This week, the European SharePoint Conference (ESPC) is held between November 27 – 30 in Amsterdam the Netherlands. The event which will attract thousands of visitors and will feature more than 140 amazing speakers on a diverse set of topics related to Microsoft 365. At this event, I have the pleasure of speaking about Microsoft…
Microsoft Intune Application Deployment Best Practices
In December 2012, I blogged about best practices for deploying applications using System Center Configuration Manager, and while many of those recommendations are still valid I thought it was worthwhile to update my recommendations for today’s world, deploying applications using Microsoft Intune. My Modern Workplace Application Vision Source: A framework for Windows endpoint management transformation…
Speaking at the Workplace Ninja Summit, September 27-29 2023
Starting on Wednesday September 27, till Friday September 29 the Workplace Ninja Summit which is an in-person event will take place in Baden, Switserland. This event is organized by the diverse Workplace Ninja User Groups throughout the world which provide delegates helping to organize this 3 day event. The event will have more than 100,…
Speaking at the Cloud Identity Summit 2023, on September 7th 2023
On Thursday September 7th, the annual Cloud Identity Summit will take place as an in-person event in Koblenz Germany. This event is organized by Thomas Naunheim, Gregory Reimling and René Wasel, you can find more information about them here. At this event, I will be speaking about Microsoft Entra Id/Azure AD Conditional Access in my…
Azure AD Conditional Access authentication context now also available for Azure AD Privileged Identity Management
Microsoft has extended the capabilities of Azure AD authentication context to Azure AD Privileged Identity Management (PIM). By doing this we can trigger a Conditional Access policy to be executed at the moment someone elevates their role using Azure AD PIM. This functionality is now in preview. In June 2021 I already provided a first…
December 2022 update of the conditional access demystified whitepaper and workflow cheat sheet.
I’m proud to announce the December 2022 update of my Conditional Access demystified whitepaper. With this release, we have reached the fifth iteration of the whitepaper and accompanying files. I released the first version in in August 2019 after writing several blogposts on the subject. In May last year I released the second version containing…
Conditional Access public preview functionality reviewed (22H2) – Part 3: Granular control for external user types
In the last couple of months, Microsoft released new functionality for Azure AD Conditional Access. All of this functionality is still in public preview, so please read the following article on what to expect from Preview functionality: Preview Terms Of Use | Microsoft Azure In these series of articles I will go through the following…
Conditional Access public preview functionality reviewed (22H2) – Part 2: Conditional Access filters for Apps and Workload Identities
In the last couple of months, Microsoft released new functionality for Azure AD Conditional Access. All of this functionality is still in public preview, so please read the following article on what to expect from Preview functionality: Preview Terms Of Use | Microsoft Azure In these series of articles I will go through the following…
