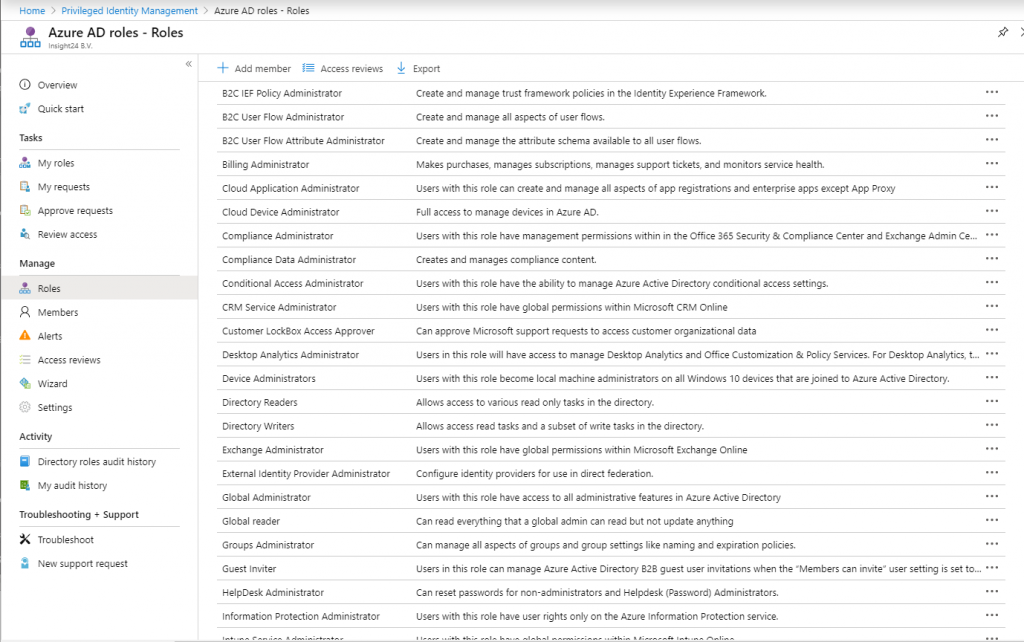
The Device Administrator role is available within Azure AD Privileged Identity Management (PIM), so when using PIM you can assign the role from there as well and make users either permanent members or eligible.
Challenges
Based on what is possible out of the box, from a security perspective this poses some challenges. For example, do you really want to login to another device using “Global Administrator” rights, you never know what software is running on the system (keyloggers or any other tool which can harvest credentials). If your Global Administrator account is compromised this can be considered a major security issue. Same goes for permanent Device Administrators, if their account is compromised you can basically access every Azure AD joined machine using those credentials.
There are also some challenges with the Device Administrator group, mainly because when you add a user to this role (either via the Azure AD settings or by activating the role using PIM) the change is not effective immediately on the Windows 10 client. The reason for this has to do with the PRT, which stands for Primary Refresh Token.
From the documentation:
A Primary Refresh Token (PRT) is a key artifact of Azure AD authentication on Windows 10, iOS, and Android devices. It is a JSON Web Token (JWT) specially issued to Microsoft first party token brokers to enable single sign-on (SSO) across the applications used on those devices. The CloudAP plugin renews the PRT every 4 hours during Windows sign in.
Basically this means that after a user is added to the Device admins group it can take up to 4 hours for this to be active, and vice versa (when user is removed from Device admins it stays local admin for up to 4 hours).
So what are the other options you have,
Make Me Admin is a simple, open-source application for Windows that allows standard user accounts to be elevated to administrator-level, on a temporary basis.
You could configure Make Me Admin in such a way that you either allow end-users to temporarily give them local administrator rights while you help remotely. Or start Make Me Admin with Runas for your own account and specify that account as eligible for elevation using one of the many settings (not tested)
Thanks Erik Loef for making me aware of this solution.
This solution, created by John Seerden provides a way to maintain passwords for locally created accounts. You could for example create a local account, and have the password managed by Serverless LAPS. The main point here is not to create a local account, with a common password on all of your Azure AD Joined machines. If that account gets compromised then the attacker has access to all of your Azure AD machines. (the whole reason why Microsoft created the Local Administrator Password Solution in the first place). See: Create a local user account via Windows 10 MDM by Peter van der Woude
Use another management agents besides Intune.
There are some other Management Agents which provide solutions which can temporarily create local accounts with administrative credentials. Once the necessary work by the workplace administrator on the machine is done the management tooling removes the created account.
Michael Mardahl pointed me to a solution he build to manage the administrators group using an Azure AD Security Group and some PowerShell magic. Worthwhile to check this one out.
Oliver Kieselbach pointed me to two interesting solutions mentioned below
Intune Local Administrator Password Solution (iLAPS) by Alex Ø. T. Hansen
Another solution to manage the Local Administrator password in a similar way
LAPS for Azure AD and Hybrid Joined by Synergix
Synergix provides a free community edition called Secrets Vault, they also have an Enterprise paid edition available providing way more functionality.
Centero Carillon for Access Right Management.
Centero has a nice solution for local admin rights available. When a user needs admin rights he/she can simply request them giving a justification. This process even works if the user is not online. Central reporting is provided for admins to view the requests.
Conclusion
Microsoft still has a lot of work to do when it comes to visibility into who is local admin on Azure AD joined machines, also extending PIM to also include accounts on Azure AD joined clients would be a welcome addition. Users could then temporarily request local administrator/power user rights and this would be effective immediately if approved.
If you have found other solutions to these challenges please reach out, I will include your solution in this blogpost with credits 🙂
Hi Kenneth,
as a free solutions I also know this one:
http://blog.tofte-it.dk/powershell-intune-local-administrator-password-solution-ilaps/
and for Edu and non profit I know in addition this one:
https://www.synergix.com/products/secrets-vault/features/laps-for-azure-ad/
best,
Oliver
Synergix Secrets Vault Community Edition is now FREE FOR ALL !!!
https://www.synergix.com/products/secrets-vault/editions
Higher Edition supports ..
– Multiple Local Account Password Management
– Rotation of Logon Name with rotation of passwords
– Windows 7.0 SP1, Windows 8.x, Windows 10
– Windows Server 2008/R2, 2012/R2, 2016, 2019
– Azure AD Joined Windows 10
– On Prem AD Joined Windows 7.0 SP1 to Windows Server 2019
– Workgroup Computers
– Azure AD Domain Service Joined computers
– UNIX
– MacOS
Plus
Audit capabilities
Security Event Forwarding
and Hardware + Software Information that help you perform deep analysis when performing an investigation.
and more coming in future releases ( new release every quarter ! )
Hi, Kenneth,
Thanks for great article and inspiration.
I have no clue of what I am doing wrong but I cant get the Device Administrators role to work. I tried everything and searched everywhere. The users will log in fine but does not have local admin rights. I tried on multitple tenants. Any idea what i am missing here?
Just for facts:
– AAD P1
– Tried with or without license
– Local groups are in place on the machine
– GA accounts works fine
Hi Guus,
When propagating users into the Device Administrator group, it can take a while for this to become effective. This has to do with the PRT, which refreshes every 4 hours. (so it can take up to 4 hours max)
Did you take this into account while testing?
Hope this helps,
Regards,
Kenneth
Yes definitely. I have been working on this for a few days already. it is breaking my head lol. Also because I cannot find anybody else on the internet experiencing the same issue.
The MS article is pretty straight forward: https://docs.microsoft.com/en-us/azure/active-directory/devices/assign-local-admin
I really don’t see what I miss here. I tried giving the local admin user that i created for this role extra admin rights and a license as well just to see if thats the missing part but no luck still..
Guus,
Strange indeed.
Are Global Administrators admin on the device? – can you verify if the correct groups are provisioned locally on the device? It should work, since I have tested it several times.. my experience though is that it can take some time for newly added device administrators to become active.
Please share your findings, and reach out if I can help.
/Kenneth
Hi kenneth,
Thanks a lot for your quick reply’s.
Yes both SIDs (like mentioned in your blog) are in place on the local machine(s) and GA account acts like local admin on the machine when logging in.
Do you assign licences to your local admin account(s)? I guess you use a dedicated account for this? thats the way I would like it to work so that our support desk staff can use it to troubleshoot remotely without the need of the GA account.
Also do you assign any other admin roles to the user? Now it only has the Device Administrators role assigned..but tried to include the intune admin role on top to try if that works..
Any updates on this Guus?
Still no luck..I tried giving the user a full M365Business license and additional admin roles to see if my problem is in that area. I will take a last resort action and submit a ticket with MS support today..keep you posted!
Under the Administrators Properties, make sure that the SID at the bottom is the actual SID for the “Device Administrator” role in your tenancy. In my case, it wasn’t. I had to create a powershell script to change it to the correct SID and things started working as expected.
If it’s the first time you login and you already have Azure Ad device admin role then there are no issues. The challenge is if you have already logged in without Azure Ad device admin, then was added to the role, then you need to wait for 4hr PRT refresh and re-logon.
Hi, I’m having an issue where some devices (eg “Computer A”) my admin account (member of AADJDLA role) can elevate a process yet on other devices (eg “Computer B”) it can’t “The requested operation requires elevation”. By enabling privileged use auditing I found that on Computer B, after attempting to elevate there is a “Group membership information” ID4627 event and I can clearly see that my admin account is not a member of the AADJLA group/SID/role. I can’t figure out why this is inconsistent and why these devices don’t evaluate this membership.