Conditional Access public preview functionality reviewed (22H2) – Part 1: Authentication Strength
In the last couple of months, Microsoft released new functionality for Azure AD Conditional Access. All of this functionality is still in public preview, so please read the following article on what to expect from Preview functionality: Preview Terms Of Use | Microsoft Azure In these series of articles I will go through the following…
Speaking about Mobile Application Management at the AppManagEvent 2022 on October 7 in Utrecht
On October 7, 2022 the AppManagEvent will be organized in the Media Plaza, Jaarbeurs Utrecht. The AppManagEvent is an initiative from PDS b.v. in the Netherlands. For 2022, the themes are Deployment, Security, Application Virtualization, MSIX, Win10/11/365 management, Identity Management, IT Infra and much more. At this event, I will be speaking together with my…
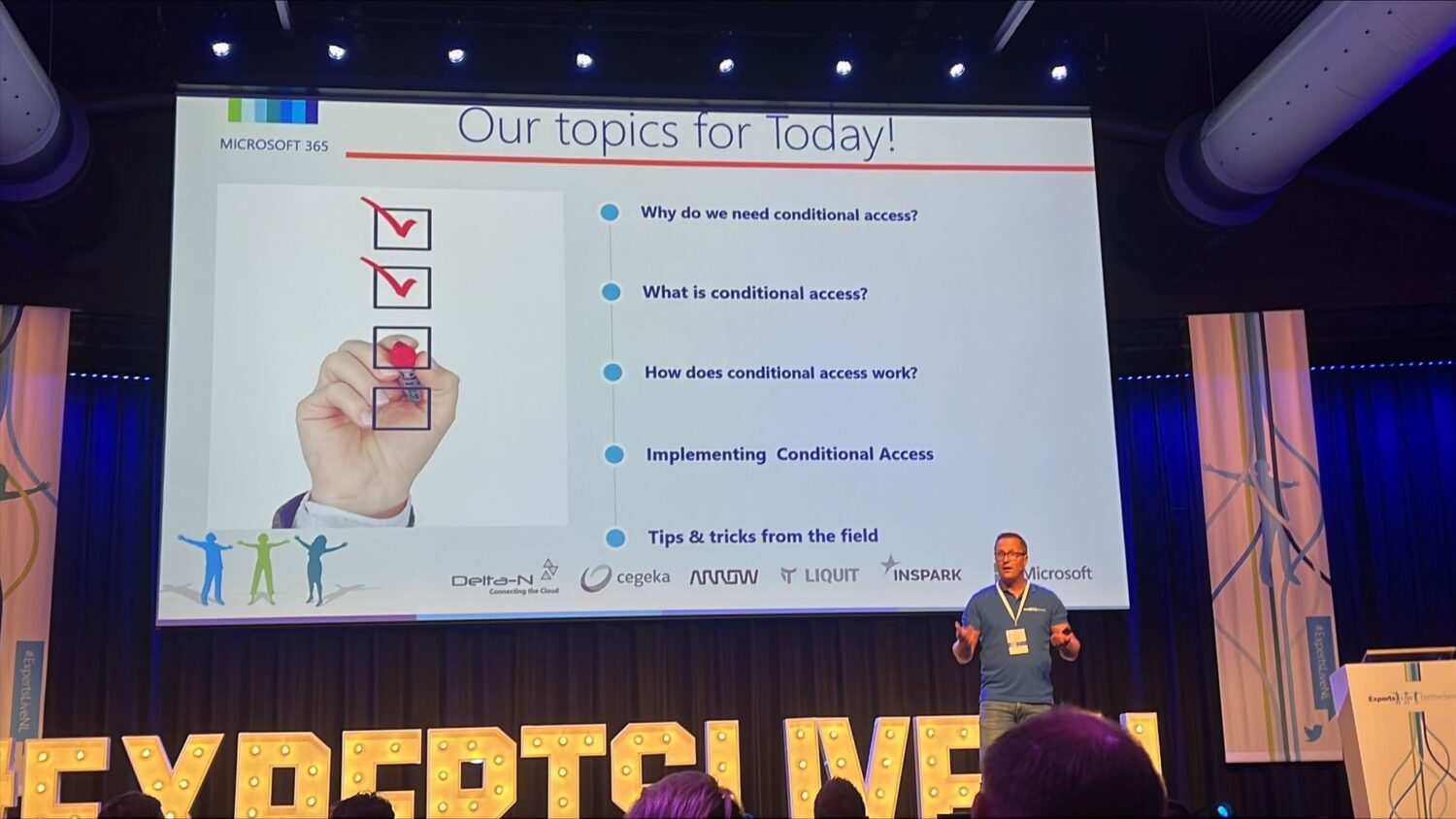
Speaking about Conditional Access at Experts Live Netherlands 2022 on September 30 in Den Bosch
Besides helping organizing Experts Live NL 2022 in my role as speaker manager together with Erik Loef, I’m also happy to announce that I will be speaking at this amazing event as well. My session will be about: Azure AD Conditional Access Demystified, a topic on which I already presented before and written some extensive…
Speaking about Conditional Access at the Workplace Ninja Summit 2022 on September 12th in Luzern Switzerland
After speaking virtually on the Workplace Ninja Summit 2020 and Workplace Ninja Summit 2021, I’m really proud to announce that I will also speak the Workplace Ninja Summit 2021, and this time it’s an in-person event. The Workplace Ninja Summit 2022, is an in-person event held from September 12th till September 14 in Luzern Switzerland….
Speaking about Mobile Application Management at the Techorama Belgium 2022 event
On Wednesday, May 25, 2022, I will be speaking together with Peter Daalmans at the Techorama Belgium event. Techorama 2022 will be an in-person conference taking place in Antwerp 24-25 (pre-con on May 23) in Kinepolis Antwerp. Techorama will offer its usual combination of great speakers, an unforgettable conference experience and 3 days of deep-dive…
Speaking about implementing Microsoft Endpoint Manager for Operations and Mobile Application Management at the Microsoft 365 Virtual Marathon 2022 event
On Friday, May 6th 2022, I will be speaking at the Microsoft 365 Virtual Marathon 2022 event. Microsoft 365 Virtual Marathon is a free, online, 60-hour event happening May 4-6, 2022. Featuring great speakers from around the globe. This event is free for all wanting to attend. The event starts at 9:00 am on Wednesday…
Apple Business Manager device import options for later use within Microsoft Endpoint Manager
This blogpost is a continuation of two earlier blogposts about integrating Apple Business Manager with Azure Active Directory and Apple Business Manager. The first blogpost written was about Setting up Apple Business Manager for use with Azure Active Directory and covered the steps to request access to Apple Business Manager, and how to setup and…